Take control of open-source risk
Invicti brings software composition analysis (SCA) into the same intelligent platform as DAST, SAST, IAST, API Security, and Container Security so you can see and act on component risks with clarity and confidence.
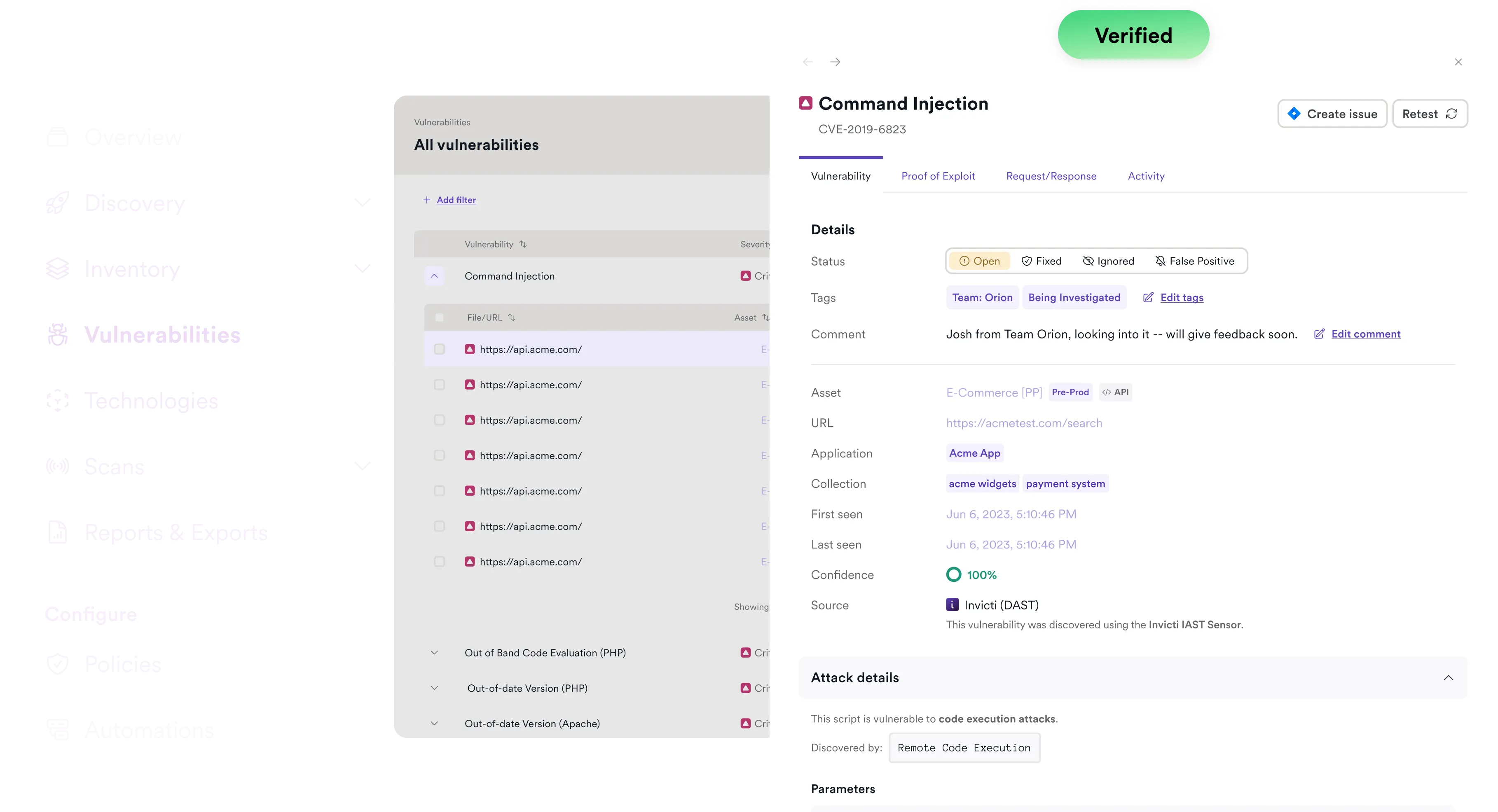

The problem with legacy SCA
Open-source components accelerate development, but they also introduce hidden risks. Legacy SCA finds them but runs as a static tool, disconnected from DAST, IAST, and CI/CD pipelines, leaving security teams to manage open-source risk in isolation. Duplicate or unverified alerts lack context and eventually get ignored while exploitable vulnerabilities slip into production.
Non-actionable alerts
Legacy SCA tools build static lists of every vulnerable dependency, without verifying exploitability. With thousands of alerts, teams can’t tell signal from noise.
Blind at runtime
Static-only SCA can’t see which components are active in production, leaving teams fixing issues with no immediate impact while real runtime risks slip through.
Vulnerabilities in a vacuum
Siloed SCA leaves teams guessing if flaws are compliance issues, actual risks, or noise. Without correlation across tools, prioritization is impossible.
Actionable alerts
Invicti SCA transforms your flood of alerts into prioritized, actionable findings you can trust.
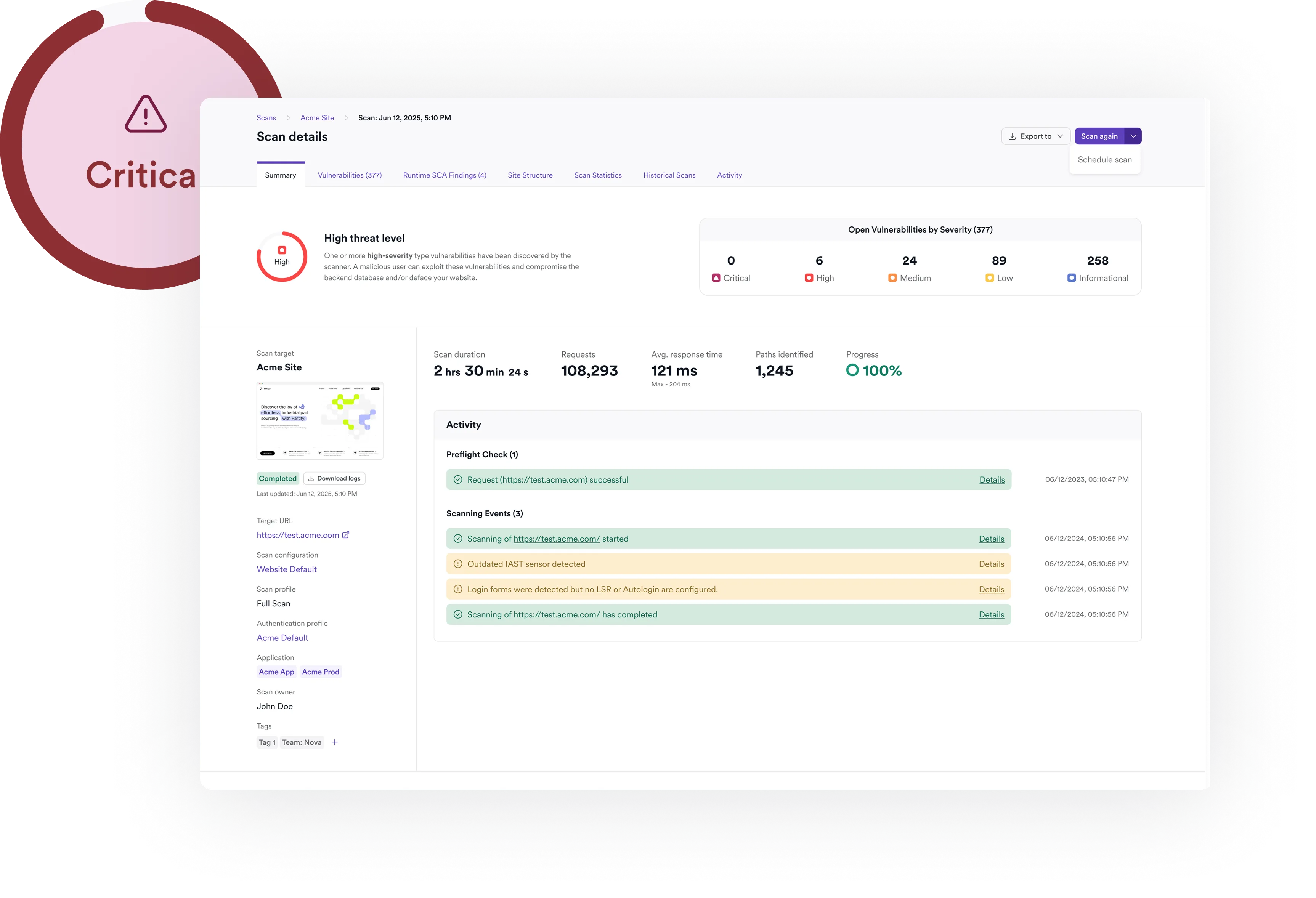
Full coverage across static and runtime checks
Invicti combines static and dynamic analysis to give you complete visibility into open-source risk both in code and in live environments.
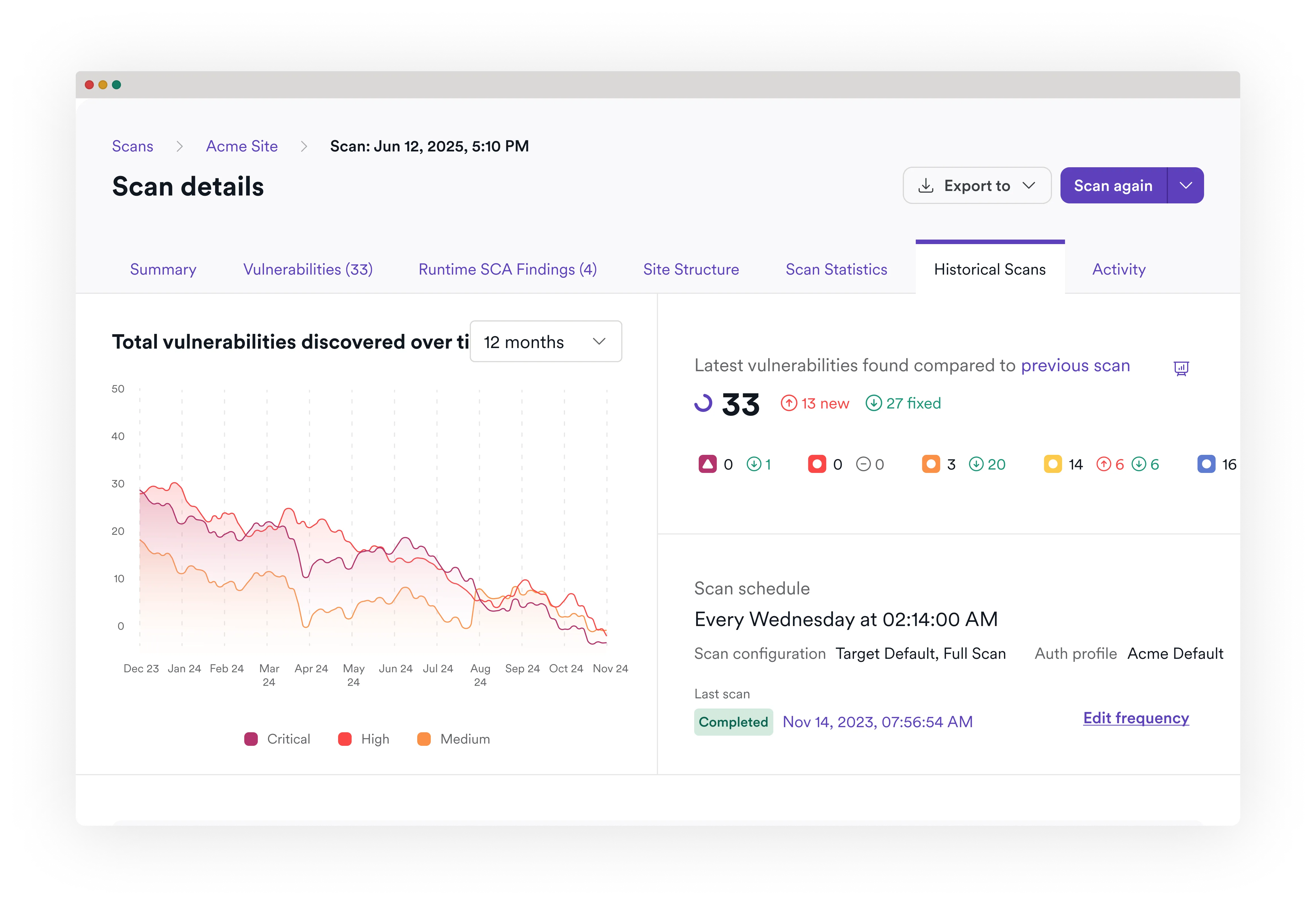
Open-source risk with full context
Invicti unifies SCA with AST and container security so you can prioritize open-source risk in the context of your overall risk posture.

Frequently asked SCA questions
Yes. Invicti offers static and dynamic SCA as a fully integrated capability within the Invicti Application Security Platform. Unlike standalone tools, Invicti correlates SCA results with DAST, SAST, API, and container findings for a single, normalized view of risk. With Invicti ASPM, SCA results flow into CI/CD, ticketing, and reporting pipelines without requiring an extra orchestration layer.
Traditional SCA tools generate static inventories of vulnerable dependencies, leaving teams with long, context-free lists. Invicti combines static and dynamic SCA:
- Static SCA: Flags all declared components with known vulnerabilities, even if not loaded at runtime.
- Dynamic SCA (in DAST): Flags only the components actually in use during runtime scans.
- Together, this hybrid approach helps teams prioritize exploitable risks. Invicti also adds SBOM management, deduplication across tools, and risk scoring so teams don’t drown in duplicate or low-value alerts.
Yes. Invicti traces vulnerabilities through full dependency chains, including transitive dependencies. By resolving which libraries call others, the platform ensures you don’t miss risks buried several layers deep, and avoids false alarms when a declared library isn’t actually used in the application.
The platform syncs with leading vulnerability databases frequently to make sure the latest CVEs and advisories are included in results. This ensures teams don’t miss emerging vulnerabilities and can react quickly to new disclosures.
Yes. Invicti SCA detects known vulnerabilities (CVE-based) in open-source libraries and flags risky licenses for compliance. With SBOM and license analysis features in Invicti ASPM, Invicti also supports CycloneDX, SPDX, and other SBOM formats, giving security teams both security and compliance visibility. This means you can track vulnerabilities and avoid licensing pitfalls that could impact business or regulatory requirements.
Invicti SCA is fully automatable. It integrates into CI/CD pipelines (Jenkins, GitHub Actions, GitLab, Azure DevOps, etc.) to block risky builds, route findings directly into Jira or Azure Boards, and update tickets as fixes are validated. Invicti adds policy enforcement rules, meaning you can automatically fail a build if a high-severity open-source vulnerability is found, or trigger workflows in Slack/Teams when license violations appear.
Invicti’s SCA flags both security and compliance risks in open-source components. With support for CycloneDX and SPDX SBOM standards, the platform not only identifies vulnerabilities but also pinpoints risky open-source licenses such as copyleft or GPL. This helps organizations meet compliance requirements and avoid legal or business disruptions.
Yes. Invicti generates SBOMs in industry standards like CycloneDX and SPDX and automatically maps them to applications. This makes it easy to produce audit-ready reports for government or industry compliance frameworks, while also giving security teams continuous visibility into open-source risk .
See every open-source risk with static and dynamic SCA, validated in context.









