Netsparker Standard 5.4 – September 2019 Update
This blog post announces the September 2019 update for Netsparker Standard 5.4. The release highlights are Custom Security Checks via Scripting and HMAC Authentication Support via Scripting. Other features include Web Cache Deception Security Checks, Manual Authentication and new Send To Actions integration.

We’re delighted to announce the release of Netsparker Standard 5.4. The highlights of this release are:
- Custom Security Checks via a Scripting feature
- HMAC Authentication Support via a Scripting feature
Other new features include Web Cache Deception Security Checks, Manual Authentication and new Send To Actions integrations.

Security Checks
We have two new security checks in this release:
- Custom Security Checks via a Scripting feature
- Web Cache Deception Security Checks
Custom Security Checks
Netsparker has introduced scripting support for users to create their own custom security checks. Users will be able to implement active (send payload and analyze response), passive (analyze response), singular (runs once per scan) and per-directory (runs once per each directory/segment on web site) security checks using JavaScript programming language.
For more information, see Custom Security Checks via Scripting.
Web Cache Deception Security Checks
We have added a Web Cache Deception engine to the list of Security Checks. Web cache deception is a new web attack vector that affects various technologies, such as web frameworks and caching mechanisms. The attack takes advantage of default behaviors and poor configurations of various technologies that are involved in the application's architecture.

Authentication
We have two new authentication methods in this release:
- HMAC Authentication Support via Scripting
- Manual Authentication
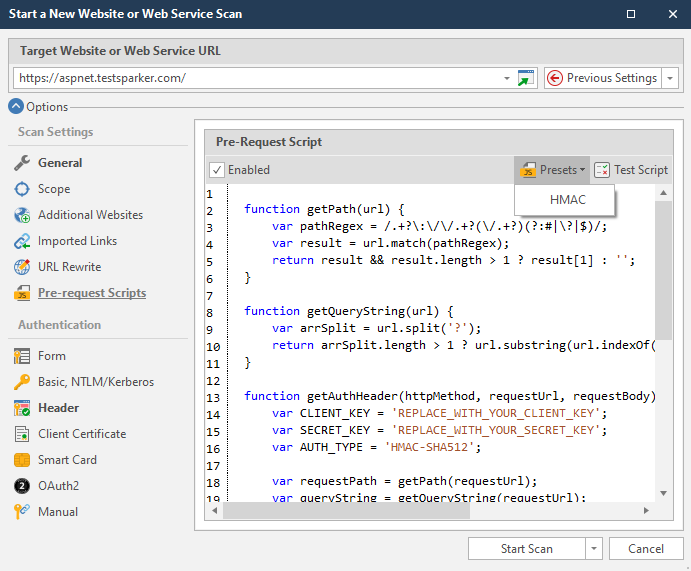
HMAC Authentication Support via Scripting
This is an authentication scheme frequently requested by customers. Users can now calculate HMAC tokens prior to each request by executing some custom JavaScript code. A scripting engine in Netsparker will execute JavaScript code. We are planning to be API compatible with Postman, since users already have the required script on their Postman environment.
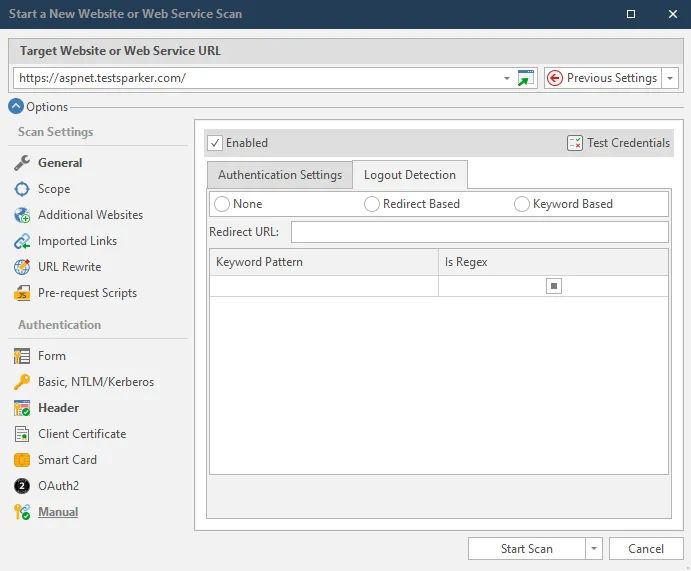
Manual Authentication
This new authentication method will allow you to import and replay your pre-recorded requests. You will be able to playback any sequence of HTTP requests prior to a scan. It will not replace Form Authentication method but will act as a backup in cases where Form Authentication may fail with the user’s web site. Netsparker will support all the Import Links formats with the new authentication method, since it will use a similar technology.
Send To Integration
Users will be able to send vulnerability details to:
- Asana
- Clubhouse
- Microsoft Teams
- Trello
- Webhook
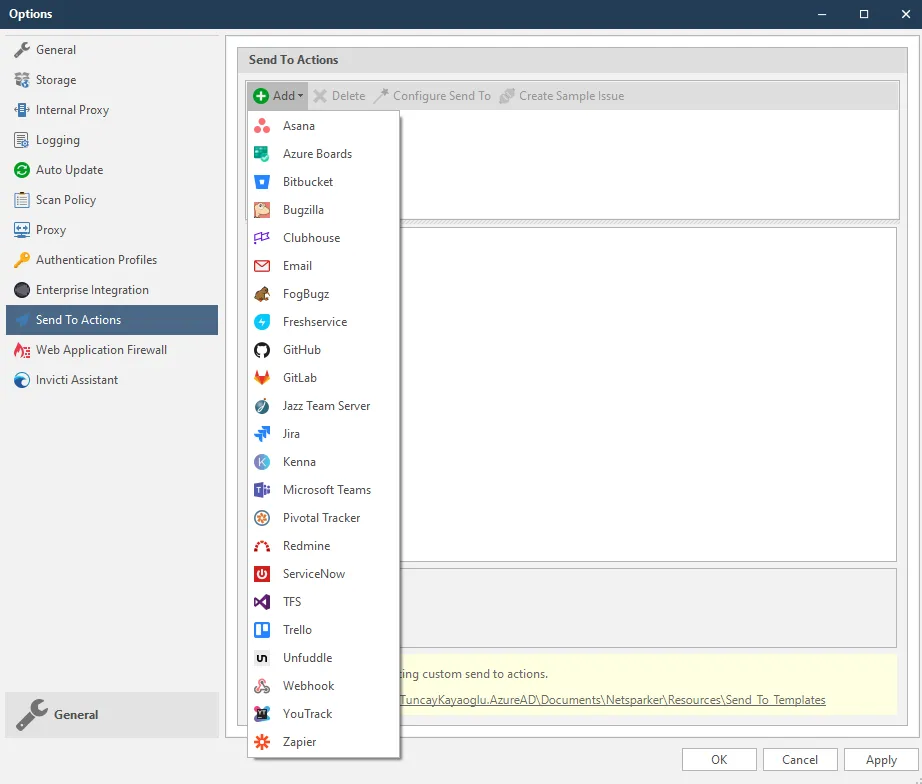
For further information on all the Send To integrations available for Netsparker Standard, see Issue Tracking Systems.
Further Information
For a complete list of what is new, improved and fixed in this update, refer to the Netsparker Standard changelog.


