Automated penetration testing tools for web apps and APIs
Use Invicti’s DAST-based platform to automate pentesting and bring it in-house. By making it part of a continuous security testing process, you can proactively find and fix vulnerabilities across your websites, web applications, and APIs.

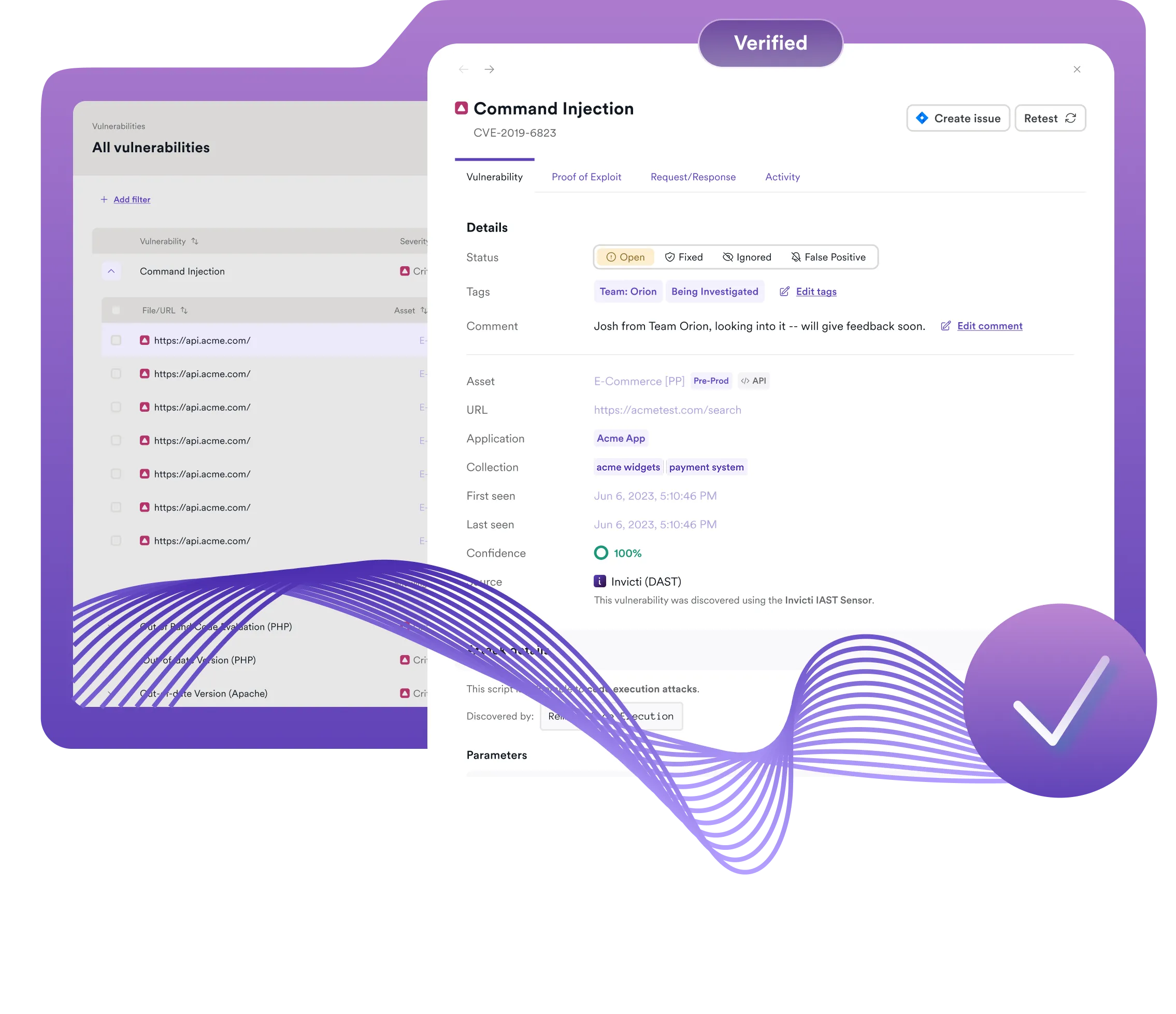
Manual vs automated penetration testing
Determined malicious hackers are probing your web applications for security vulnerabilities all the time. They have access to the same penetration testing software and security tools that security professionals use to conduct security assessments—but before they go in manually and risk exposure, they use swarms of bots to continuously look for weaknesses and easy points of entry into your environments.
Manual penetration testing (in its broadest version also called red teaming) is performed by security professionals and ethical hackers who simulate the actions of an attacker trying to get into your systems. Malicious hackers don’t have to follow rules and restrictions, so both they and red teamers may run network scans, look for operating system vulnerabilities, and attempt social engineering tricks as well as directly attacking your web applications using a variety of tools. But above all, the bad guys wait for their recon bots to find easy targets first.
Web applications and APIs are in the first line of fire. Industry research shows the majority of cyberattacks originate with a web app, which makes web application pentesting a priority to maintain a solid security posture. Being slow and expensive, manual penetration testing is commissioned periodically and not always for the full scope of production environments. To quickly find weak spots in frequently changing app environments before malicious bots can exploit them, you need to automate at least some penetration testing work and perform it in a continuous process across all your assets—and this is where automated penetration testing comes in.
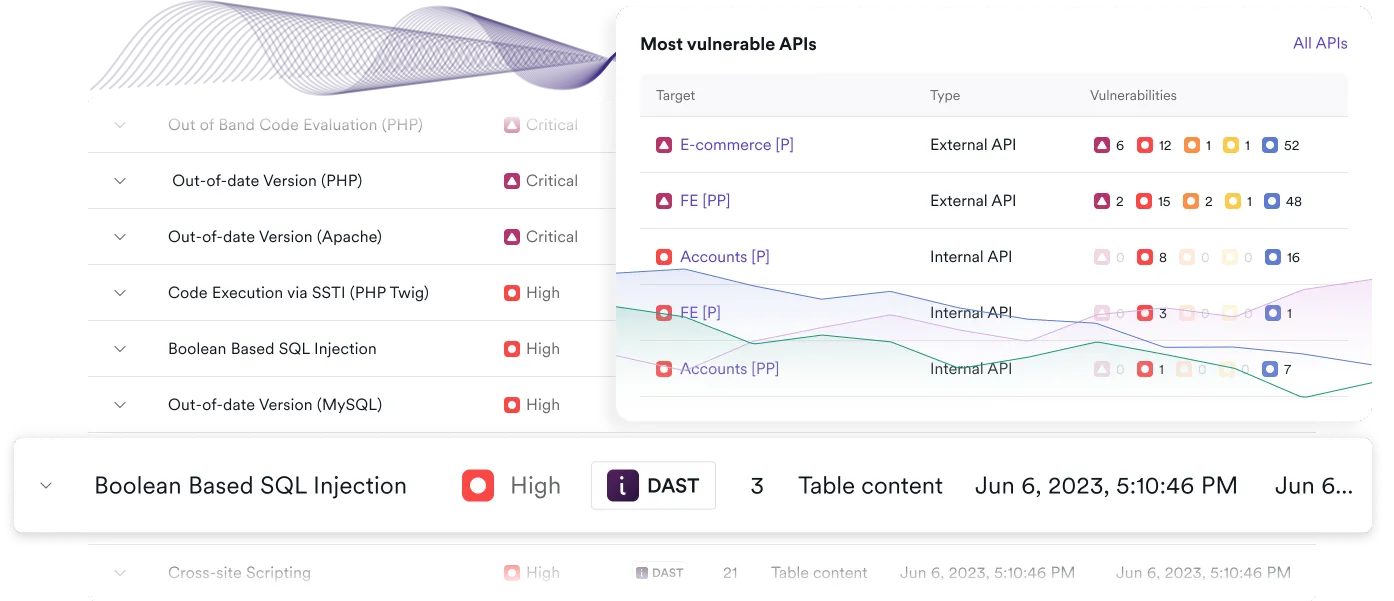
Automated penetration testing software
With an automated vulnerability assessment tool such as Invicti in place, organizations can, in effect, conduct automated and continuous penetration tests on their web applications and APIs without needing an army of skilled penetration testers. Using a vulnerability scanner as their web pen testing software lets companies scan thousands of web assets for security vulnerabilities in a matter of hours, and do so on a continuous schedule to stay ahead of cyber threats.
To be clear, automated and manual penetration testing are two sides of the same coin, and any organization needs both. But manual pentesting is expensive, time-consuming, and limited in scope and time, so getting maximum value out of it requires an automated pentesting and remediation process to maintain a baseline level of security. By bringing a lot of web security testing in-house, you can find and fix all the “easy” vulnerabilities internally, covering misconfigurations, security headers, automatable injections, and more—allowing experienced pentesters to investigate more advanced attack vectors.
Automated pentesting ensures the scalability needed to keep up with your development process. If your application attack surface doubles in a short time due to rapid development in response to a business opportunity, automated testing is the only approach to security that can scale quickly enough without holding back releases and innovation.
Using DAST as your automated penetration testing tool
Any web application pentester starts their engagement by running a vulnerability scanner that can crawl a site or app and identify as many input parameters as possible for testing. By taking a high-quality DAST solution that can maximize this coverage while also performing automated security checks, organizations can, in effect, stop paying others to run a tool that the security team needs anyway. Look for tools that incorporate a full browser engine to ensure they can crawl, navigate, and test even Javascript-heavy modern applications like SPAs.
To be suitable for automated penetration testing, a DAST tool must be uncompromisingly accurate. Pentesters will often use vulnerability scanners, both commercial and open-source, that are designed to aid manual testing but are not optimized for use as standalone automated tools. Advanced features like Invicti’s proof-based scanning for automatic vulnerability exploitation and confirmation allow a DAST to safely and efficiently deliver actionable security issue reports on an enterprise scale without regular human interaction.
One significant benefit of using DAST for in-house automated pentesting is that you can integrate it with your development, operations, and security workflows. Instead of getting an external manual pentest report that you then need to do something about, you can directly and immediately work on identified issues. When feeding automated findings into your workflows, DAST tool accuracy is paramount to avoid false positives while also exploring as many potential vulnerabilities as possible.
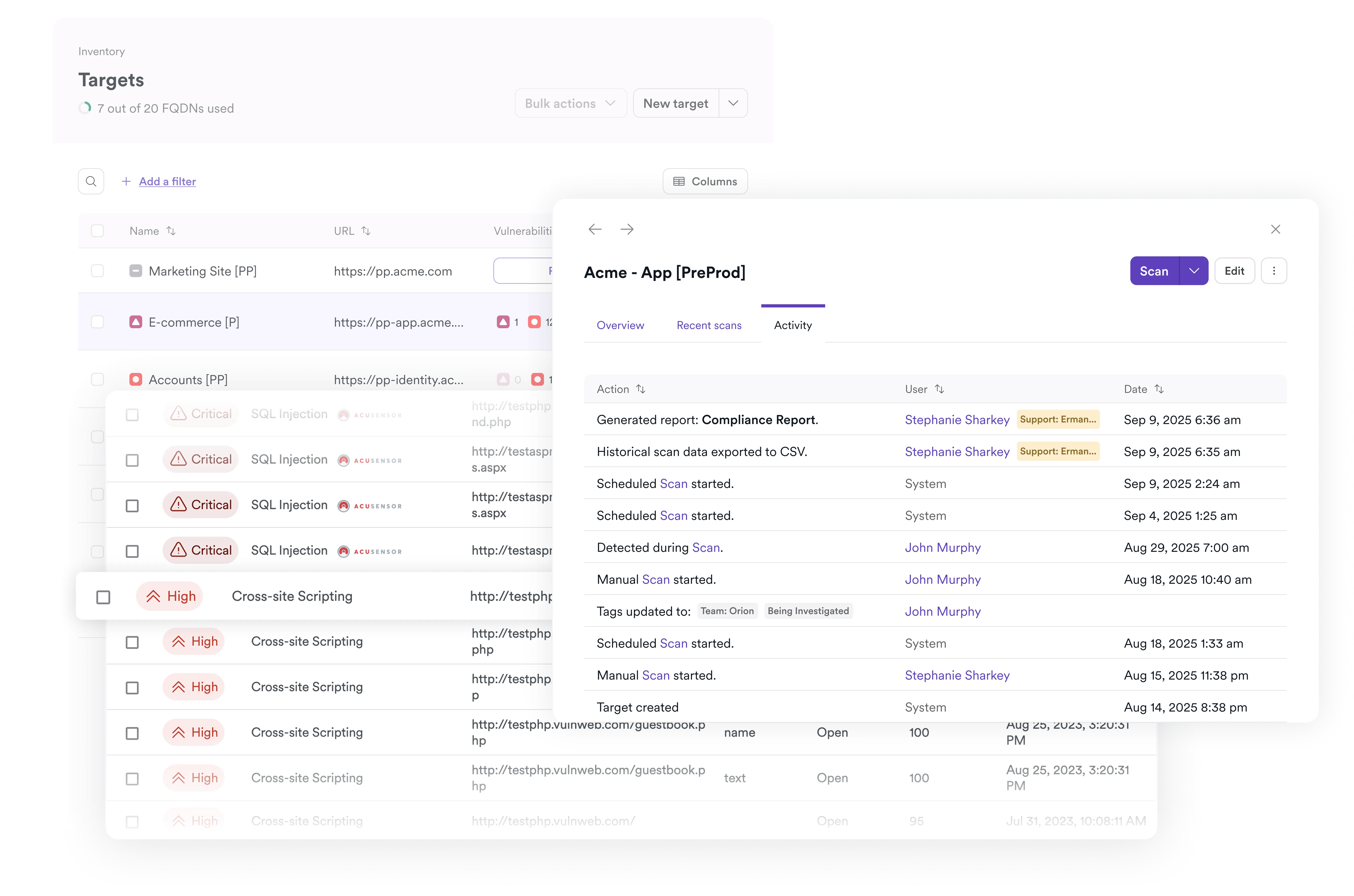
Implementing automated pentesting
Manual pentesting is typically a one-off event—a penetration test is performed, you get the findings, you pay up, and the assignment is over. Automated pentesting, on the other hand, is best performed as part of an equally automated continuous process that’s an integral part of your cybersecurity program:
- Focus on your web application and API attack surface: Web vulnerability scanning brings the quickest and easiest wins for attackers and defenders alike, so this is where your automated pentest efforts should focus. Automated tools also exist to find and even exploit web vulnerabilities safely, while more advanced and intrusive methods like network penetration testing are best left to cybersecurity professionals during manual testing.
- Use an accurate DAST platform instead of looking for a separate automated pentesting tool: Automated web pentesting is just a subset of dynamic application security testing, so using a high quality DAST solution is a far more efficient, flexible, cost-effective approach than adding yet another tool that uses the same methodology. Look for a DAST scanner with automated vulnerability confirmation functionality to prevent wasting time on false positives.
- Integrate automated penetration testing using DAST into your prioritization and remediation workflows: Build an application security process that incorporates automated pentesting into your existing workflows for vulnerability management, continuous monitoring, and protection. Be sure to check if your chosen solution supports your deployment model, especially if you need to run scans on-premises or on a mixture of on-prem and cloud-based deployments.
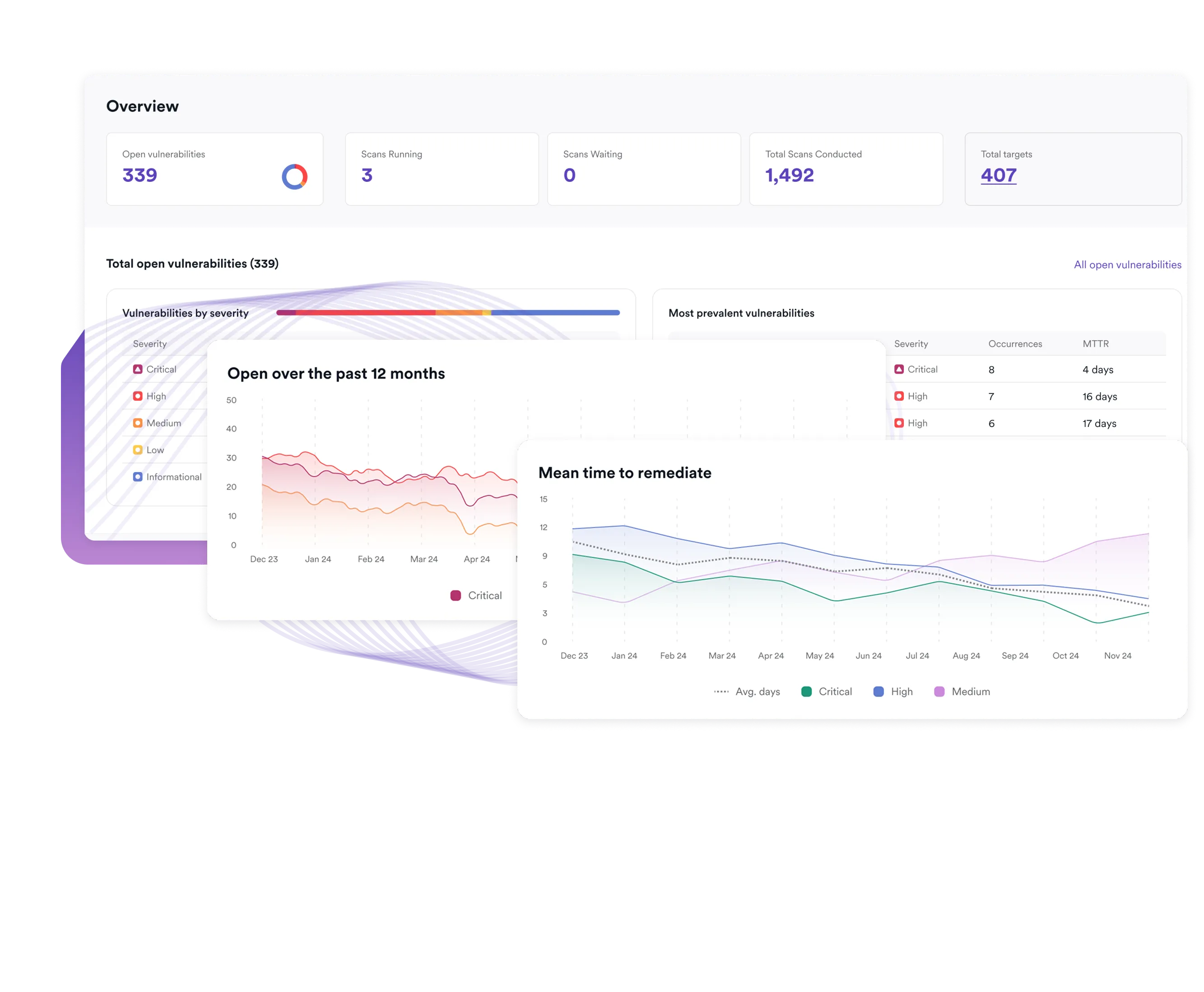
FAQs about automated penetration testing
Many routine aspects of pentesting can and should be automated, leaving deeper manual investigation to cybersecurity experts. For web applications and APIs, DAST tools can automatically probe for common security weaknesses like SQL injection vulnerabilities before they are found and exploited by bad actors.
A combination of automated and manual pentesting is always recommended to combine the speed and coverage of automated testing with the expertise and intuition of human experts. Reliable automated scanners can provide a baseline level of security testing in between less frequent (and more costly) manual tests.
Ideally, the automated penetration testing role should be filled by security testing tools that run in a continuous process. For DAST solutions used as web application pentesting tools, the recommended schedule is daily incremental scans for new and updated assets and full weekly scans on entire environments.
Using your DAST as an automated pentesting tool has the benefit of collating all web vulnerability reports on a single platform for a near-real-time view of your security posture. When DAST is integrated both into security operations and into DevOps, which is the recommended practice, identified security issues can be immediately assigned for remediation.
Depending on your security controls, tool reliability, and the level of integration, vulnerabilities found by an automated pentesting tool can be only reported for evaluation by the security team or immediately assigned for remediation. With web application testing using reliable DAST tools, you can even use the vulnerability information to set up temporary WAF rules to block attacks until the underlying issue is fixed.

