Flexible Deployment Options with Invicti Scan Agents
Executive Summary
This document demonstrates how decentralized Invicti deployments with internal scanning agents can provide consistent vulnerability scanning results with centralized visibility in a wide variety of environments. By decoupling the scanning engine from the management and reporting systems, you can deploy Invicti’s industry-leading dynamic application security testing (DAST) to match your application development infrastructure and integrate it into existing workflows. Highlights from this technical white paper include:
- The challenges of ensuring consistent and accurate vulnerability scanning and enforcing web security policies in distributed and highly dynamic application environments.
- How Invicti Enterprise uses scan agents to combine distributed vulnerability scanning with centralized security management.
- The benefits of deploying Invicti with scan agents, such as maximized security testing coverage, centralized visibility, improved operating efficiency, and automatic scaling.
- Typical use cases and deployment scenarios with network diagrams, including a multinational setup and containerized web services in the cloud.
The Challenges
Ensuring consistent web application security testing across multiple environments, deployments, and locations poses a major technological challenge for businesses worldwide. Every organization is different and one-size-fits-all solutions inevitably require trade-offs between coverage, effectiveness, and workflow efficiency. While the ultimate goal is the same – to measurably improve web application security – the sheer variety of application deployment architectures leaves organizations struggling to get tangible results.
Securing Distributed Application Environments
To be effective at scale, security solutions and workflows need to be automated as much as possible. The growing complexity and scale of web application environments combined with a rapidly changing cybersecurity landscape means that code-level (static) security testing is not enough to prevent vulnerabilities. Organizations have come to realize that automated dynamic testing is a mandatory part of any web application security program, but implementing scanning effectively in complex environments is not an easy task. What’s more, scanning is just the beginning. To improve security, you need to get accurate and timely vulnerability information to your developers so they can fix the issues. You also need centralized visibility across the entire security workflow, no matter how complex the underlying infrastructure.
For large application environments with hundreds of web assets spread across multiple sites, handling vulnerability scanning and management manually is simply not effective. To complicate the picture even more, what if some of the application environments you want to scan are internal and not accessible from the Internet, perhaps for compliance reasons? What if they reside in separate networks or even different physical locations across the world? How do you ensure that all assets are scanned on a regular basis and vulnerabilities are fixed before they can be exploited by attackers? How can you centrally manage security across distributed teams? How do you keep track of all the security workflows so you know if you’re making progress?
Keeping Pace with Change and Growth
Compounding the problem is the fact that web application environments are highly dynamic. New sites and applications appear on what seems a daily basis, high-profile applications are under constant development, and new technologies are readily brought on board to keep ahead of the competition. Because it has become so easy to spin up a new website or expand an existing one, many organizations don’t know exactly what web assets they have and what they need to secure.
Software architecture is changing, too. Monolithic applications are now a rare sight outside legacy environments and organizations increasingly favor service-oriented designs, with software commonly split up into dozens or even hundreds of microservices. Coupled with the flexibility and convenience of cloud computing and virtualization, this results in web application environments made up of ever-changing collections of containerized web services that are spun up and torn down depending on current business needs and workloads.
Facing this moving and ever-expanding target are small security teams that don’t have the resources or technical capabilities to manually keep up with all the changes and centrally manage security. If you have a dozen geographical locations with separate web application development programs, staying in control of all the changes becomes exponentially more difficult. When you also need to scale security to match the pace of business growth while still maintaining visibility of the overall security posture, it is clear that conventional approaches are not going to work.
The Solution: Invicti Scan Agents
To address these challenges across the huge variety of deployment models and use cases, web application
security solutions need to be highly configurable and support a variety of deployment models. This allows organizations to smoothly incorporate security into their existing environments and workflows to ensure consistency and central visibility.
Invicti Enterprise has a modular architecture that offers extremely flexible deployment options, from a fire-and-forget, all-cloud on-demand deployment to advanced on-premises setups across isolated internal networks. With this model, you can take advantage of Invicti’s industry-leading vulnerability detection and management features in a way that best suits your infrastructure and business requirements.
Vulnerability scanning with Invicti is based on the idea of decoupling the scan process from the central server by using scan agents to run scans and report results back to the server. For maximum flexibility, you can deploy scan agents in any target environment – on-premise (on Windows and Linux, but also wherever a Docker image can be deployed), in the cloud, and in any hybrid configurations in between. The goal of deploying Invicti Enterprise with a customized scan agent setup is to decentralize scanning and align it with the application environment while still reaping the benefits of centralized scan and vulnerability management.
The Benefits
By matching the deployment model of the web application security solution to your specific environment, you can take full advantage of Invicti’s workflow integration and optimization capabilities. After setting up scan agents and automation, a small security team can easily manage thousands of assets across multiple locations and add agents as necessary to seamlessly scale scanning without additional manual configuration. Combined with Invicti’s extensive internal API, this also opens the way to fully automated security testing integration in custom environments.
With multiple scan agents, you can divide and conquer application security challenges by maximizing coverage and making full use of Invicti’s proprietary Proof-Based Scanning™ technology. This translates to rapid security improvements with minimized communication overhead, shorter time-to-fix, and automated fix retesting across all web application environments.
Centralized Vulnerability Scanning and Management
Results from multiple Invicti scan agents can be combined in a single easy-to-use management interface for full visibility and control over web application security across any number of environments. Crucially, this is possible regardless of the internal deployment architecture and organizational structure. After all, a large organization can have dozens of development teams, each with its own unique tasks, capabilities, and needs. Without centralized web application security management, there is no way to define and apply security policies, enforce SLAs or identify opportunities for improvement.
Centralized management is especially challenging across local environments. While organizations worldwide continue moving to the cloud, there are still many situations where data and applications must reside on local systems, for example due to compliance concerns. By deploying Invicti scan agents in each environment, you can scan internal applications and manage vulnerabilities from a central interface just like in an all-cloud setup. Combined with automation and API integration, this provides a unique solution to detect vulnerabilities and maintain web application security across multiple logical and physical locations, no matter if you are using Invicti via the user interface or integrating its scanning capabilities into your own management systems.
Automatic Scaling in the Cloud
For cloud-based deployments on Amazon Web Services, you can use Invicti scan agents to improve scalability and performance. If you set a Invicti scan agent to cloud mode and enable automatic scaling in the cloud, a new cloud agent will be automatically created every time a scan is launched and automatically destroyed when the scan ends. This eliminates the need to manually configure additional agents as scanning needs grow – when a new website, web service or application environment instance goes live, you can automatically fire up one or more agents to test it.
The ability to spin up scan agents on demand is especially important in containerized environments where the number and type of services and applications that are running at any given time may vary depending on the current workload. Agent scalability extends scan automation to ensure scanning coverage across the entire web application environment currently in use. This provides a realistic view of the current web security posture and, if necessary, allows you to reduce scanning time by using multiple agents to scan many environments in parallel.
Selected Deployment Scenarios
To ensure that all users can integrate industry-leading vulnerability scanning capabilities into their environments, Invicti has been developed with flexibility in mind. Depending on their individual needs, organizations can use any combination of built-in and custom integrations and management capabilities to launch scans and collect results. Here are just a few Invicti Enterprise deployment scenarios that use scan agents to maximize effectiveness and coverage.
The Multinational
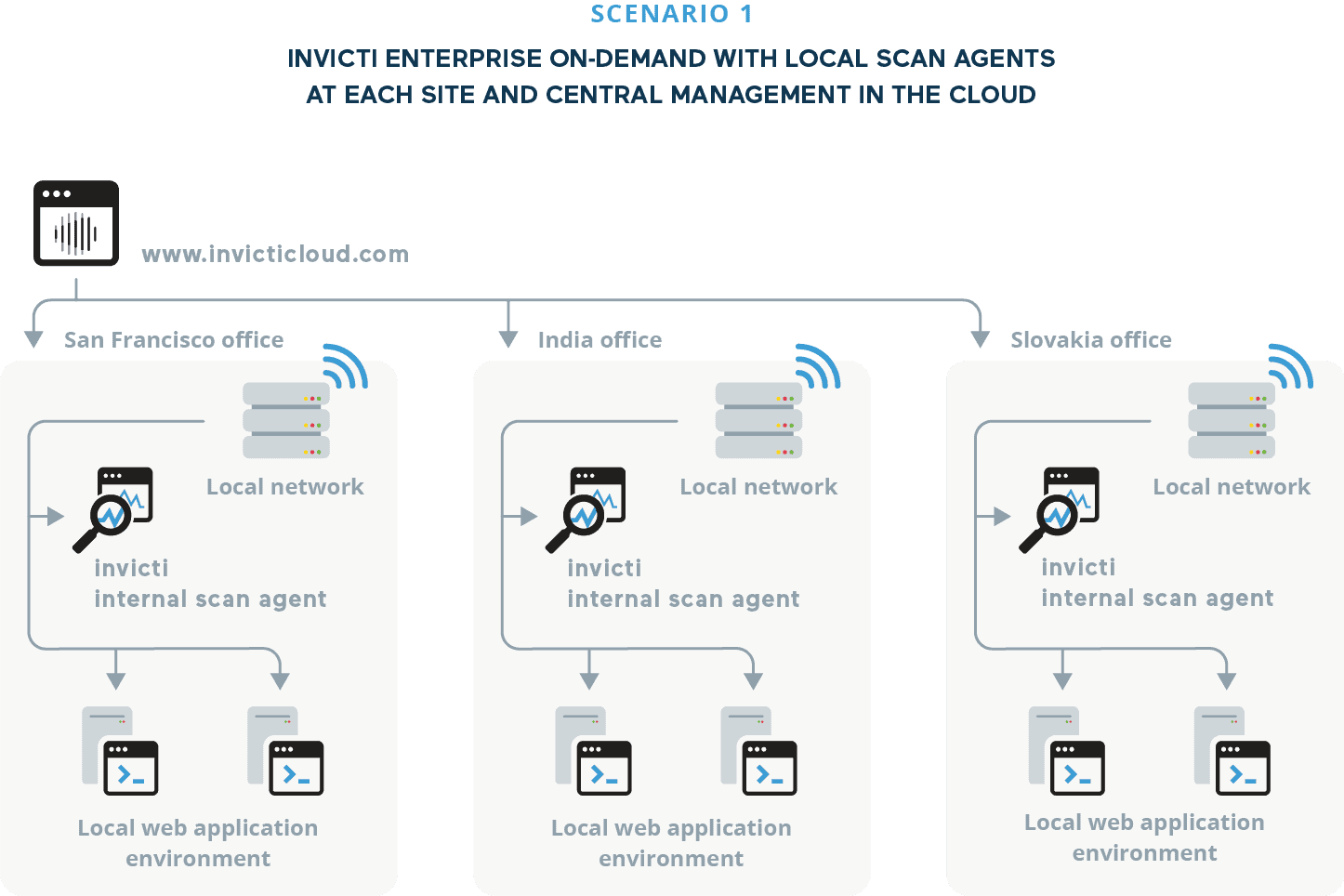
A multinational corporation has web development teams spread across 20 separate physical sites in multiple countries, using a mixture of Windows and Linux environments. To protect intellectual property, development and staging environments must be isolated from the public Internet. At the same time, the corporation needs to uniformly enforce strict web application security policies to meet regulatory requirements for information security.
SOLUTION – Invicti Enterprise on-demand with local scan agents at each site, managed centrally by the Invicti Enterprise server in the cloud. For web assets that can’t be scanned out-of-the-box using on-demand scanning with automatic scaling, local scan agents are used. Each team has one machine that runs a scan agent to test selected web assets in the team’s local network, with scans triggered automatically via a custom IDE integration using the Invicti API. Scan results from each agent are sent to the central Invicti server where the web security team can use Invicti’s vulnerability classification and management features to assign issues to developers.
Internal scan agents allow the organization to scan non-public development and staging environments. Once deployed to production, the live applications are scanned directly using Invicti Enterprise on-demand.
The Government Agency
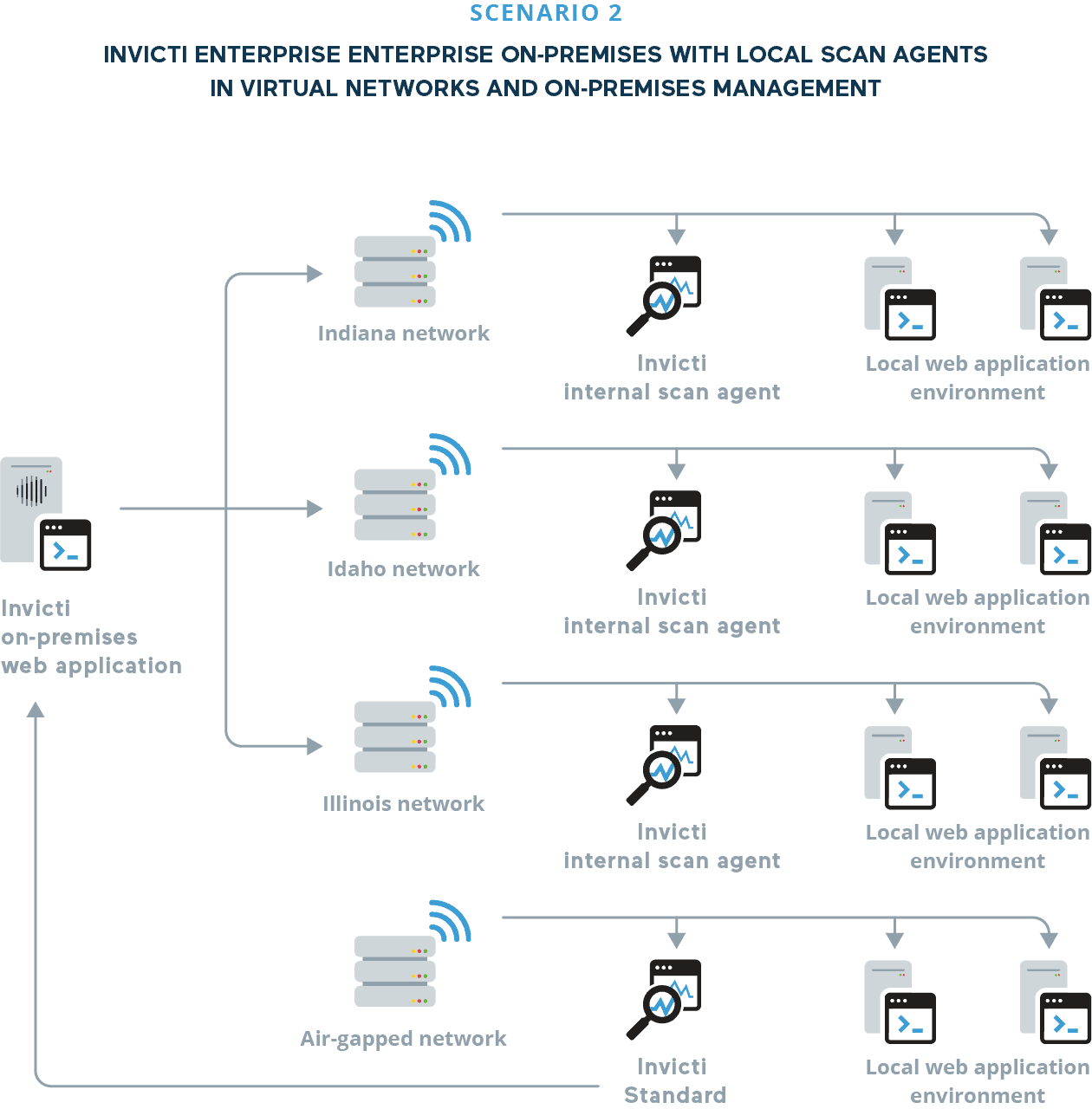
A federal agency maintains and develops dozens of web applications for multiple states. Development is spread across some 30 separate teams, each with its own development, staging, and production environments. Each team has its own virtual network within the wider agency infrastructure. For compliance reasons and to protect citizens’ personal information, data storage and application development must be isolated from the public web.
SOLUTION – Invicti Enterprise on-premises with local scan agents in each team’s virtual network, managed by a Invicti Enterprise server deployed on-premises. Each team has one virtual machine that runs a scan agent to test selected web assets in the team’s local network, with scans triggered automatically via a Jenkins integration. Scan results from each agent are sent to the on-premises Invicti application server. The web security team uses Invicti’s vulnerability classification and management features to assign issues to developers.
For ad-hoc scans and manual testing in isolated networks, the security team uses Invicti Standard, which is included with the Enterprise edition. Scan results from Invicti Standard are then uploaded to the on-premises Invicti server.
The SaaS Vendor
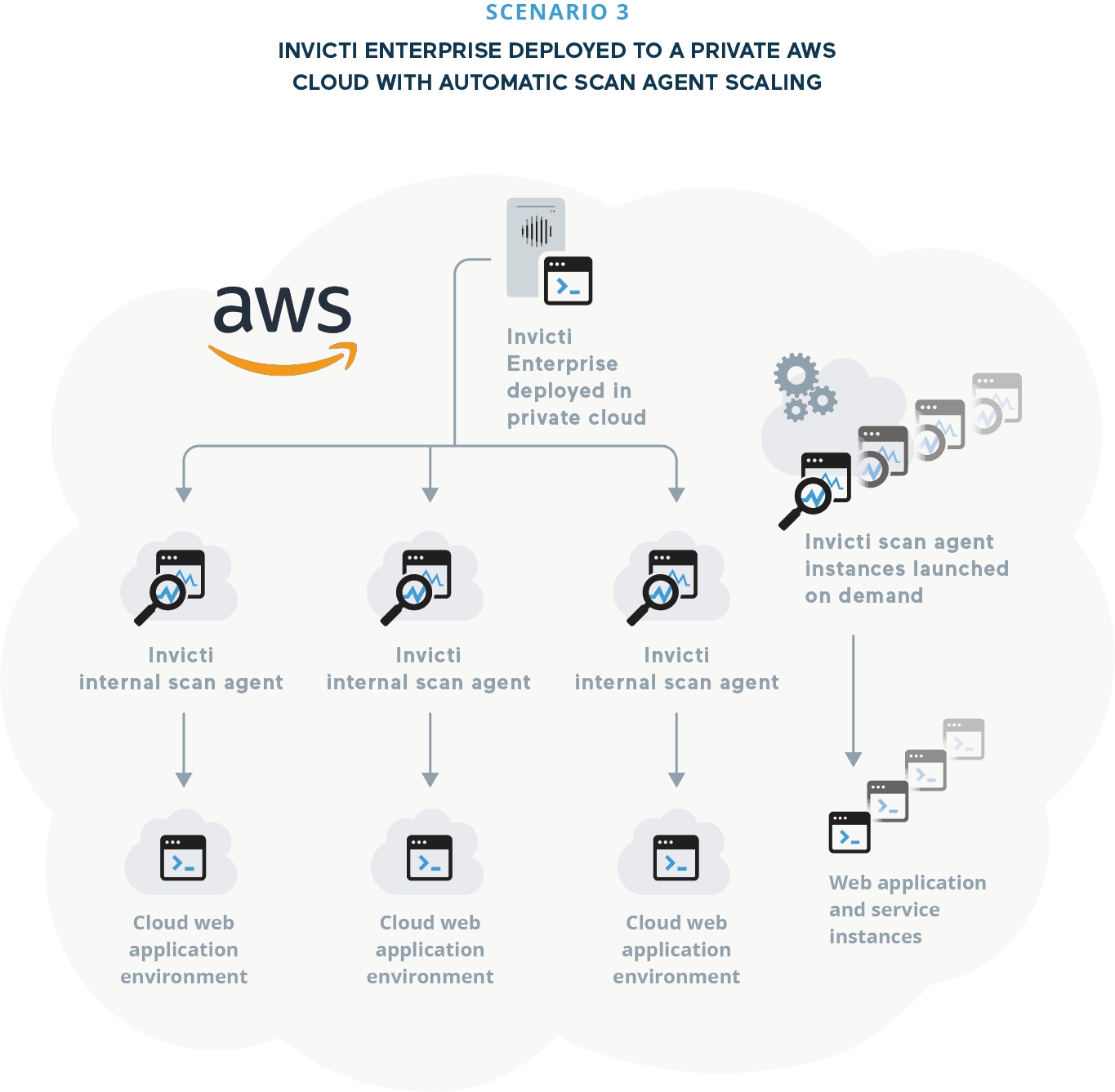
A major technology services company runs a huge and constantly growing all-cloud environment based on Amazon Web Services, with hundreds of services and applications developed and maintained both for customers and for internal use. Web application environments change on a daily basis as new functionality is rolled out in CI/CD pipelines and existing containerized services and applications are spun up depending on demand.
SOLUTION – Invicti Enterprise deployed to a private AWS cloud with cloud scan agents and automatic agent scaling on AWS. Every time a scan is launched, Invicti creates a new agent instance, runs the scan, collects the results, and destroys the instance. Scans are triggered automatically for each build, so the number of scan agents varies to match the current testing workload. Results are sent back to the central server and accessible to the security team in the regular Invicti Enterprise user interface. All vulnerabilities confirmed with Proof-Based Scanning™ and classified as High or Critical severity are automatically assigned to developers to fix via a Jira integration.
Automatic scan agent scaling in the cloud provides a unique solution for securing environments that are spun up automatically, where it is impractical to deploy scan agents manually.
Conclusion
An effective web application security program relies on accuracy, consistency, and maximum automation. For large organizations, applying consistent vulnerability scanning policies across multiple environments poses a major challenge. They need a solution that would allow them to distribute scanning while providing centralized results and visibility, regardless of the specific architecture and technologies.
Invicti Enterprise was designed with precisely this goal in mind, using a modular architecture that decouples vulnerability scanning and management. Organizations can align scanning to their internal structures and workflows by deploying Invicti scan agents in all their web application environments, whether on-premises or in the cloud, but still reap the benefits of centralized security management. Combined with the benefits of extensive integration and customization, this translates into improved coverage, streamlined workflows and, ultimately, more secure web applications.

