The industry’s first. Still the best.
The speed of Acunetix with the depth of Netsparker, now in one AI-powered DAST.
3600+ Top Organizations Trust Invicti
























The problem with legacy DAST
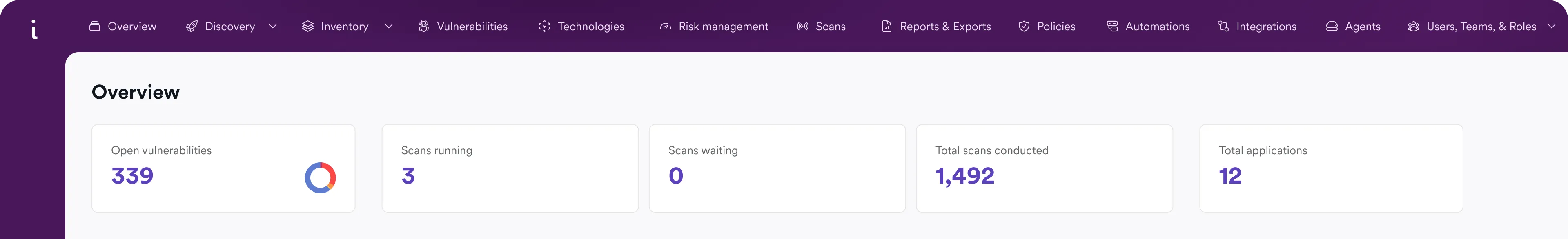
Other platforms offer bolted-on DAST solutions as an afterthought to complement their existing products. This creates a snowball effect of workflow problems and costly vulnerabilities that destabilize organizations and halt progress. Invicti's AppSec platform is built on the industry's fastest, most accurate DAST so that you can validate vulnerabilities with proof.
Constant false positives
Alert fatigue and false positives breed critical misses. 97% of DevSecOps teams ignore real vulnerabilities at least once per month.
Too slow for modern pipelines
Slow scans, broken CI/CD integrations, clunky interfaces, and manual cleanup cost organizations up to 9,760 hours a year.
Blind spots in critical systems
Most scanners weren’t built to find unknown APIs, leaving dozens of business-critical assets completely unscanned.
Proven exploitability. Zero guesswork.
Invicti’s proof-based scanning confirms many common vulnerabilities automatically by exploiting them safely and showing you the proof. When an issue is flagged, your team can trust it and fix it fast.

Built for speed. Used with trust.
Invicti fits directly into your CI/CD pipeline with native integrations for tools like Jenkins, GitHub, and Azure to deliver clean, actionable results right inside developer workflows.
.svg)
If it’s running, it’s scanned.
Invicti is built for enterprise scale, scanning complex web applications without slowing you down. It handles dynamic apps, APIs, single page applications (SPAs), and authenticated workflows with ease.
World’s best DAST, even better with AI
The industry’s leading DAST engine continues to improve with AI innovations that are closing the gap between automated scanning and manual penetration testing. Our AI innovations not only enhance DAST accuracy but also help remediate risks posed by AI-powered software and AI-aided development.
Frequently asked DAST questions
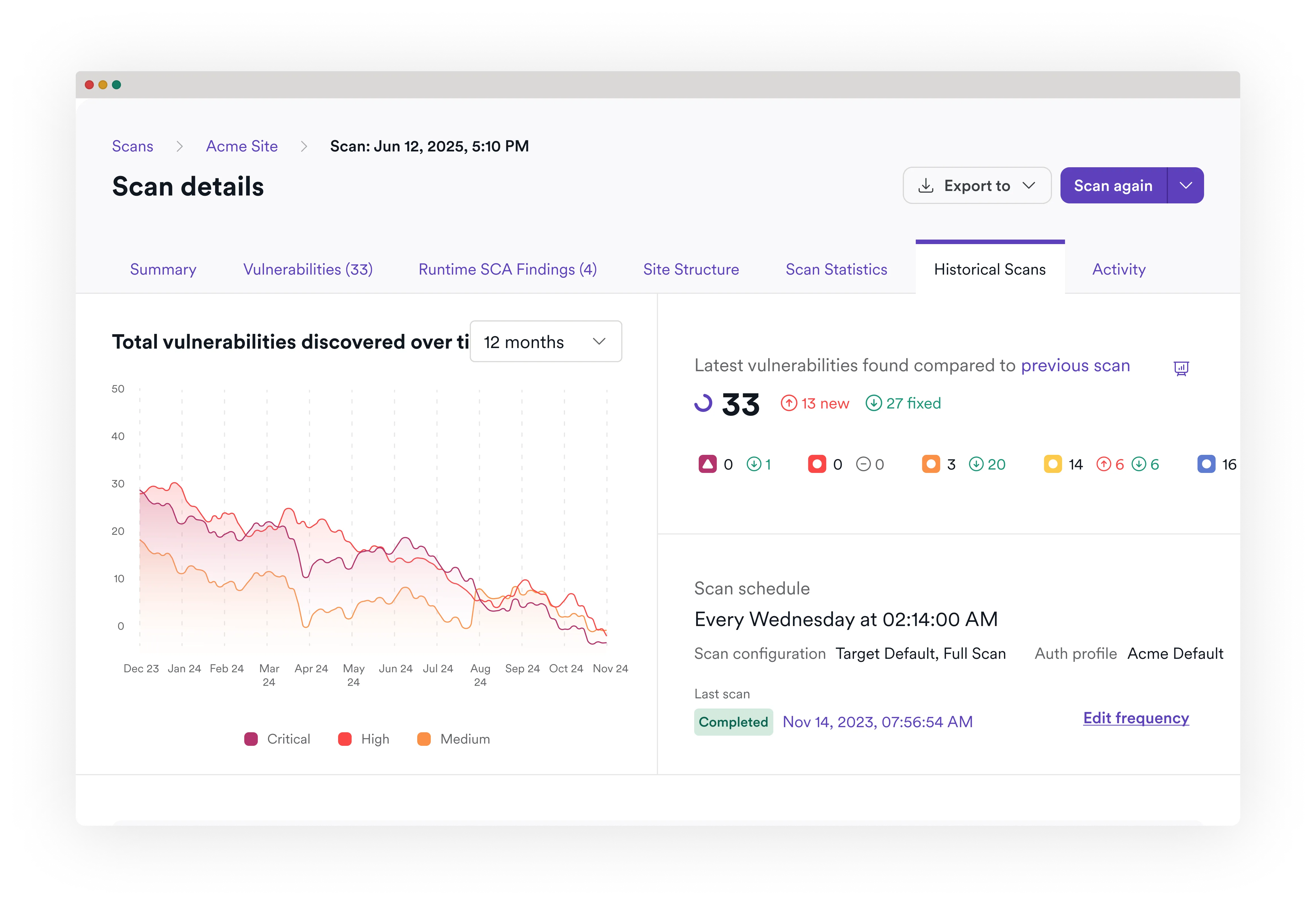
Invicti’s proof-based scanning safely confirms exploitable issues (PoE/PoC), so developers get tickets they can trust. In third-party validations and our long-term user data analysis, confirmed findings achieve 99.98% accuracy.
Yes. Invicti uses advanced checks plus proof/confirmation to surface exploitable issues first, so you don’t end up with “all config, no impact” reports. When combined with additional IAST, reports can even include stack traces or the exact query for faster fixes.
Invicti is authentication-aware and designed to scan authenticated flows (including complex login) so you get coverage where vulnerabilities actually hide, not just on your public pages.
Yes. 110+ out-of-the-box integrations plus a powerful API and open-source CLI let you orchestrate scans in pipelines, push only verified issues to work trackers, enforce gates, and re-test fixes automatically.
ASPM is only as good as its inputs. Invicti feeds runtime-validated, low-noise findings into the posture layer to de-duplicate, correlate, and prioritize what’s actually exploitable so teams fix what reduces risk fastest – all within one platform. Learn more about Invicti ASPM here.
When Invicti flags a critical vulnerability as verified (SQLi, command injection, etc.), it means it has safely exploited it in a controlled way and includes proof in the report so teams can reproduce and fix without debate. For XSS, we execute a confirmation payload within an embedded browser and attach a working PoC. Read more about how it works here.
Yes. Invicti treats APIs as first-class citizens, ingesting definitions (OpenAPI/Swagger, Postman, WSDL, GraphQL schemas), discovering unknown endpoints, understanding JSON responses, and testing real API risks mapped to the OWASP API Top 10. Learn more about API security here.
Invicti’s latest scan engine is built for speed and scale, running checks up to 8× faster in recent benchmarks against previous (already industry-leading) versions. Use scan profiles and policies to focus on what matters, schedule scans to fit release cadences, and rely on proof to minimize post-scan churn.
Absolutely. You can export the data you need from the full internal API and use built-in dashboards/metrics to track MTTR, SLA adherence, and posture trends across apps, business units, and environments – and then share executive-ready reports.
Unlike many other vendors, Invicti provides flexible licensing that matches the way you build and operate your applications and lets you scan as often as you need. Learn more about Invicti pricing here.
The only DAST that validates findings with proof-based scanning.