Zero-noise AppSec platform
Invicti delivers the fastest, most accurate testing tools with AI-powered automation and single-pane vulnerability correlation.


3600+ Top Organizations Trust Invicti

















The problem with legacy AppSec
Fragmented tools create alert fatigue, slow velocity, and leave teams with no way to measure real progress.
Drowning in alerts
Every scanner floods you with alerts. Without correlation, you waste hours chasing duplicates and false positives.
Always behind dev velocity
With one AppSec engineer for every hundred developers, manual triage and fragmented tools make it impossible to keep up with rapid release cycles.
No remediation metrics
“How long did it take to fix your critical vulnerabilities last quarter?” Most teams can’t answer this simple question, leaving leaders exposed.
Cut through the noise

Keep up with development
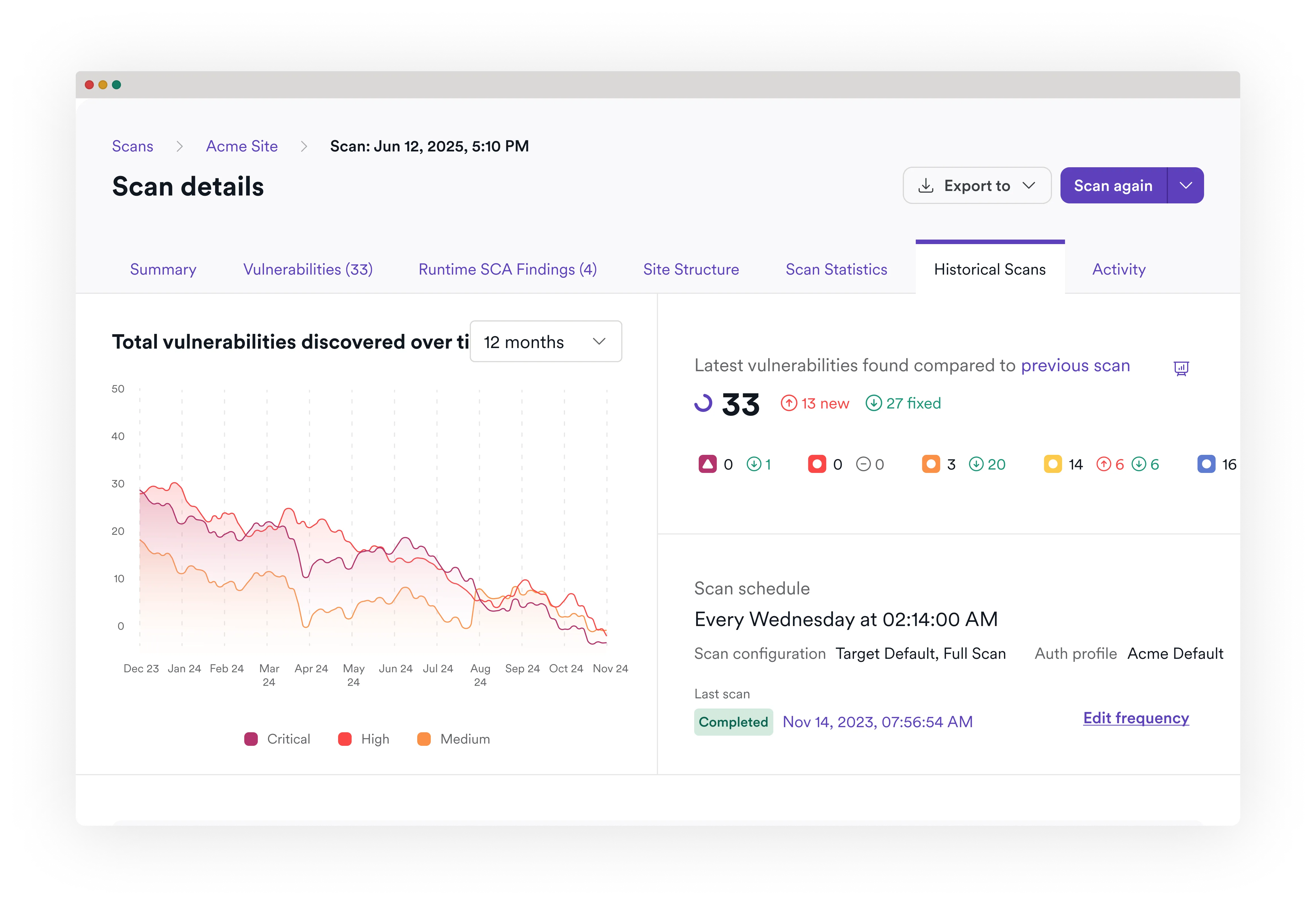
Know where you stand

Scan, correlate, and remediate in one platform

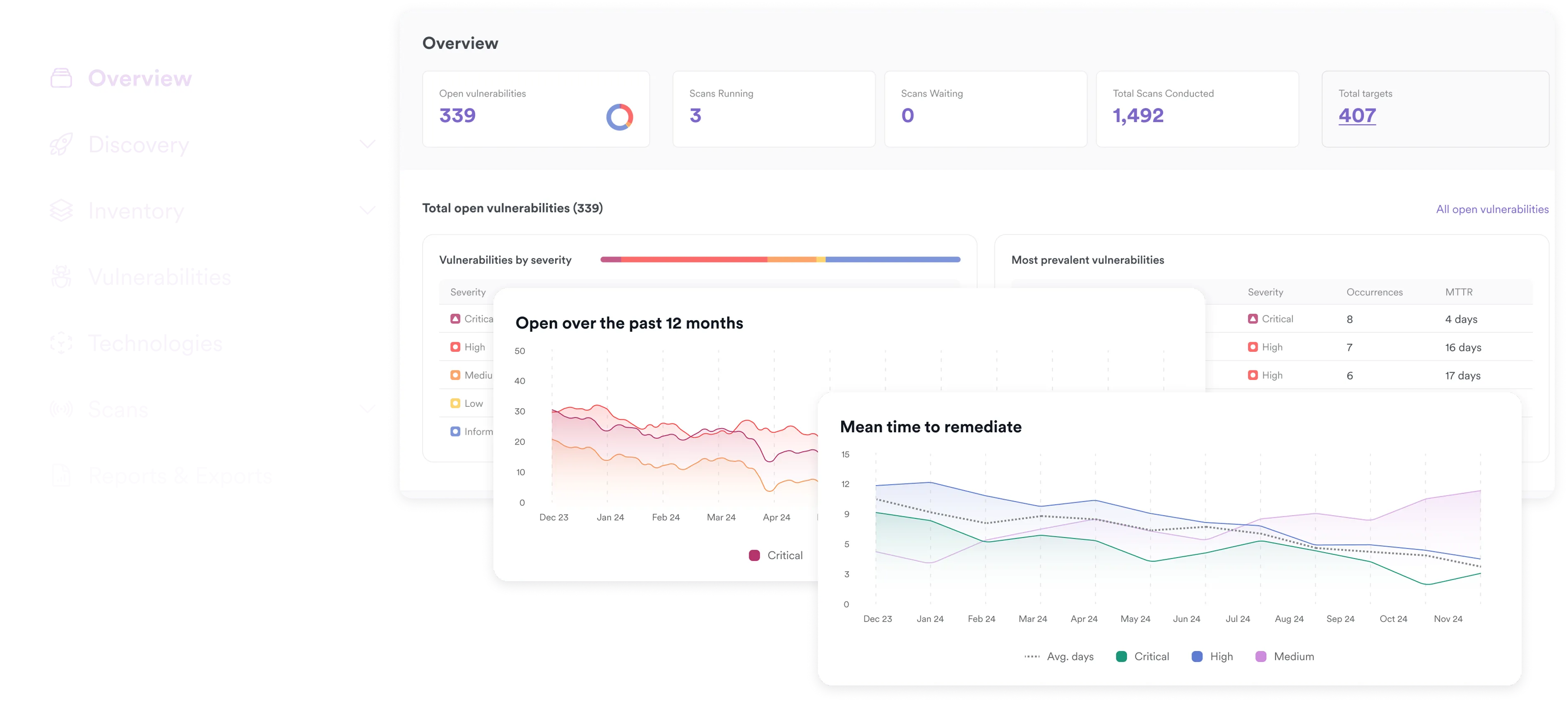
Your AppSec control center
Invicti delivers industry-best AST, leading ASPM functionality, and complete integration with all the tools you already use.
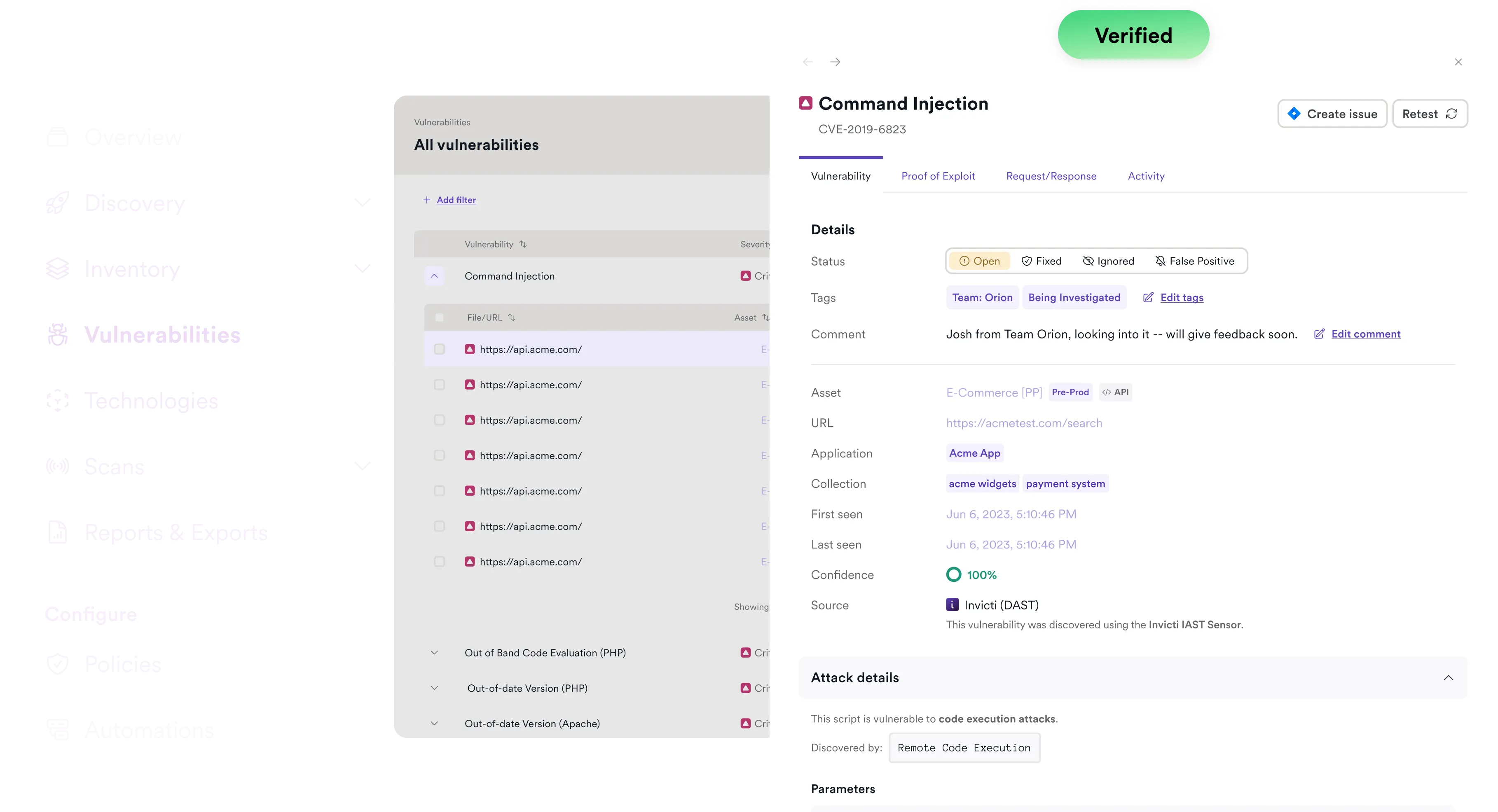
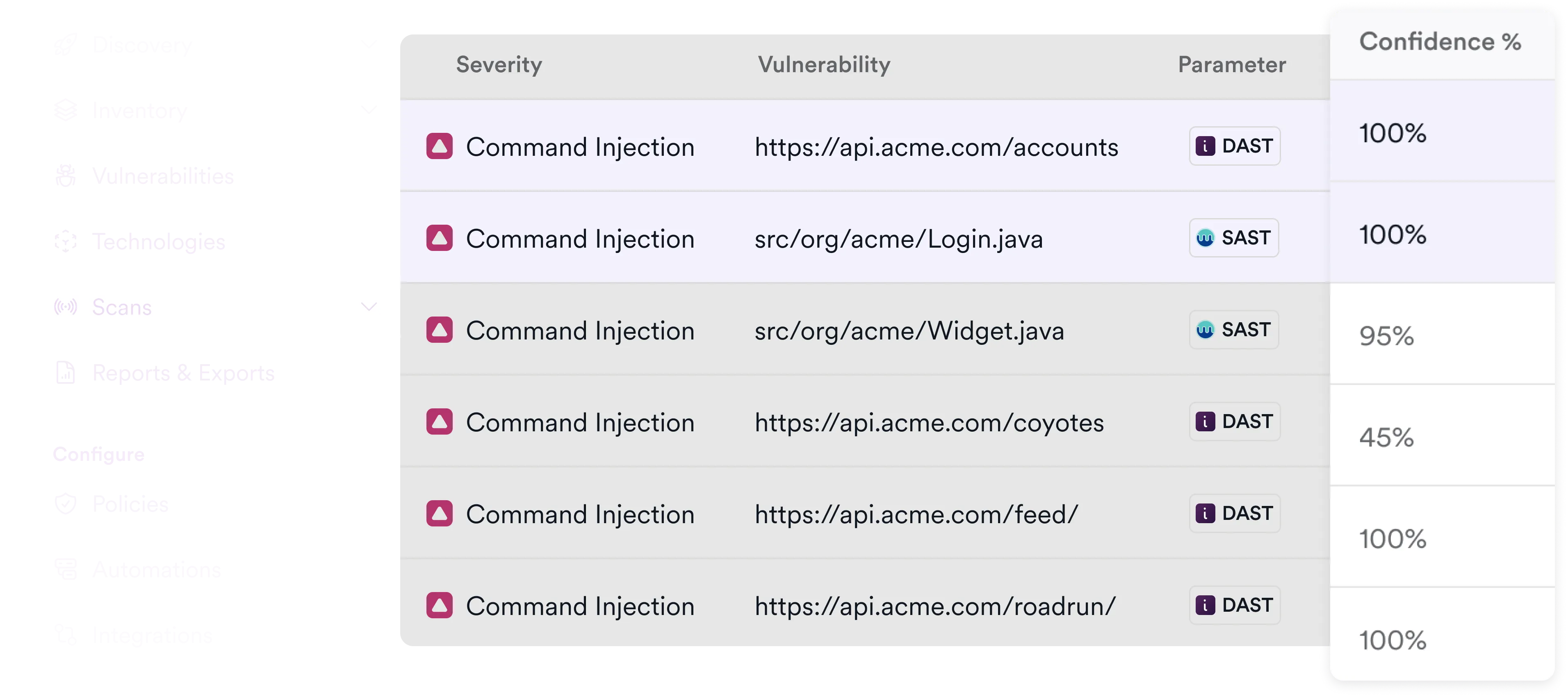
Find, prioritize, and remediate code vulnerabilities
Invicti integrates with a leading SAST provider to give teams the best of both worlds: proactive static testing of all application code, paired with the proof-based validation of DAST. It’s SAST without the noise.
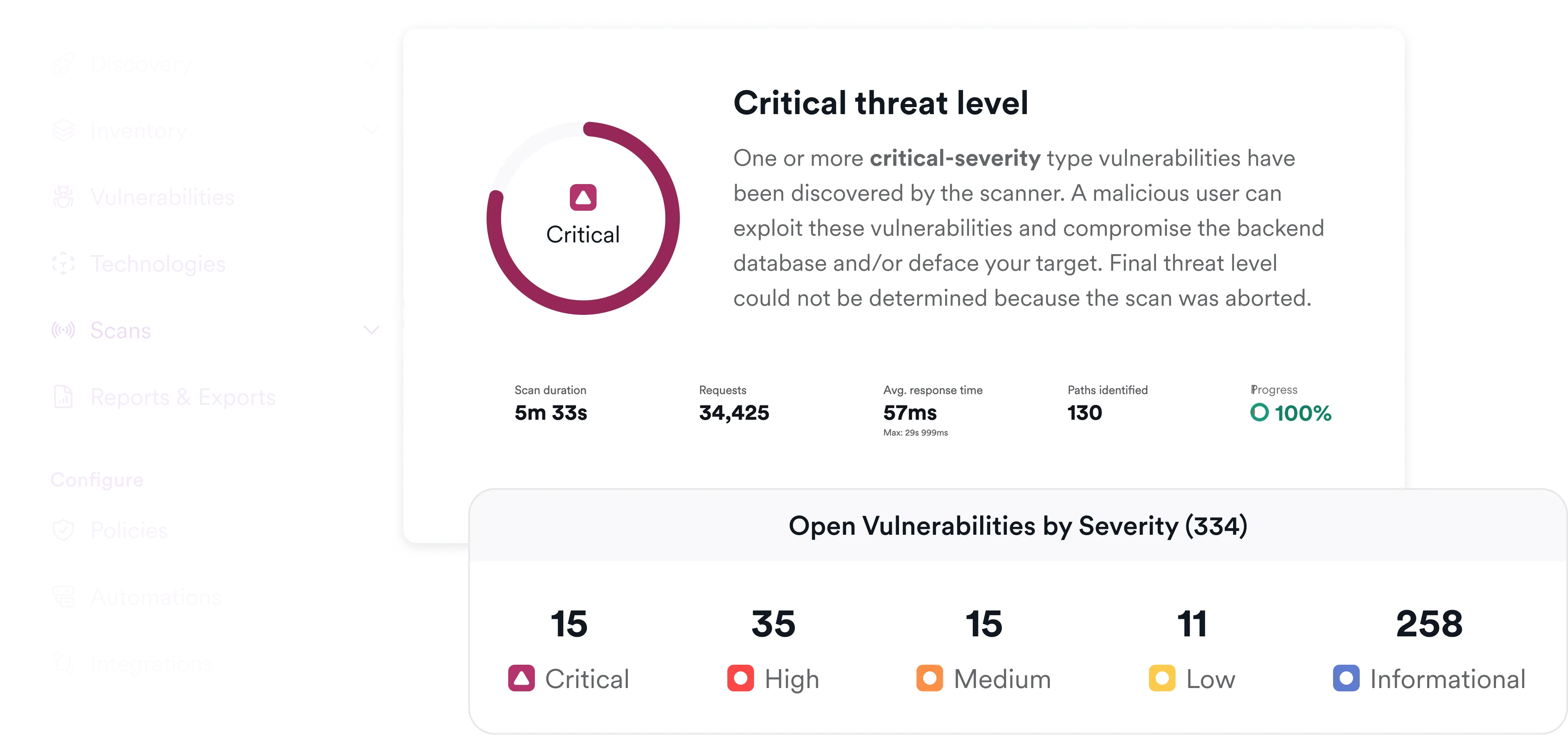
Take control of open-source risk
Invicti delivers integrated dynamic and static Software Composition Analysis, giving teams full visibility into open-source and third-party components. With runtime insight and deep code-level analysis, you get the context you need to fix issues faster.
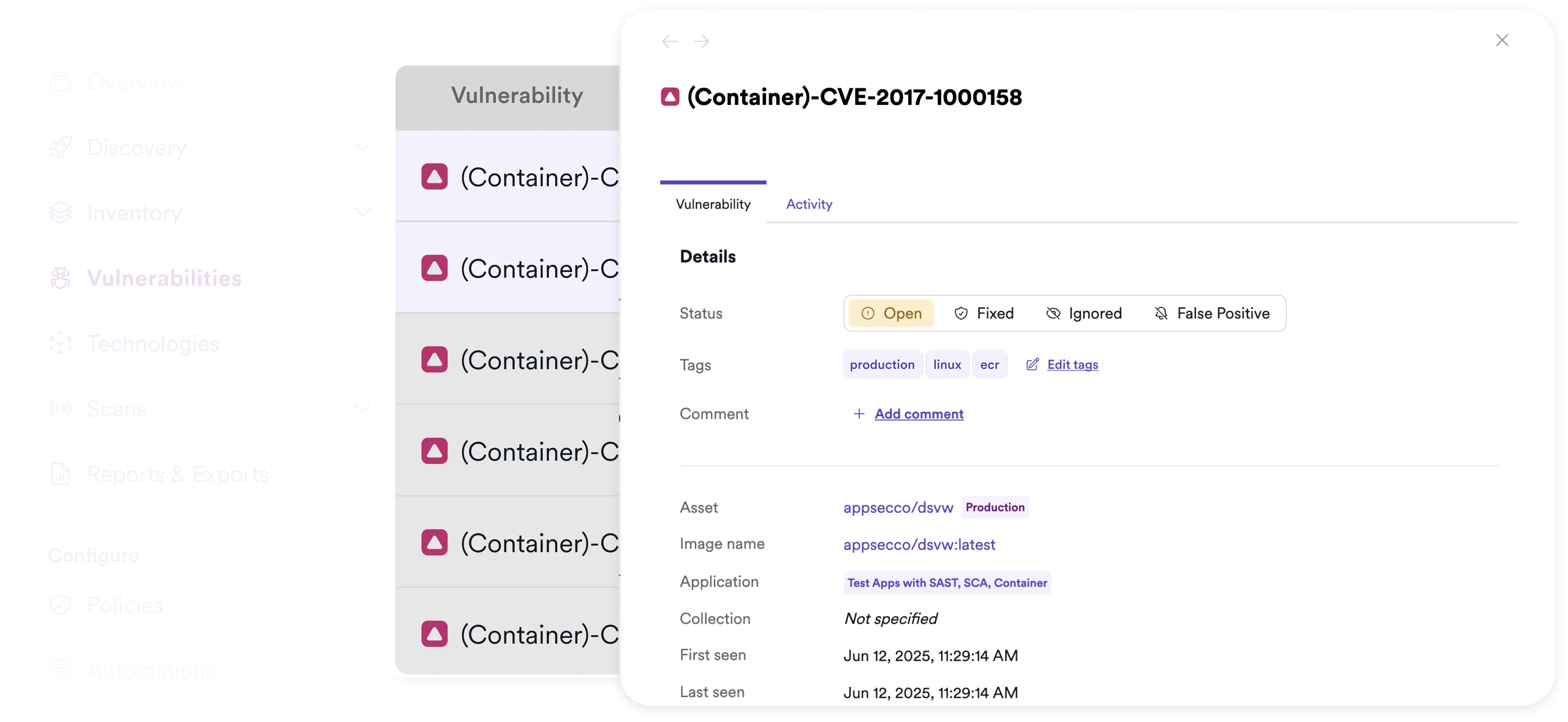
Full visibility, smarter workflows, stronger container security
Invicti supports container image scanning across popular registries and Kubernetes environments so you can spot vulnerable components early, enforce policies, and ship secure containers at scale.
The industry’s first. Still the best.
Invicti’s industry-leading DAST engine delivers proof-based scanning with an industry-best 99.98% accuracy. Fully integrated into your SDLC, it scales effortlessly across teams and portfolios.
Discover shadow APIs, reconstruct specs, scan for runtime risks
Invicti scans REST, SOAP, and GraphQL APIs with the same depth and accuracy as web apps—validating vulnerabilities with proof before they reach production. Documented or not, your APIs get full coverage, automatically.

Application security posture management (ASPM)
Invicti’s DAST-verified ASPM unifies, validates, prioritizes, and acts on AppSec risk. Get a single source of truth with policy enforcement and audit-ready reporting.
Find, prioritize, and remediate code vulnerabilities
Invicti integrates with a leading SAST provider to give teams the best of both worlds: proactive static testing of all application code, paired with the proof-based validation of DAST. It’s SAST without the noise.

Take control of open-source risk
Invicti delivers integrated dynamic and static Software Composition Analysis, giving teams full visibility into open-source and third-party components. With runtime insight and deep code-level analysis, you get the context you need to fix issues faster.

Full visibility, smarter workflows, stronger container security
Invicti supports container image scanning across popular registries and Kubernetes environments so you can spot vulnerable components early, enforce policies, and ship secure containers at scale.

The industry’s first. Still the best.
Invicti’s industry-leading DAST engine delivers proof-based scanning with an industry-best 99.98% accuracy. Fully integrated into your SDLC, it scales effortlessly across teams and portfolios.

Discover shadow APIs, reconstruct specs, scan for runtime risks
Invicti scans REST, SOAP, and GraphQL APIs with the same depth and accuracy as web apps—validating vulnerabilities with proof before they reach production. Documented or not, your APIs get full coverage, automatically.

Application security posture management (ASPM)
Invicti’s DAST-verified ASPM unifies, validates, prioritizes, and acts on AppSec risk. Get a single source of truth with policy enforcement and audit-ready reporting.

Start Here with a Medium Heading
Lorem ipsum dolor sit amet consectetur. Arcu ornare est dui est congue gravida eget euismod mi.
Seamlessly connect to your existing tools
FAQs about the Invicti AppSec platform
The Invicti Platform takes a DAST-first approach to application security, focusing on exploitable vulnerabilities in live applications rather than theoretical risks. Unlike static testing tools that generate excessive false positives, Invicti uses proof-based scanning to automatically validate vulnerabilities with proof-of-exploit, eliminating guesswork and wasted effort.
False positives are one of the biggest challenges in application security. For many common vulnerability classes, Invicti addresses this with proof-based scanning, which automatically verifies whether a vulnerability is truly exploitable. This reduces alert fatigue and ensures development teams only spend time fixing real, high-risk issues.
Application security posture management (ASPM) provides centralized visibility and risk management across security tools, workflows, and teams. Invicti delivers the industry’s first proof-based ASPM by combining its leading DAST and API security with orchestration and management capabilities. This enables enterprises to prioritize, track, and remediate vulnerabilities across all applications with zero noise.
Yes. Invicti goes beyond web application scanning to include automated API discovery and testing. This helps organizations cover hidden parts of their attack surface, ensuring both web applications and APIs are continuously identified and secured against real-world threats.
Absolutely. The Invicti Platform is built for automation and scalability, with integrations into CI/CD pipelines, issue trackers, and collaboration tools. This allows security testing to run continuously in DevSecOps environments without slowing down development, ensuring vulnerabilities are detected and remediated early.
Yes. The Invicti Platform includes software composition analysis (SCA) and container security capabilities, allowing organizations to identify vulnerable open-source libraries, outdated technologies, and insecure container images. Combined with dynamic testing, this provides both static and runtime visibility into supply chain risks for a more complete security posture.
From discovery to remediation, manage every application risk in one place.
































































