5 reasons why proof-based scanning is a game-changer
Making decisions based on probabilities and hunches instead of solid facts is bad not just for business but also for security. Invicti DAST uses proof-based scanning to cut through the uncertainty and show which web vulnerabilities are real and exploitable. Here are 5 reasons why this changes the entire approach to application security testing.

Reason #1: Restoring trust in DAST
Dynamic application security testing (DAST) has come a very long way from the simple web application testing tools of the early 2000s. The first scanners were simple scripts and utilities to aid in manual testing across mostly static web pages. As web technologies advanced by leaps and bounds, legacy DAST products developed from the early scanners simply could not keep up, proving limited in scope, accuracy, and usefulness. This gave rise to the stereotype of DAST as a second-rate citizen in the world of application security testing – a nice-to-have rather than must-have.
Even though today’s advanced solutions represent a completely new generation of DAST scanners, users still have low expectations of automated dynamic testing and tend to be skeptical of any new claims of effectiveness. After all, every vendor claims to have higher accuracy and fewer false positives than the competition. To counter this, Invicti was built on the deceptively simple idea that to convince users a vulnerability is real, you need to deliver solid proof – and this is how proof-based scanning was born.
The real innovation is that an automated tool can identify many vulnerabilities with the same level of certainty as a penetration tester or bounty hunter. The Confirmed stamp that you see in Invicti reports for verified vulnerabilities is more than just an icon – it means that the issue is real and you can move to address it without manual verification by the security team. Quite simply, if you see Confirmed, you have a vulnerability that you need to fix. Period.
Vulnerability confirmations provided by proof-based scanning are at least 99.98% accurate. Learn how we calculated this percentage based on real-life vulnerability testing data and how accurate vulnerability scanning can translate into major savings.
Reason #2: The shift to fact-based web application security
Proof-based scanning works by safely exploiting an identified vulnerability and extracting sample data to prove that an attack is possible. It is not a gimmick or an extra feature to tick off on the list but a fundamental change in the approach to vulnerability scanning. With legacy scanners, the results were always a list of suspicious pages that someone should probably take a look at. With evidence-based automated confirmation, there’s nothing uncertain about your DAST results – they are vulnerabilities that really exist, are exploitable, and can get you hacked right now. You’re now working with security facts.
Without proof, every result from even the best DAST scan could be a false alarm until somebody checks it manually. In a large web environment, you can have thousands of issues being reported – but until they are verified, you simply don’t know your current security status or workload. Proof-based scanning cuts through this uncertainty by automatically and conclusively showing which issues are real and exploitable and cannot be false positives. This eliminates guesswork and enables the move to fact-based web application security at any scale.
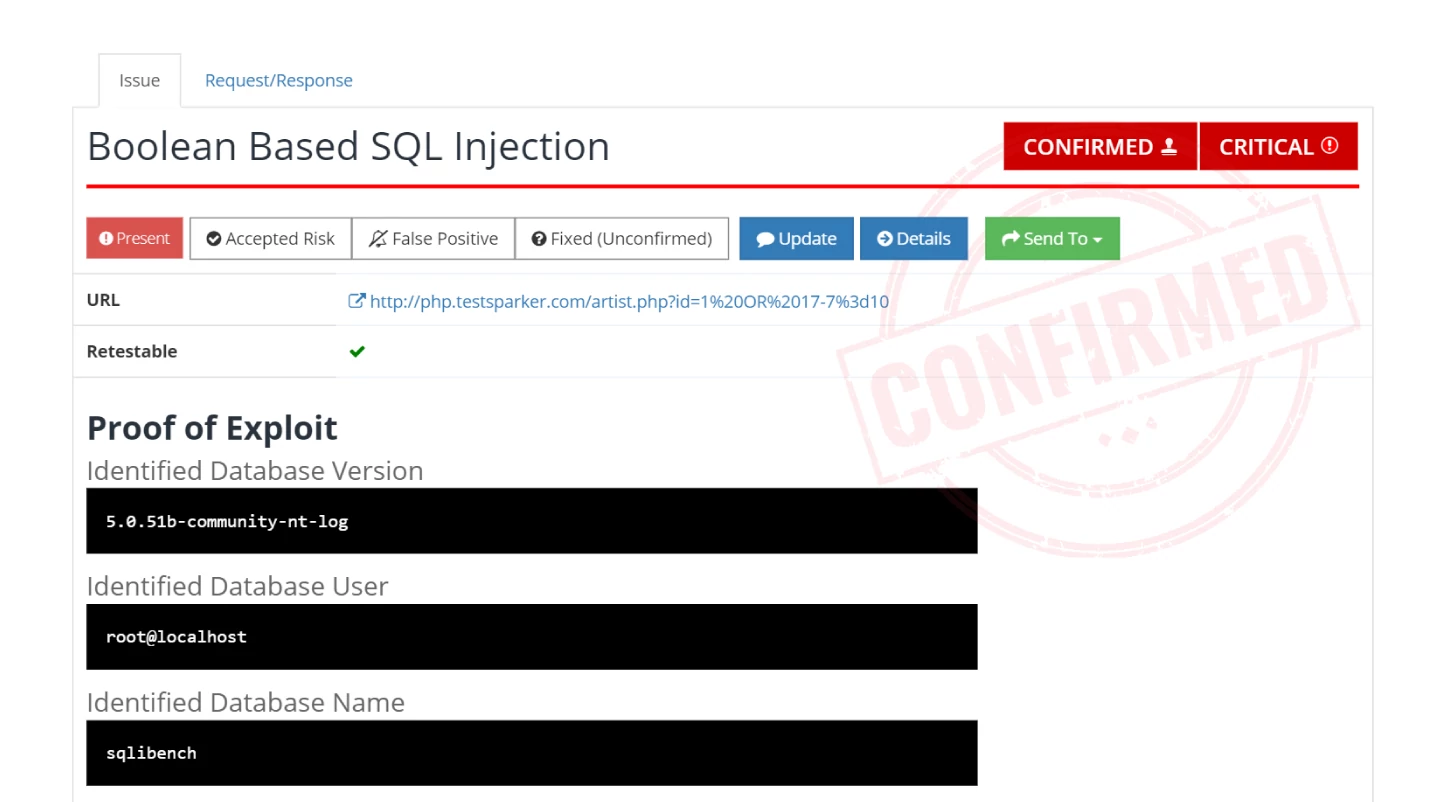
Reason #3: Accurate prioritization and planning
In any web application environment, you will get a variety of issues that differ in type, importance, and potential impact. To get measurable security improvements from day one, you need to focus your resources where they will make the biggest difference at a given time, starting with vulnerabilities that are directly exploitable and would have the greatest impact if targeted by attackers.
This is where proof-based scanning really shines. Every confirmed vulnerability that is accompanied by proof has already been safely exploited by the scanner, so you know for a fact that attackers could exploit it as well. Combined with severity ratings and technical information provided in each vulnerability report, this gives you accurate data to plan and prioritize resolution efforts for rapid time-to-value.
Proof-based scanning automatically confirms over 94% of direct-impact vulnerabilities – issues such as injections and cross-site scripting that can be remotely exploited with no additional prerequisites. See our technical white paper to learn how this is possible.
Reason #4: True automation and scalability
Modern web application development relies on automation and cloud-based scalability. Build environments, continuous integration pipelines, containerized deployments – everything is heavily automated because that’s the only way to build and operate extremely complex and dynamic environments with limited human resources. Yet when you try to add automated security testing to this mix, things don’t always mesh smoothly.
Automation is all about eliminating as much manual work as possible. So what do you do if all the results from your legacy DAST need to be verified manually before you can create developer tickets? This is where most DAST scanning products stumble, leading to the misconception that you can’t use DAST in CI/CD pipelines. Of course you can – but only if you use evidence-based scanning to ensure that only real and exploitable security issues are assigned automatically and you’re not injecting false-positive results into your development and testing workflow.
To take security automation and scalability even further, Invicti integrates with popular issue trackers out-of-the-box so automatically confirmed vulnerability reports can go directly to developers without clunky additional steps burdening the security team. You can also set up automatic fix retesting to go from security bug report to an effective fix without any manual steps by security staff. Proven and fully trusted vulnerability scan results pave the way to confident automation and true scalability.
Reason #5: Improved workflows and working relations
Last but certainly not least, proof-based scanning completely changes the developer-security team dynamic by minimizing miscommunication and back-and-forth. When a developer gets a confirmed security issue report from the Invicti solution, they can immediately see proof that the vulnerability really exists and is exploitable. They also get detailed information about the issue and its potential impact, along with full remediation guidance. This is a huge time-saver for security engineers, who can now focus on managing vulnerabilities and providing security advice rather than manually confirming, documenting, and monitoring issues.
Moving from lengthy exchanges triggered by “this code is insecure, fix it” to detailed bug reports accompanied by actual proof eliminates unnecessary communication, streamlines workflows, and greatly improves working relations. No more finger-pointing and throwing issues over the wall – now everyone works with solid data to understand root causes, eliminate vulnerabilities, and improve security in the long run. Developers get actionable tickets so they can quickly fix security bugs and focus on building better software, while security testers can concentrate on more complex vulnerabilities that really need human expertise and intuition.
Always demand proof
There are lots of vulnerability scanners on the DAST market and vendors are all making similar claims about accuracy, low false positives, great coverage… It can get pretty confusing out there. At Invicti, we value straight talking. When we say a vulnerability is confirmed and proven, the issue is definitely real – and we know because we have already safely exploited it. Here is your bug, here is your proof, go fix it. Web application security doesn’t get any simpler.
To see how Invicti eliminates uncertainty with 99.98% accuracy and learn the inner workings of proof-based scanning, get the full Invicti technical white paper: How Invicti Generates Proof to Avoid False Positives.


