Discover shadow APIs, reconstruct specs, scan for runtime risks
Invicti extends DAST into API security with discovery, stateful scanning, and proof-based validation so you can uncover shadow APIs, test for vulnerabilities, and protect every endpoint in context.


3600+ Top Organizations Trust Invicti
















The problem with homegrown API security
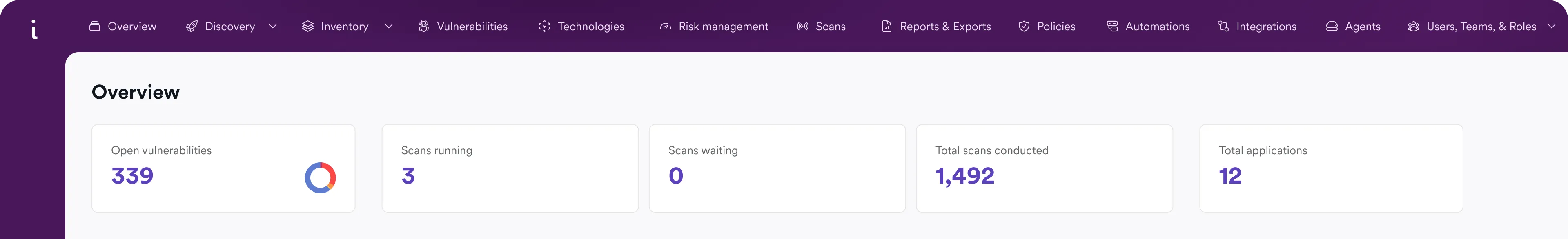
API discovery and continuous testing are crucial for protecting your applications and bottom line, but legacy approaches have left security teams overloaded and disconnected. In fact, up to 84% of security professionals experience an API security incident each year.
Blind spots in API inventory
Most teams don’t know how many APIs they have, let alone which ones are undocumented, exposed, or vulnerable.
Shallow or noisy testing
Basic scans or source-only reviews can’t validate complex issues like BOLA or BFLA. Teams end up drowning in false positives while missing the most dangerous vulnerabilities.
Disconnected remediation
Even though APIs are part of the app, API security findings often live in a silo. Security teams lack a unified view, while developers get incomplete guidance. This slows remediation and leaves APIs exposed during fixes.
Complete API discovery and inventory

Accurate, proof-based API scanning
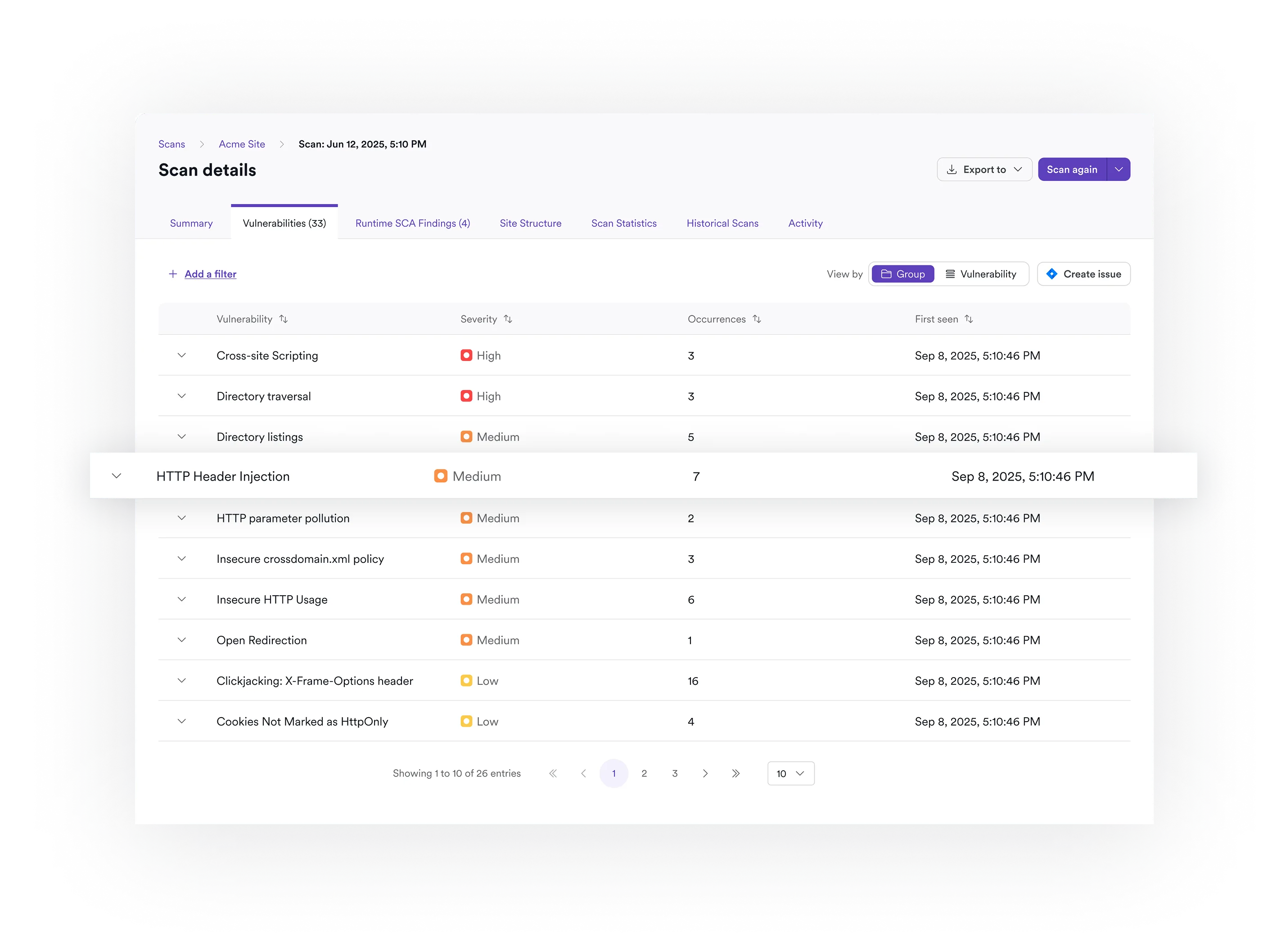
Unified remediation and protection

Integrate with your existing tools
Frequently asked API questions
Invicti discovers APIs through multiple methods:
- Zero-config techniques (passive traffic analysis and URL pattern detection)
- Sensorless detection based on API traffic generated during web app scans.
- Gateway integration (Apigee, Azure, Kong)
- File-based imports (Swagger/OpenAPI, Postman, WSDLs, GraphQL schemas).
Yes. Invicti supports all common authentication methods, including basic authentication and OAuth2, ensuring full coverage of API endpoints during scans.
Invicti also applies its proof-based scanning to APIs where technically possible, proving vulnerabilities by extracting data or showing a working exploit. This ensures verified, actionable results instead of guesses.
Yes. Invicti delivers actionable vulnerability reports complete with remediation guidance for APIs as part of its integrated workflow.
Yes. Invicti analyzes network API traffic in container deployments such as Kubernetes clusters to reconstruct API definitions based on observed traffic.
Yes. Invicti explicitly provides API discovery as part of its platform and its layered discovery approach helps fill gaps in known inventories.
When setting up API scanning on the Invicti Platform, you can define more than one user account to be used in auth-related testing, ideally a higher and a lower privilege account. By comparing access attempts using both accounts, Invicti can detect horizontal and vertical broken access issues.
Yes. API testing explicitly maps results to much of the OWASP API Top 10, including IDOR/BOLA, BFLA, and injection flaws.
Invicti supports scanning across REST, SOAP, and GraphQL APIs, dynamically adjusting to their structure.
Discover shadow APIs, validate real risks, and secure every endpoint.