AI-powered AppSec
Invicti AI secures your applications from code to runtime.

3600+ Top Organizations Trust Invicti
























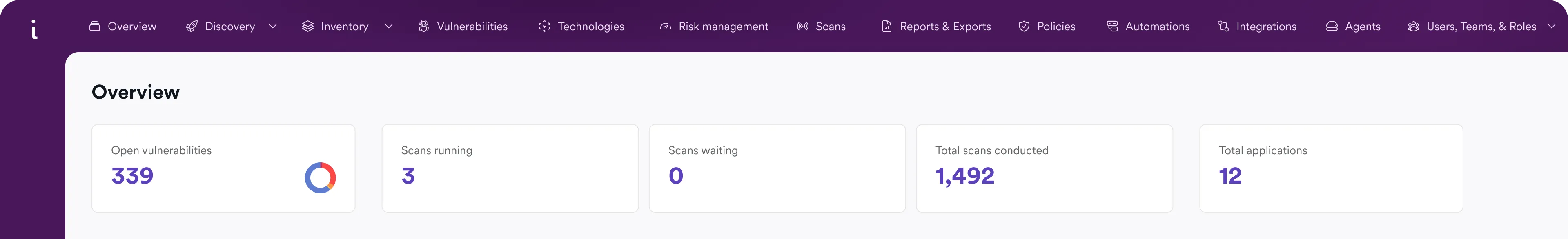
Challenges we’re solving with AI
Too many findings, too much code, and too many releases. AppSec needs have outgrown what humans alone can manage. Invicti applies AI to cut the noise, keep pace with modern development, and help developers fix issues fast.
Vibecoding risks
AI-assisted coding introduces hidden flaws that static tools flag without context. We prove which issues are exploitable at runtime, correlate them back to the code, and prioritize the biggest threats.
"Pentest-only" attack surfaces
Logic flaws, authenticated APIs, and AI-driven endpoints typically require manual penetration testing. We close this gap with AI form filling, stateful scanning, and LLM testing.
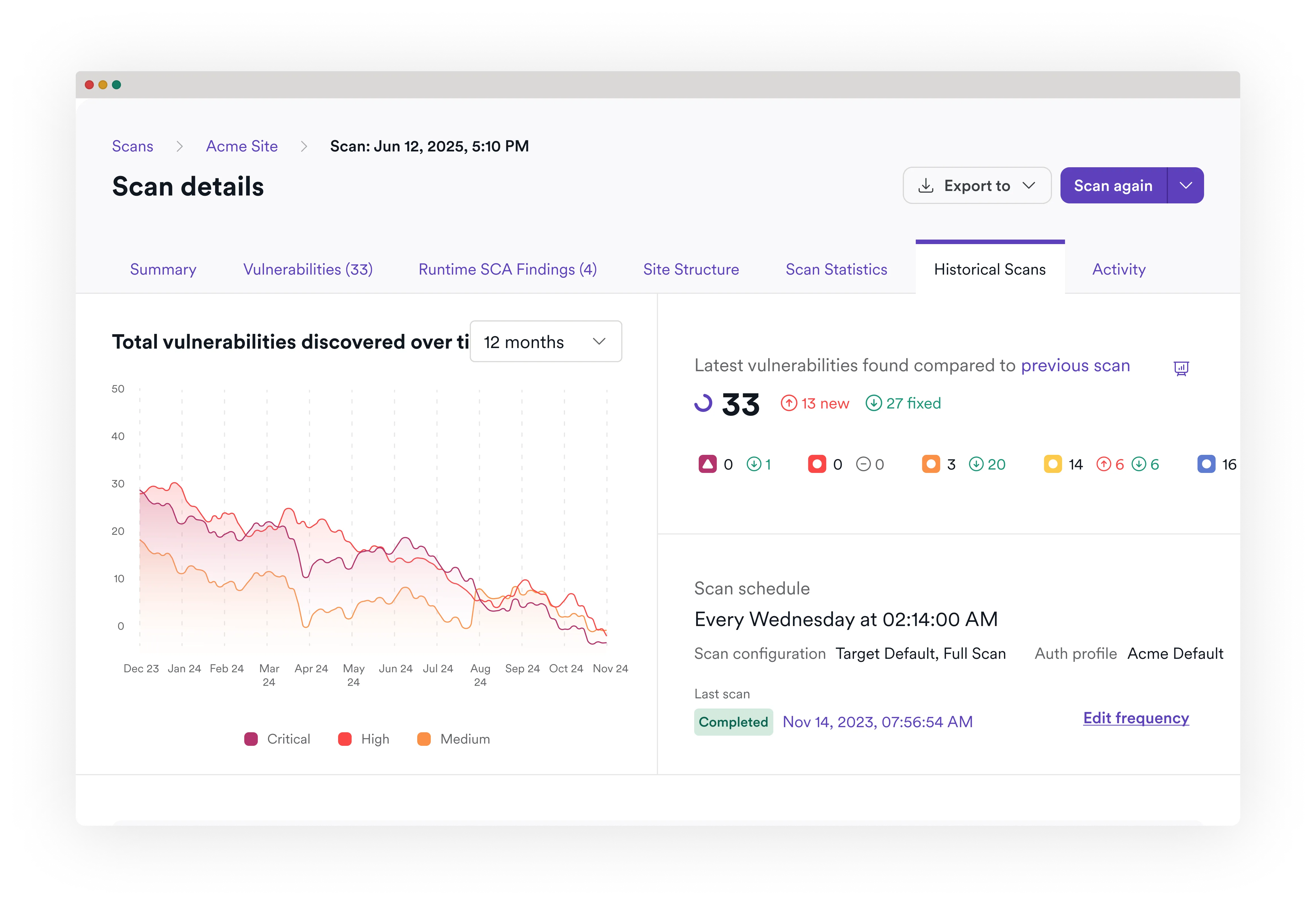
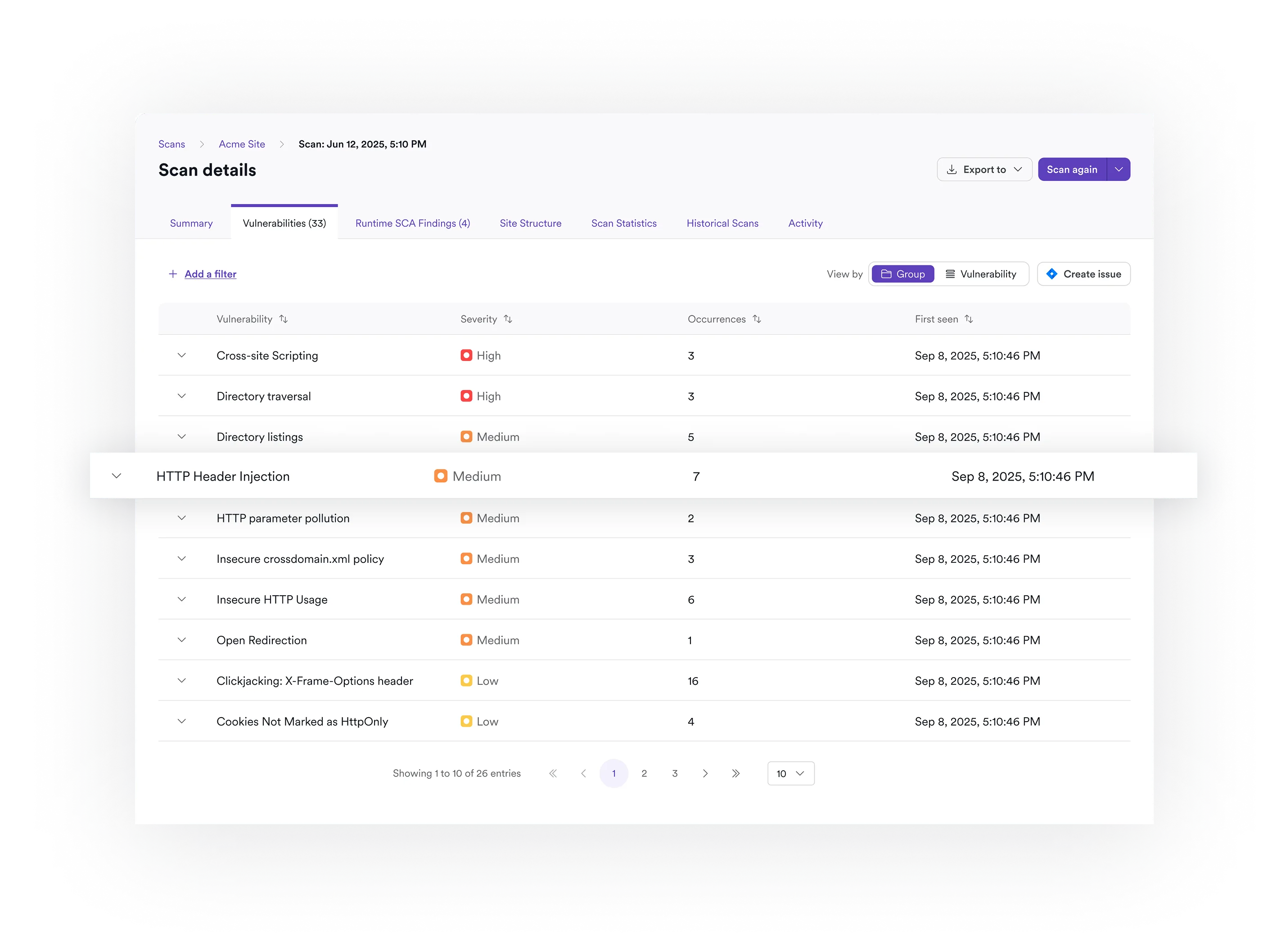
Correlation and remediation
There are too many vulnerability types for devs to remember. We correlate results across scanners, prove what’s real, and deliver code-level remediation guidance with training support and corporate memory.
Catch vibecoding risks before production
Close the pentesting gap

Empower and assist developers

Frequently asked AI security questions
AI is used to reduce noise, accelerate remediation, and improve coverage. Capabilities include predictive risk scoring, AI remediation guidance, and correlation of findings across multiple tools.
AI remediation guidance provides developers with code-level fix suggestions generated automatically for identified vulnerabilities. Instead of generic secure coding rules, Invicti delivers targeted recommendations in context, so developers can review and apply precise fixes directly.
Yes. Invicti includes security testing for LLM-powered and AI-driven interfaces, detecting risks such as prompt injection and shadow AI endpoints, aligned with the OWASP Top 10 for LLMs.
Invicti builds a corporate memory by tracking recurring vulnerabilities and linking them to an internal knowledge base. Integrations with platforms such as Secure Code Warrior and SecureFlag provide developers with targeted training based on the issues they’ve introduced, helping prevent repeats.
AI-aided correlation and deduplication link results across SAST, SCA, DAST, and container scanners. By normalizing and validating vulnerabilities, teams see a single confirmed issue instead of multiple duplicates.
With two-way integrations, AI-driven automation validates fixes through follow-up scans and can reopen tickets if issues persist.
Yes. Invicti uses AI to automate tasks such as authentication and form handling, expanding coverage for modern applications without manual setup.
Predictive risk scoring is the ability to rank vulnerabilities by risk before a scan even begins. Invicti uses application context, exploitability checks, and external threat intelligence to anticipate which endpoints are most likely to be attacked.
Learn how AI can empower developers and speed remediation