Hunting down vulnerabilities with Invicti’s DAST+IAST approach
The addition of interactive application security testing (IAST) to Invicti’s highly accurate vulnerability scanning engine helps web developers to find and fix security flaws faster. In this article and demo video, we show you how easy it is to go from scan to result to bug fix – and you may be surprised at the level of detail provided by the DAST+IAST combination.
See Invicti Shark in action
Invicti automatically confirms high-impact vulnerabilities using Proof-Based Scanning to deliver detailed and directly actionable results. This helps developers to isolate the root cause of each security issue and implement an effective fix. When Invicti Shark, the additional IAST component, is installed in the application environment, the core scanning engine can pinpoint issues even more accurately to speed remediation and streamline the entire application security testing workflow.
Watch the full demo below and read on for a step-by-step journey through the process of fixing vulnerabilities such as cross-site scripting (XSS) and SQL injection using Invicti’s DAST and IAST approach.
https://youtu.be/uz6XnRnNxfU
Working with Invicti scan results
When using Invicti to check new code as part of a web development pipeline, it is easy to set up a reusable scan profile for a specific site, technology, and required scope of testing. Then you simply click Scan (if initiating scans manually) and wait for the results. Because Invicti automatically confirms the vast majority of high-impact vulnerabilities by safely exploiting them, developers can be confident that these issues are not false positives and can immediately take action to fix them.
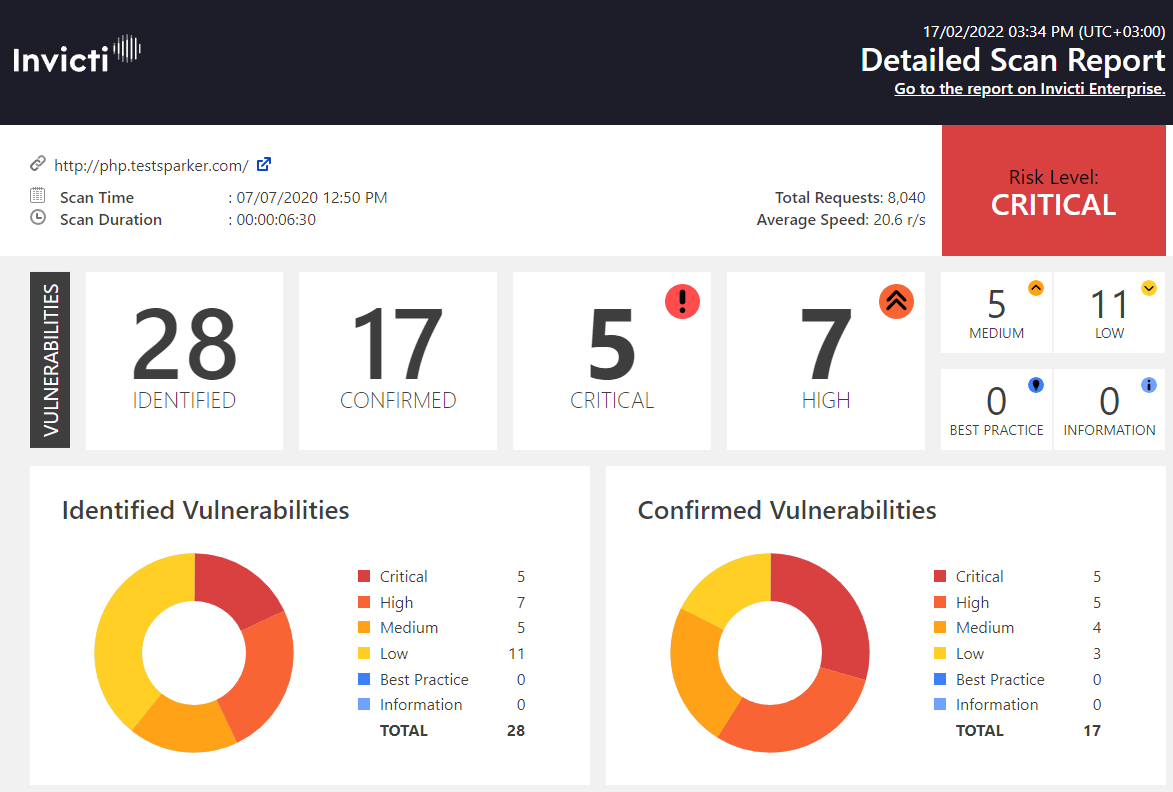
Issues are automatically triaged according to severity and you can filter them to see what needs to be addressed first. For each vulnerability, Invicti clearly shows the type and impact of the security flaw and provides clear remediation guidelines. Vulnerabilities confirmed by Invicti also include additional information about the way the flaw was exploited during testing to show that the issue is real and help pinpoint the root cause. If the IAST component is enabled, as it is in the demo, it works hand in hand with the main scanner to provide additional insight into vulnerabilities.
Finding and fixing cross-site scripting vulnerabilities
Cross-site scripting (XSS) is by far the most common class of web vulnerabilities, so Invicti detects and automatically confirms a wide variety of XSS variants (read more in the article What is cross-site scripting?). Looking at an XSS scan result, you get detailed information about the vulnerability, complete with the actual URL that was used to successfully inject JavaScript into the application during testing.
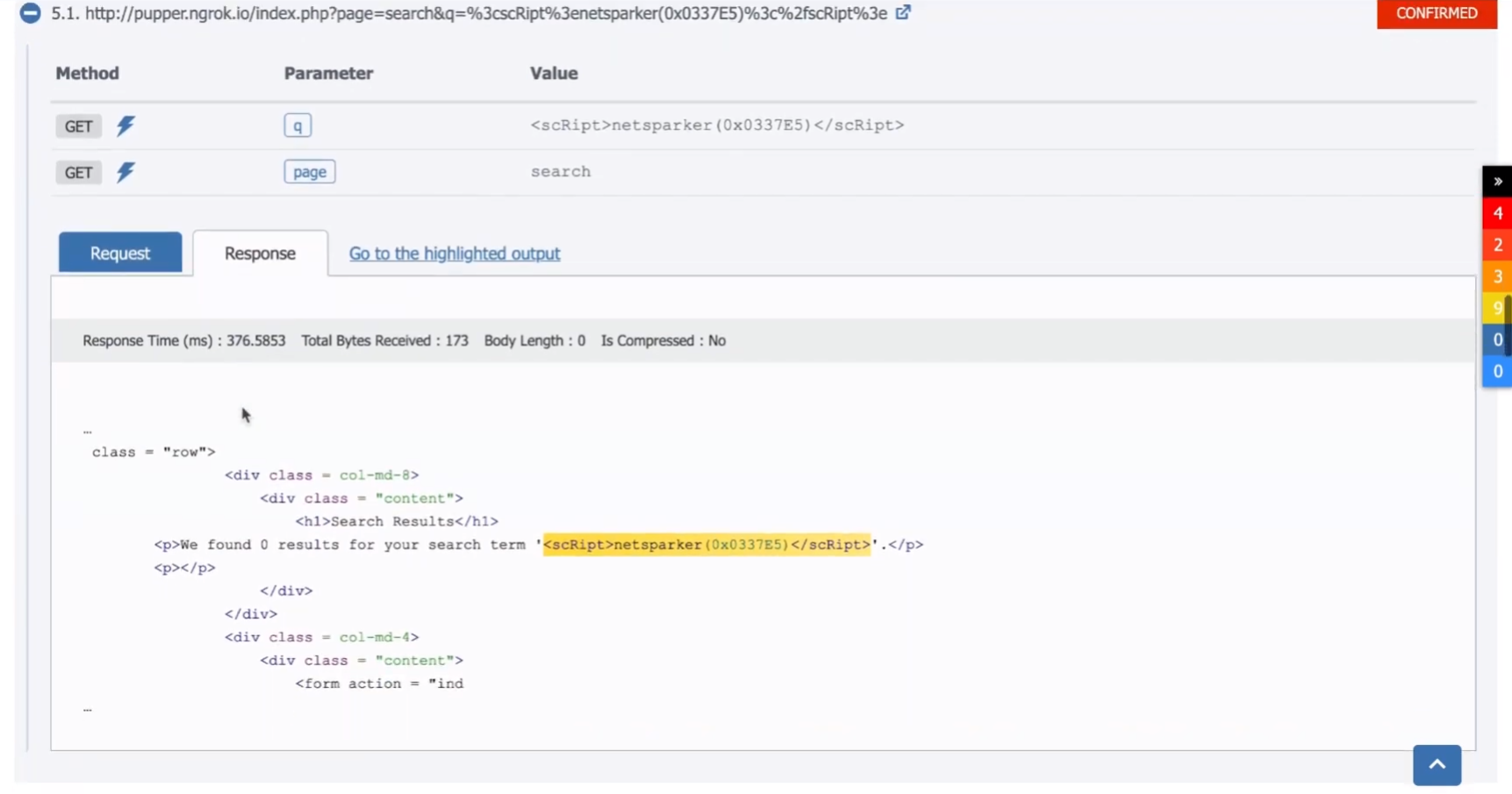
By tracing the injection back to the relevant page and parameter, you can quickly locate the vulnerable code. Invicti provides remediation guidelines to help developers quickly and effectively fix the underlying issue. For cross-site scripting, the usual cause of the vulnerability is failure to sanitize and validate user-controllable input before using it in JavaScript code. Adding proper input validation should fix the issue in most cases and this is what Invicti recommends in the report.
Dealing with SQL injection vulnerabilities
SQL injections are another high-profile category of vulnerabilities. They are especially dangerous because they allow attackers to execute database queries and as such are a major attack vector for data breaches. Invicti detects and automatically confirms such vulnerabilities, again providing the test attack URL and often also sample data extracted from the database as additional proof. Because the injection is processed on the server, Invicti’s interactive scanning module deployed in the application environment can provide valuable additional information about the vulnerability.
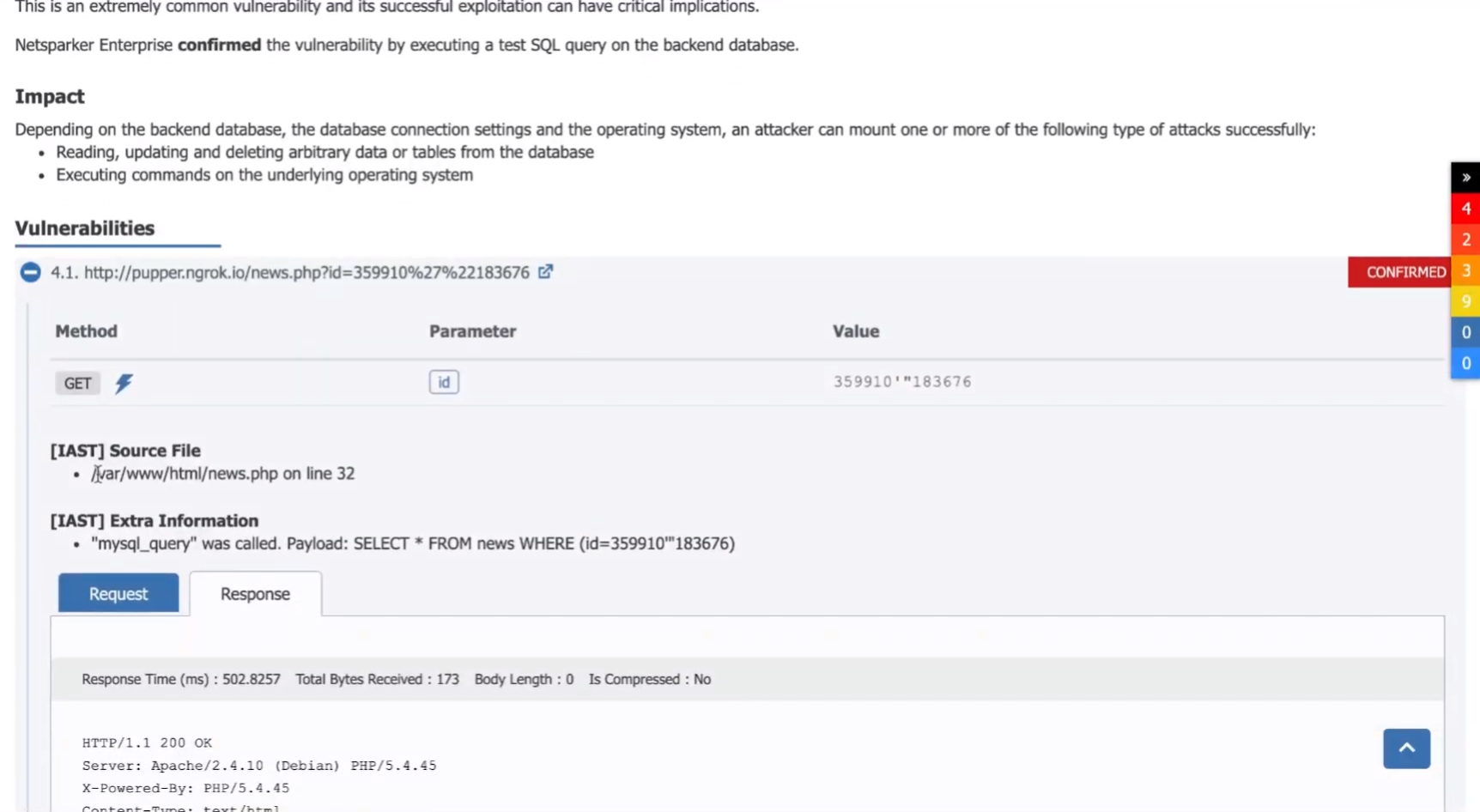
Working in conjunction with the core scanning engine, the IAST component monitors code execution to extract the database query that was executed following the injection. Depending on the application technology (PHP, .NET, and Java applications currently supported for the IAST functionality), results can contain the filename and line of code or stack trace. This makes it easy to locate the underlying issue in code and fix it, for example using parameterized queries instead of manually concatenating query strings with raw user inputs.
How Invicti ensures effective fixes
When you’ve finished fixing a vulnerability, you mark it as fixed (either in Invicti itself or an integrated issue tracker) and Invicti automatically queues it for retesting. This is a vital step in ensuring that the fix has fully addressed the vulnerability and (just as importantly) hasn’t introduced any new security issues. Partial fixes that don’t address the root cause of a vulnerability are not only bad for security but also generate lots of extra work when the same issue (or a very similar one) resurfaces in the future.
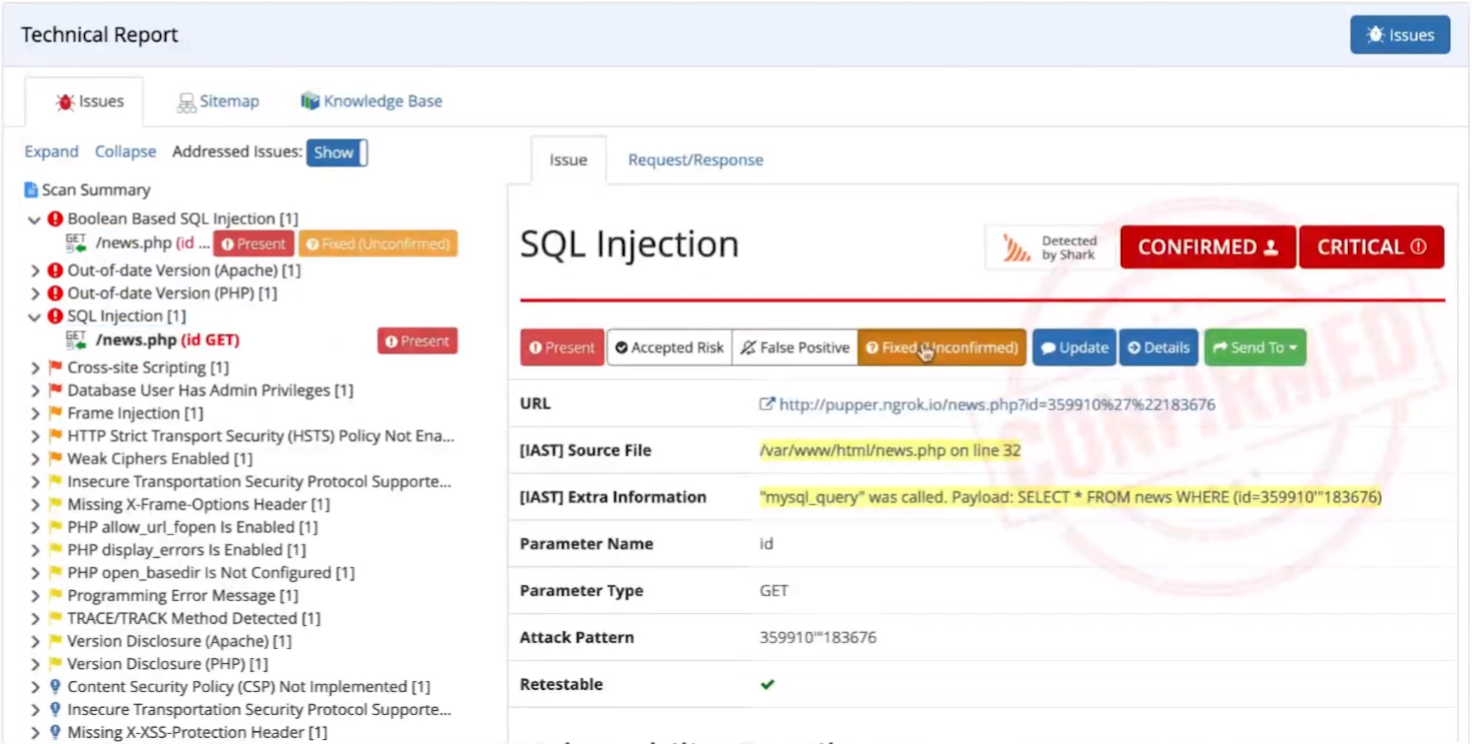
In the demo, the SQL injection was first naively fixed by blacklisting a handful of forbidden SQL keywords. Filtering user input like this is usually a bad idea because any reasonably advanced attacker (and scanner) will easily find a way to outsmart the filter. This is why Invicti can still exploit the same vulnerability upon retesting and the Fixed flag is removed. The only way to fully address the vulnerability is to use proper parameterized queries, as recommended in the technical report. With this fix implemented and restested, Invicti no longer reports any risk of SQL injection on that specific page.
How Invicti’s DAST+IAST approach speeds remediation
The main developer complaint leveled against less advanced dynamic application testing tools is that they generate lots of false positives and only vaguely indicate the location and causes of vulnerabilities. This adds a lot of extra work and frustration, leading some developers to treat security as a waste of time and a painful chore to get through rather than as a best practice to embrace.
Invicti delivers proven and actionable scan results complete with clear severity ratings and remediation guidance to help developers find, understand, and fix vulnerabilities as quickly and efficiently as possible. The additional IAST component extends these already precise results to really pinpoint issues, often down to the specific line of code. For maximum efficiency, developers can work with detailed and confirmed vulnerability reports without ever leaving their issue tracker – and this includes automatic retesting.
With Invicti in your development workflow, developers no longer need to waste time on vague vulnerability reports or security issues that always seem to come back, no matter how often you fix them. Now they get an automatic ticket, proof that the vulnerability is real, the exact location of the insecure code, and guidance on how to make the application secure and avoid similar issues in the future. Vulnerability remediation has never been so simple or so effective.


