Peace of mind from open-source risk
Open-source components are heavily used in modern software development without paying much attention to the security or legal risks they might carry. Invicti's SBOM Radar brings peace of mind to your SBOM processes.
3600+ Top Organizations Trust Invicti
























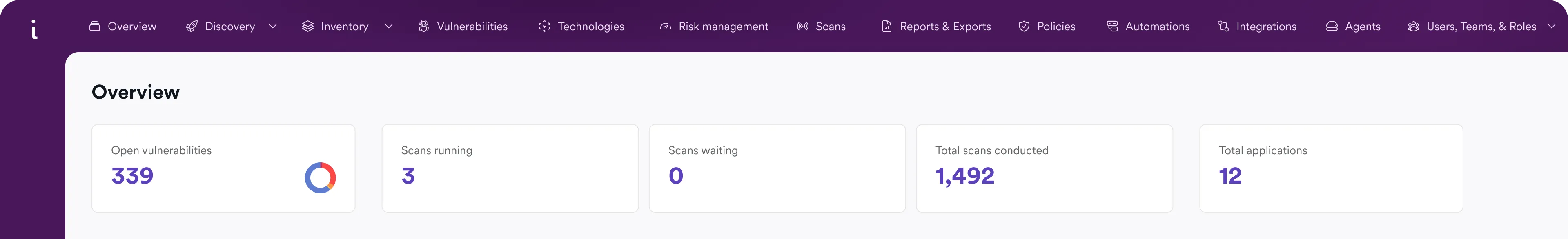
Manage open-source risk at scale
Invicti provides unique features that make open-source risk management simple and fast.
SBOM radar
Easily create SBOM reports for all your applications and export them in multiple formats.
License risk check
Get a list of all open-source licenses involved with the components your application uses.
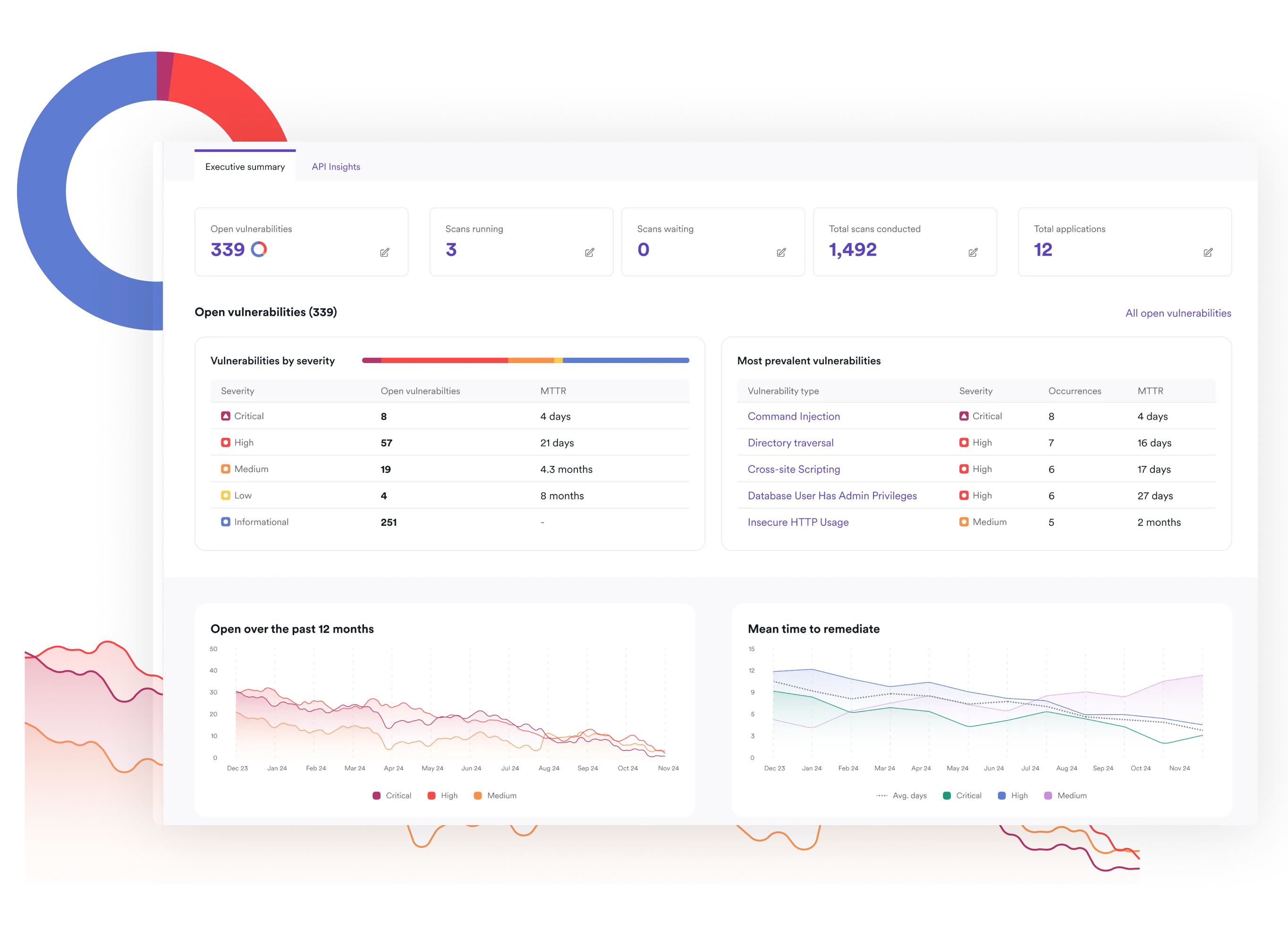
SOC II certified. Audit ready.
Invicti is thorougly pressure-tested with an SOC II certification. Audit the comprehensive logs from our Platform and integrate into your compliance programs.
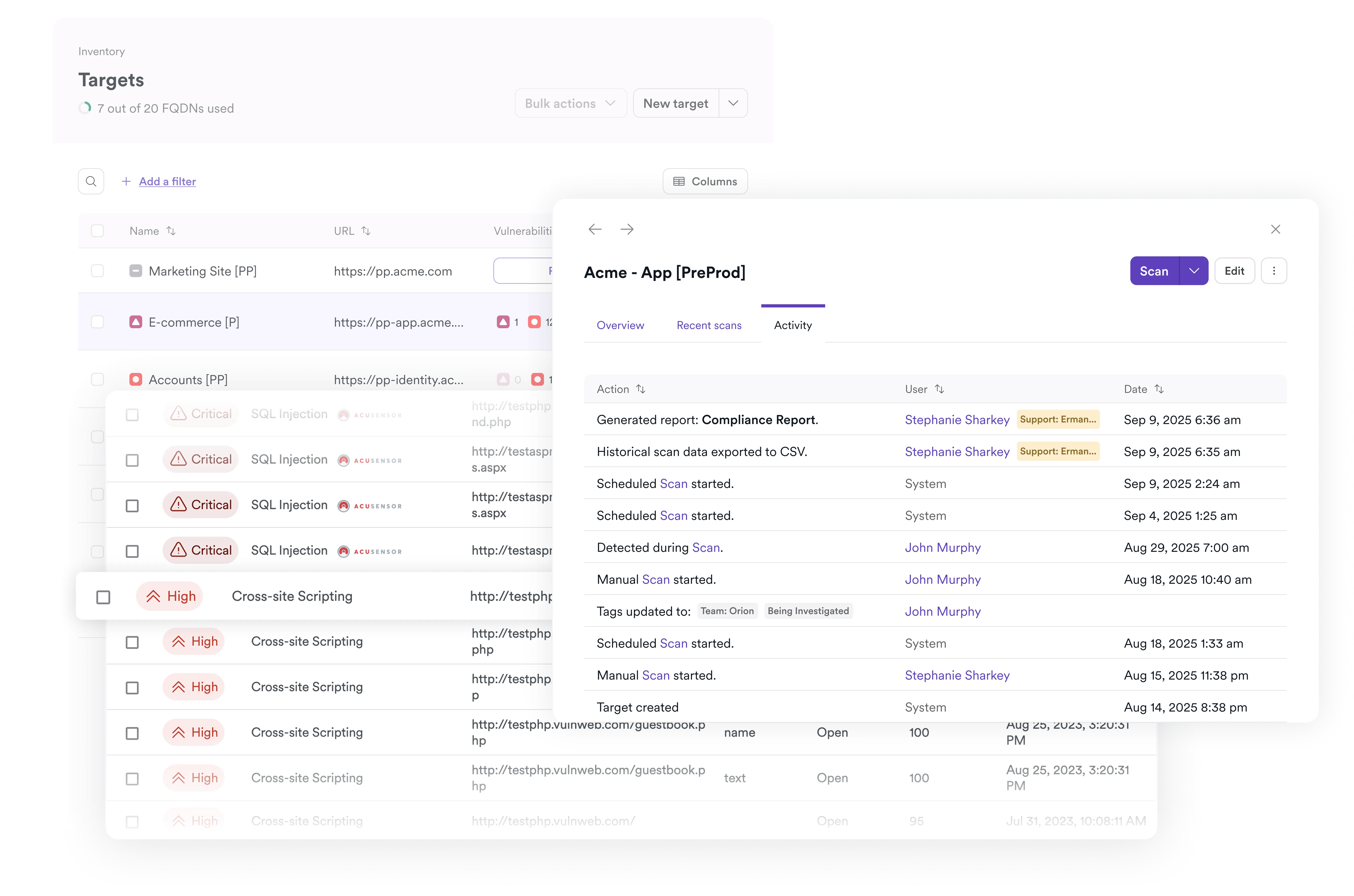
Govern SBOMs for every app
SBOM Radar automates discovery, vulnerability checks, and policy enforcement.
Reduce license risks
Understand which open-source components are riskiest.

Stay audit-ready
Turn continuous SBOM monitoring into continuous compliance.
Integrated with the tools you already use
We've got open-source risk covered.