Invicti (formerly Netsparker) vs. Qualys
The reason you run web application vulnerability scans to find and remediate issues – and Invicti (formerly Netsparker) stands head and shoulders above basic scanners from competitors like Qualys in terms of its vulnerability detection rate, result trustworthiness, and remediation guidance. Learn the difference between Invicti’s enterprise-grade application security solution and Qualys Web Application Security Scanner (WAS).
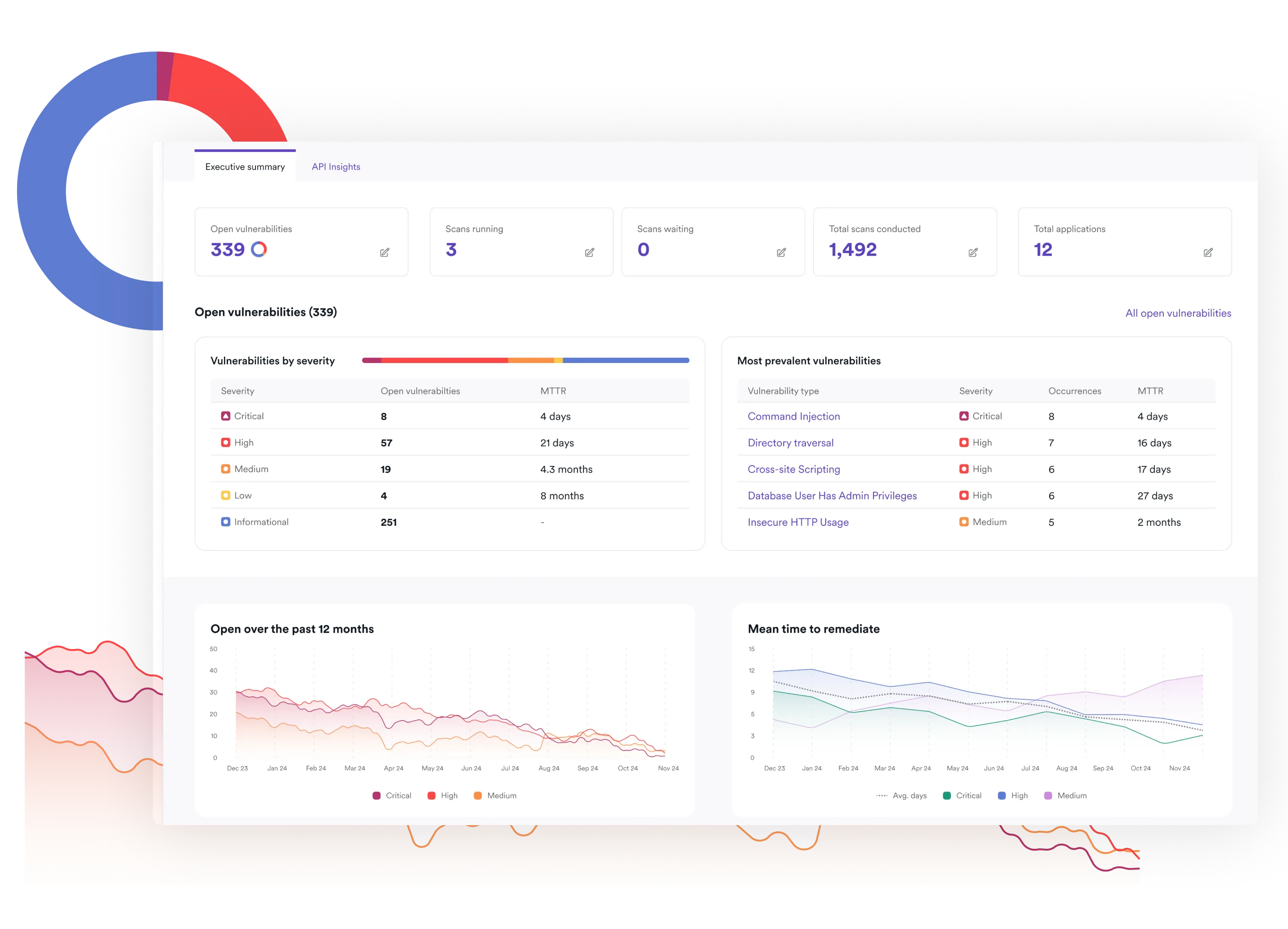
Invicti vs. Qualys at a glance
- Full-featured SaaS and on-premises enterprise DAST vs. basic cloud scanner
- Proof-based scanning for industry-leading accuracy and time-to-fix
- Automated and authenticated scanning to continuously cover web apps and APIs
- Enterprise-grade workflow integrations, reporting, and support
Full-featured SaaS and on-premises enterprise DAST vs. basic cloud scanner
With web-originating data breaches in the news every week, it’s no secret that your business (along with your customers’ data) is only as secure as its web applications and APIs. Any serious cybersecurity program needs to incorporate web application security – and that means at the very least having a reliable web vulnerability scanner that can identify exploitable web security vulnerabilities without wasting your time with false positives.
Choosing among the available alternatives seems a daunting task at first, with vendors like Qualys, Rapid7, and Tenable bundling online web application scanners with their core offerings and Portswigger providing its Burp Suite to aid penetration testing. You even have free open-source scanners like OWASP ZAP or w3af. But if you want scan results that are accurate, span your entire web attack surface, and lead to quick and effective fixes through workflow integrations, the choice gets easier. You’re looking for an enterprise-grade platform for dynamic application security testing (DAST) with automated vulnerability confirmations. And that means you’re looking for Invicti – especially if you need to scan web apps on-premises or in a hybrid SaaS/on-prem scenario.
Proof-based scanning for industry-leading accuracy and time-to-fix
Unlike less advanced scanners that work with probabilities rather than facts, Invicti uses proof-based scanning to safely and automatically exploit the majority of common web vulnerabilities and provide proof that an attack is feasible. This immediately shows your teams which issues are actionable and allows for confident automation via workflow integrations. With over 50 integrations provided out-of-the-box and a full internal API for customization, results from Invicti scans can go directly into issue trackers for rapid fixes, complete with technical information and remediation guidance for each vulnerability.
Invicti does away with the uncertainty and low user trust that plague less advanced scanners. Identified vulnerabilities are assigned accurate technical severity ratings to aid prioritization, reduce risk exposure, and shorten time-to-fix. Developers automatically get actionable tickets with full technical details and guidance, and submitted fixes can be automatically rescanned to ensure that vulnerabilities are fixed correctly and permanently. And you can use the built-in vulnerability management functionality or integrate with your existing workflows to handle security vulnerabilities in a way that works best for your development and security teams.
Automated and authenticated scanning to continuously cover web apps and APIs
Most web application security scanners are designed to be run manually and are limited in coverage in one way or another. For Qualys WAS, this means cloud-only (no on-premises option) and no automated support for enterprise scanning essentials like single sign-on (SSO) or two-factor authentication (2FA). Yet automated authentication is a must for scanning enterprise environments that overwhelmingly require authentication and authorization to access most or all web assets, both web apps and APIs, greatly limiting the ability of Qualys WAS to test APIs and business application environments.
When looking at your web security posture, having a continuous and thorough vulnerability testing process is crucial to find and eliminate vulnerabilities that could result in a data breach or worse. Unlike Qualys WAS, Invicti is designed with automation in mind and is constantly updated with new and improved security checks, so you can run the Invicti scanner on a schedule to minimize the risk of attackers finding an exploitable weakness first. The same Invicti solution you use for external web application scanning can be automated into your software development lifecycle (SDLC), doing double duty in web security and secure development.
Enterprise-grade workflow integrations, reporting, and support
When comparing Invicti (formerly Netsparker) to web scanners from more general security tool vendors such as Qualys, keep in mind that it’s relatively easy to create a rudimentary vulnerability scanner – but it takes years to develop and constantly update a scanner that is accurate and reliable enough for enterprise use. What’s more, with Invicti, the scanner is the heart of a fully integrated suite of web asset discovery, security testing, vulnerability management, workflow integration, and reporting tools. It does away with the “here are some possible issues to look at” approach of basic scanners, instead acting as an effective solution to identify actionable vulnerabilities, help your teams fix them, and keep track of your security posture at multiple levels.
Designed with SDLC integration in mind and incorporating nearly two decades of experience from building the Acunetix and Netsparker scanners, Invicti delivers a DAST tool that’s been proven to work with modern web apps and APIs, in agile development workflows, and at an enterprise scale:
- Accurate security checks for all major web vulnerability classes, including SQL injection, cross-site scripting (XSS), server-side request forgery (SSRF), and more (including out-of-band detections)
- Automatic vulnerability confirmations with proof-based scanning to safely and confidently indicate exploitable issues
- Over 50 built-in integrations with popular issue trackers such as Jira, CI/CD pipelines, vulnerability management tools, and collaboration platforms for workflow automation
- Support for popular authentication methods (including SSO with OAuth2) for maximum test coverage across web apps and APIs
- Optional server-side agents to add interactive application security testing (IAST) and dynamic software composition analysis (SCA)
- Available as a cloud-based SaaS solution, an on-premises installation, or a combination of both (central SaaS with locally-installed scan agents)
Web scanner comparisons
In the 2018 independent web vulnerability scanners comparison, Invicti, formerly Netsparker, was the only scanner to identify all vulnerabilities and to report zero false positives.

Detect more vulnerabilities
When tested in third party benchmarks by security industry experts, Invicti, formerly Netsparker, identified all direct impact vulnerabilities, surpassing all other solutions. Their results show Invicti, formerly Netsparker, has the most advanced and dead accurate crawling & vulnerability scanning technology, and the highest web vulnerability detection rate.
While both are tools for web application security testing, they are very different in origin and capabilities. Invicti offers a dedicated and mature DAST-based platform (also including IAST and dynamic SCA) for automated vulnerability scanning in production and integrated testing during development. Qualys WAS is a more basic cloud scanner typically offered in combination with Qualys’s main products from the Qualys Cloud Platform.
Read more about building DAST into the software development lifecycle
A web application scanner can only test a web page or API endpoint for vulnerabilities if it can access the asset. Legacy vulnerability scanners that were originally designed to test public-facing and mostly static pages will return very limited results for business-critical applications and websites that require authentication – and nothing at all for API endpoints. Automatic authentication is a critical capability for advanced scanning solutions such as Invicti that are able to access and thoroughly test modern web apps and APIs.
Read more about the importance of authenticated vulnerability scanning
Web vulnerability scanners (often called DAST tools) work by sending test requests and mock attacks to a running website or web application and checking application responses and behaviors for signs of security vulnerabilities. While there are significant differences between products, an advanced DAST scanner such as Invicti can automatically identify (and often safely exploit) a wide variety of application vulnerabilities as well as security misconfigurations and outdated technologies.
Read more about how Invicti finds vulnerabilities
Many cloud-only web application scanners on the market are only able to access and scan cloud-based applications. Standalone scanners intended for penetration testing can be run manually to test offline environments. Invicti is unique in offering both a SaaS (cloud-based) and on-premises scanning solution, with the further option of hybrid deployments that combine the central visibility of SaaS with locally-installed scan agents.
Read more about flexible DAST deployment options for SaaS and on-premises environments
3600+ Top Organizations Trust Invicti
























Save your security team hundreds of hours with Invicti’s web security scanner.






