Invicti (formerly Netsparker) vs. Tenable Nessus | Comparison
Network security and vulnerability management should be a part of any cybersecurity strategy – but first and foremost, you need an accurate web vulnerability scanner such as Invicti to help you find and quickly fix vulnerabilities in your web applications and APIs.
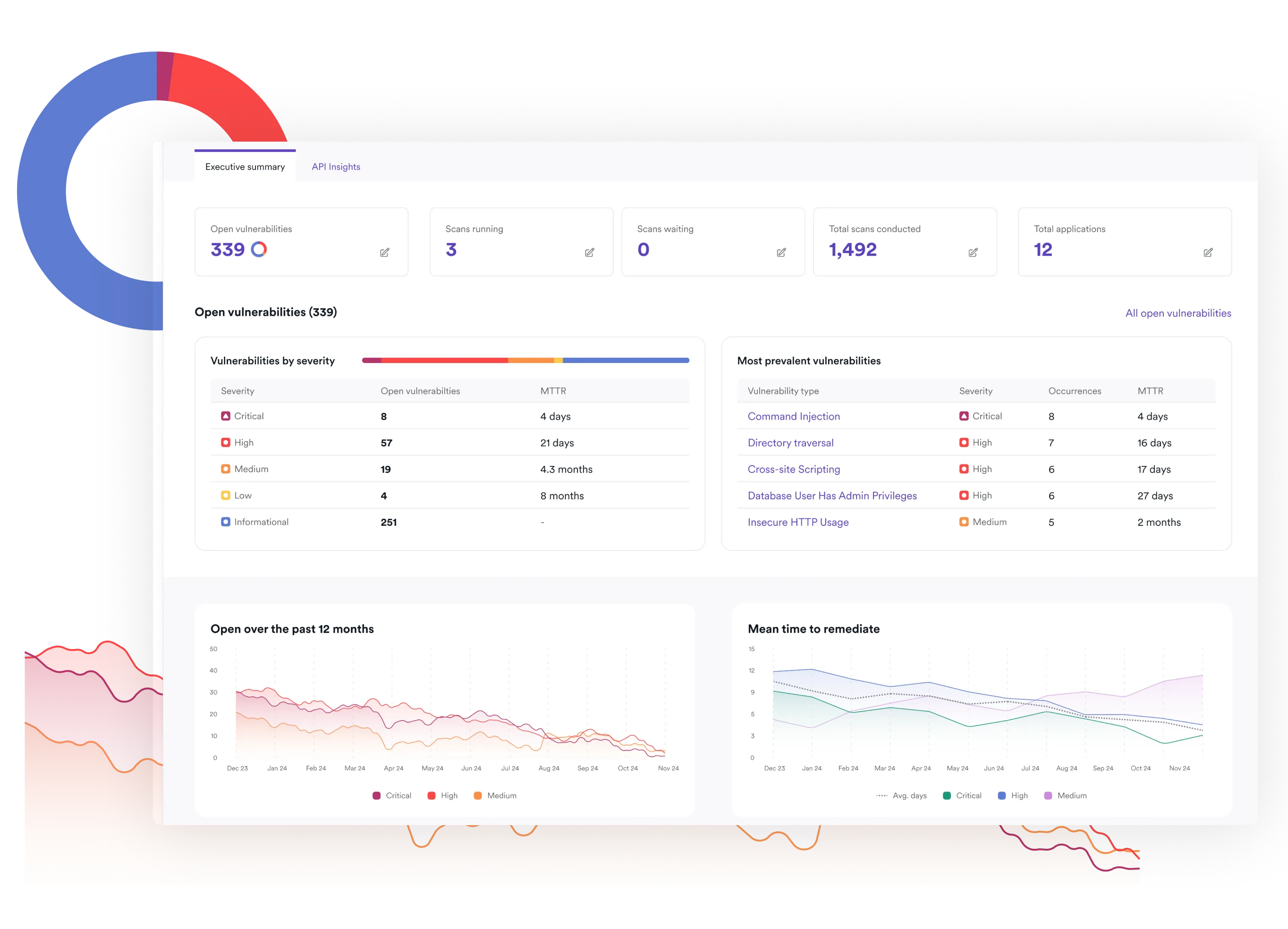
Invicti vs. Tenable Nessus at a glance
- Web application security vs. network vulnerability assessment
- Testing for web application and API vulnerabilities is a must
- Invicti focuses on accuracy and remediation
- Industry-leading DAST with proof-based scanning and workflow integrations
Web application security vs. network vulnerability assessment
When considering security testing tools, the first thing to ask yourself is: what are you planning to test? Year after year, the Verizon Data Breach Investigations Report reminds us that flaws in web applications are the most common cause of data breaches. If you don’t want to become the next breach headline, your cybersecurity program needs a high-quality web vulnerability scanner – a purpose-built solution that can automatically and regularly test the security of your web applications and API endpoints. And if you’re looking for the best, you want Invicti (formerly Netsparker).
Unlike Invicti, which is a dedicated application security testing platform, Tenable Nessus focuses on network vulnerability assessment. Network vulnerability scanners like Nessus serve an important purpose in a security testing program but do not provide a complete picture because they mostly focus on network security. Network-level testing will not tell you whether your applications are vulnerable to common web attacks such as SQL injection. Invicti, on the other hand, provides a mature solution for dynamic application security testing (DAST) that lets you perform automated web vulnerability scanning with a full embedded browser engine.
Testing for web application and API vulnerabilities is a must
Network scanners like Tenable Nessus can perform a few high-level checks related to your web presence, such as identifying vulnerable versions of web servers or known open-source platforms, but this is only scratching the surface of your web security posture. To check if your websites and applications could be compromised by attackers, a web application scanner is specifically equipped to map out all web pages and user inputs. Unlike a network scanner, it offers thorough vulnerability tests for security vulnerabilities such as cross-site scripting (XSS), SQL injection, remote file inclusion (RFI), and more.
Invicti combines web asset discovery and advanced crawling with web application scanning and API security testing. As a DAST-based security platform that also provides optional IAST and dynamic SCA functionality, Invicti is the automated counterpart to manual penetration testing. At the same time, it also identifies security misconfigurations and outdated web technologies, much as a network scanner would when pointed at a web server. A web vulnerability scanner can run automatically or on demand to keep testing your web attack surface in between manual tests and automatically submit any identified security issues for fixing – but that requires accuracy.
Invicti focuses on accuracy and aiding remediation
So you know you need a web application vulnerability scanner. The market is crowded with commercial Invicti alternatives such as Burp Suite for penetration testing, bundled products from Rapid7 and Qualys, or a basic web application scanner from Tenable (formerly called tenable.io). There are also open-source web security scanners such as OWASP Zed Attack Proxy (ZAP) and w3af. How do you choose?
The ultimate goal of web vulnerability scanning is not to run a scan and tick a box – it is to improve your web security posture. While “DAST-lite” products exist that claim to find many of the same vulnerability types, the accuracy and maturity of Invicti’s security checks makes all the difference in finding exploitable issues and automatically getting from scan results to actionable tickets – without drowning your developers and security teams in false positives. This is possible by automatically confirming many vulnerabilities using proof-based scanning, with each report including not only proof that a vulnerability is exploitable but clear guidance on where and how to fix it.
Industry-leading DAST with proof-based scanning and workflow integrations
Unlike many competitors who treat DAST as an afterthought or minor plug-in to their main product, Invicti provides a mature and full-featured DAST-based platform for security testing. Designed with software development lifecycle (SDLC) integration in mind and incorporating nearly two decades of experience from building the Acunetix and Netsparker scanners, Invicti delivers a DAST tool that’s been proven to work with modern web apps and APIs, in agile development workflows, and at an enterprise scale:
- Accurate security checks for all major web vulnerability classes, including SQL injection, cross-site scripting (XSS), server-side request forgery (SSRF), and more (including out-of-band detections)
- Automatic vulnerability confirmations with proof-based scanning to safely and confidently indicate exploitable issues
- Over 50 built-in integrations with popular issue trackers, CI/CD pipelines, vulnerability management tools, and collaboration platforms for workflow automation
- Support for popular authentication methods (including SSO with OAuth2) for maximum test coverage across web apps and APIs
- Optional server-side agents to add interactive application security testing (IAST) and dynamic software composition analysis (SCA)
- Available as a cloud-based SaaS solution, an on-premises installation, or a combination of both (central SaaS with locally-installed scan agents)
Web scanner comparisons
In the 2018 independent web vulnerability scanners comparison, Invicti, formerly Netsparker, was the only scanner to identify all vulnerabilities and to report zero false positives.

Detect more vulnerabilities
When tested in third party benchmarks by security industry experts, Invicti, formerly Netsparker, identified all direct impact vulnerabilities, surpassing all other solutions. Their results show Invicti, formerly Netsparker, has the most advanced and dead accurate crawling & vulnerability scanning technology, and the highest web vulnerability detection rate.
Tenable Nessus and Invicti are two different types of tools for different purposes. Tenable Nessus is a network scanning and vulnerability assessment tool, while Invicti is a full-fledged web application security testing platform to help you find and fix security vulnerabilities that are a common part of data breaches, such as SQL injection.
Read more about the MOVEit Transfer attacks that included SQL injection in the attack chain
No, Tenable Nessus is a network scanner and vulnerability assessment tool used to find outdated or insecure components in your application environments. It does not test web applications and APIs for vulnerabilities.
Read more about the importance of including API vulnerability testing in your web security program
Network security tools focus on finding misconfigurations and known vulnerable products and components corresponding to reported CVEs. Application security testing tools look at the running application (for dynamic testing aka DAST) or its source code (for static testing aka SAST) to find security weaknesses that could result in exploitable vulnerabilities. Advanced DAST products can identify both known vulnerabilities (CVEs) and unknown weaknesses (CWEs).
Read more about the difference between CVEs and CWEs
3600+ Top Organizations Trust Invicti
























Save your security and development teams hours each day.






