Automate your external vulnerability scanning with Invicti
Automatically test your entire web attack surface for exploitable vulnerabilities in web applications and APIs to reduce the risk of data breaches.

3600+ Top Organizations Trust Invicti


























Continuously scan your web applications and APIs to minimize risk
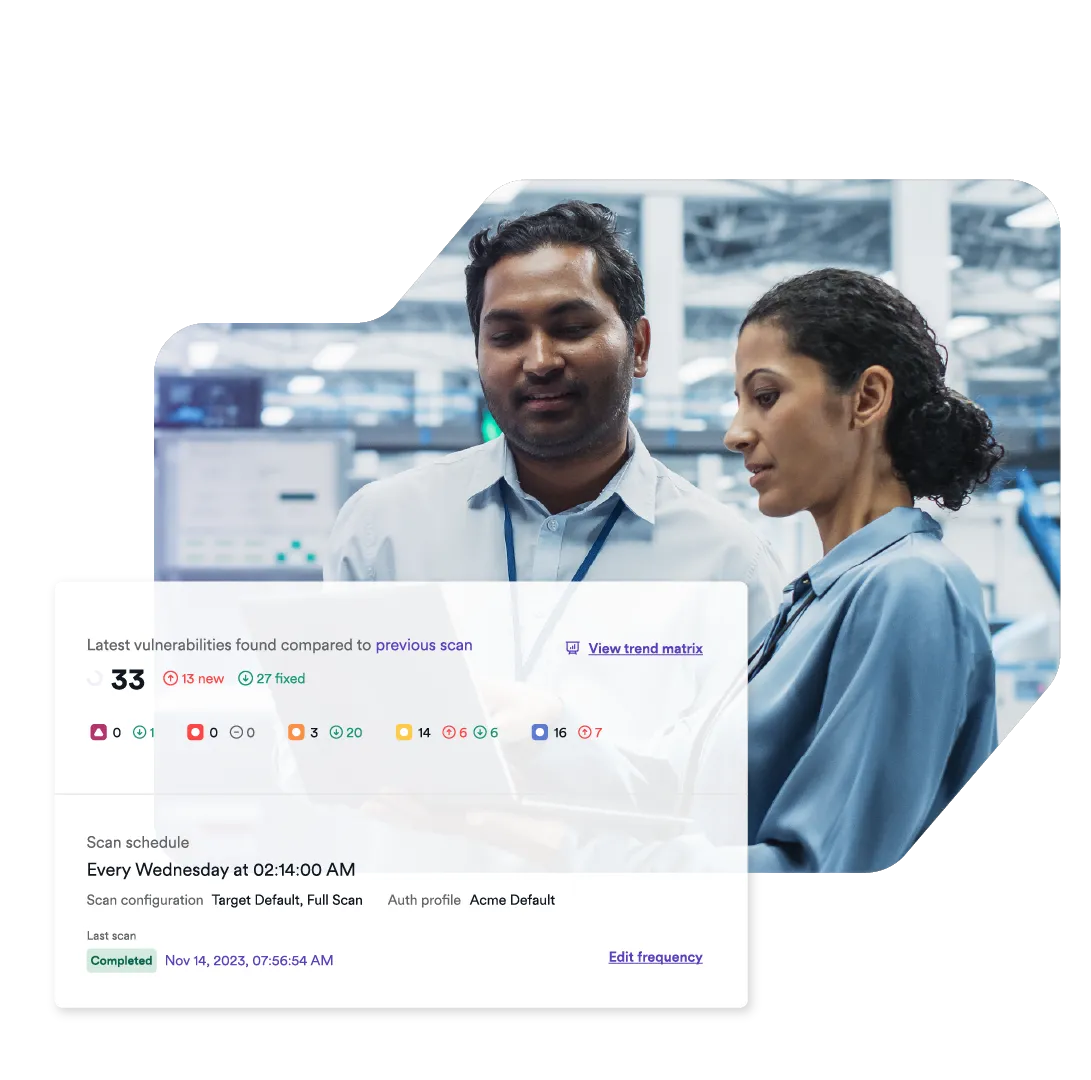
Web assets are under constant attack from cybercriminals, making continuous external vulnerability scanning critical to minimize the risk of data breaches. Invicti provides a dynamic application security testing (DAST) solution for web vulnerability scanning across entire web environments, including websites, web applications, and APIs:
- Run ad-hoc or scheduled scans on all your web assets or on predefined asset groups to automatically identify known and new vulnerabilities.
- Use built-in vulnerability management and prioritization features to guide remediation, with built-in reports to cover PCI DSS, HIPAA, and other security standards.
- Integrate the vulnerability scanner into JIRA and other popular development tools to send accurate vulnerability reports directly to developers.

Maximize visibility into your attack surface with advanced crawling and discovery
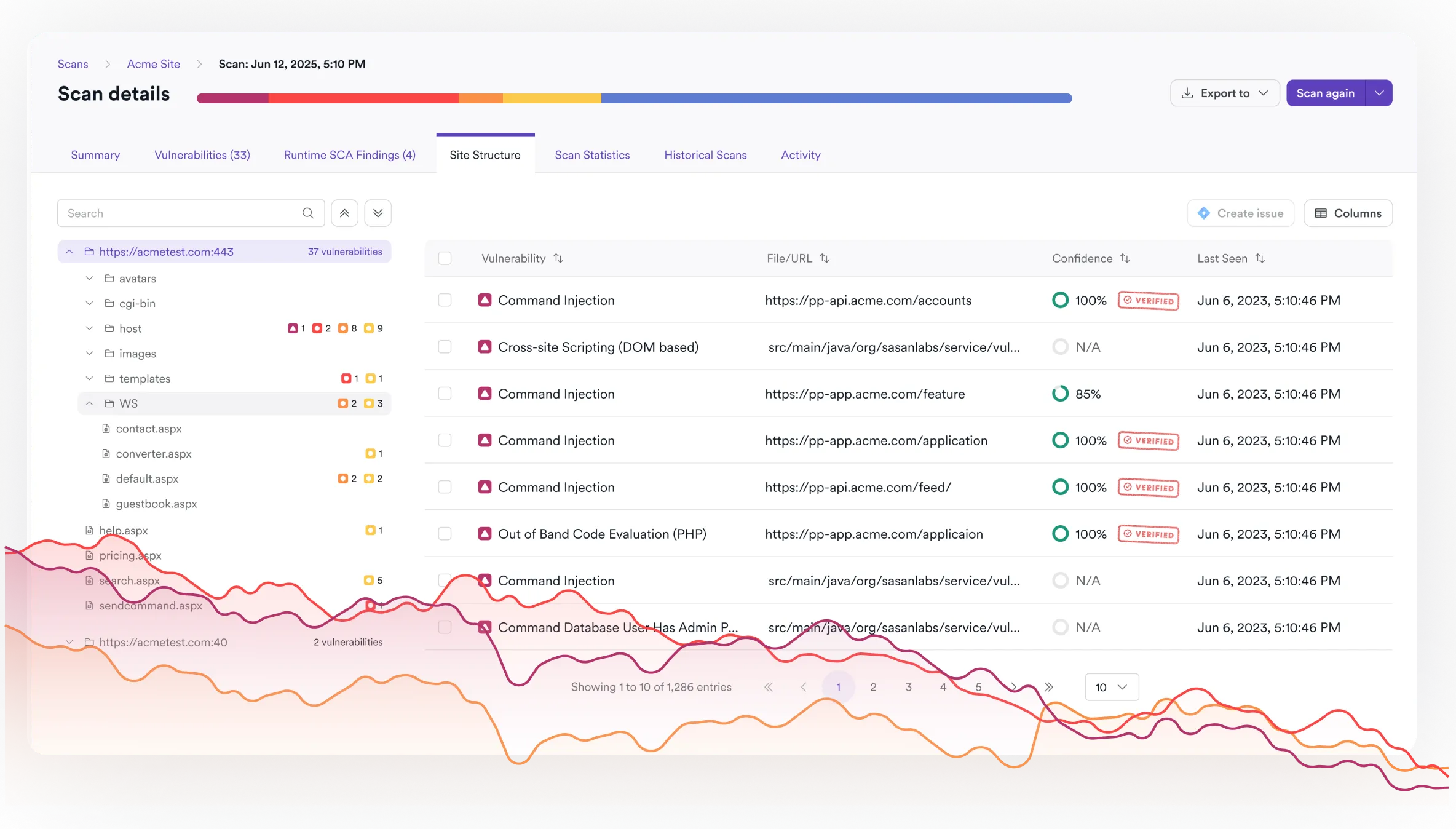
You can’t secure what you don’t know about, so Invicti’s industry-leading scan engine is combined with a built-in web asset discovery service and an advanced crawler. Web apps and APIs identified during discovery, crawling, and manual setup are automatically and safely scanned for hundreds of types of vulnerabilities:
- Automatically find SQL injection, cross-site scripting (XSS), directory traversal, command injection, remote file inclusion, and other exploitable security vulnerabilities.
- Run authenticated scans on web applications and APIs to maximize test coverage (including support for SSO with OAuth2).
- Identify security misconfigurations and outdated web technologies, with the option of adding server-side visibility through agent-based IAST and dynamic SCA.

Scale your web application security with the accuracy of proof-based scanning
When dealing with hundreds of apps and thousands of scan results, often from multiple vulnerability scanning tools, deciding where to take action requires accuracy and ruthless prioritization. Invicti uses proof-based scanning to automatically confirm the majority of high-impact vulnerabilities. Confirmed issues have been safely exploited by the scanner, so they cannot be false positives – they are remotely exploitable and you need to address them before they are targeted by malicious hackers:
- Rely on accurate automation combined with remediation guidance to smoothly scale vulnerability scanning as your application development grows, even with a small security team.
- Use the same scanning process to cover any new website or application that can run in a modern browser, regardless of the specific technologies or frameworks. This includes JavaScript-heavy single-page applications (SPAs).
- Use Invicti in a deployment model that suits your business and growth, whether cloud-based (SaaS), on-premises, or a combination of the two.
A web vulnerability scanner runs security checks in the application layer, sending HTTP requests to test websites, apps, and APIs for vulnerabilities. Network vulnerability scanners are used to probe external and internal networks for open ports and detect applications and operating systems with known vulnerabilities.
Read more about the difference between web security and network security
External vulnerability scanners are cybersecurity tools that test the external attack surface of a system or app. For websites, web applications, and APIs, external vulnerability scanning is done using dynamic application security testing (DAST) tools.
Read more about dynamic application security testing (DAST)
Ideally, you should use both types of testing. External vulnerability scanners are automated tools that can test thousands of targets and run fully autonomously if needed. Manual penetration testing by security experts is far slower and more expensive but can find advanced security vulnerabilities that scanners might miss.
Read more about vulnerability scanning vs. penetration testing
Yes, Invicti can find both known and new vulnerabilities in web applications. The core security scanner comes with hundreds of security checks to identify exploitable weaknesses by safely simulating attacks and analyzing app reactions. This is accompanied by a vulnerability database of products with known vulnerabilities (CVEs) that are also reported when identified during a scan.
Read more on how Invicti finds vulnerabilities
Featured Content

Does having a PCI compliant website and business means they are bulletproof, or better, hacker proof? This first part of this PCI compliance article looks into…

Run automated PCI DSS vulnerability scans with Invicti to automatically identify security vulnerabilities in your web applications, and fix them to…

As we have seen in part 1 of PCI Compliance, the Good, the Bad and the Insecure, PCI compliance is a good idea in abstract, however it should be…

When it comes to compliance, especially as it relates to web application security, the Payment Card Industry Data Security Standard (PCI DSS) is usually the main…

Businesses are focusing on web security to ensure the web & cloud based services they use are secure. Web application security is not easy…

An accurate and automated web server security software is vital to the security of your web applications, because the web server itself also needs to be secured…



