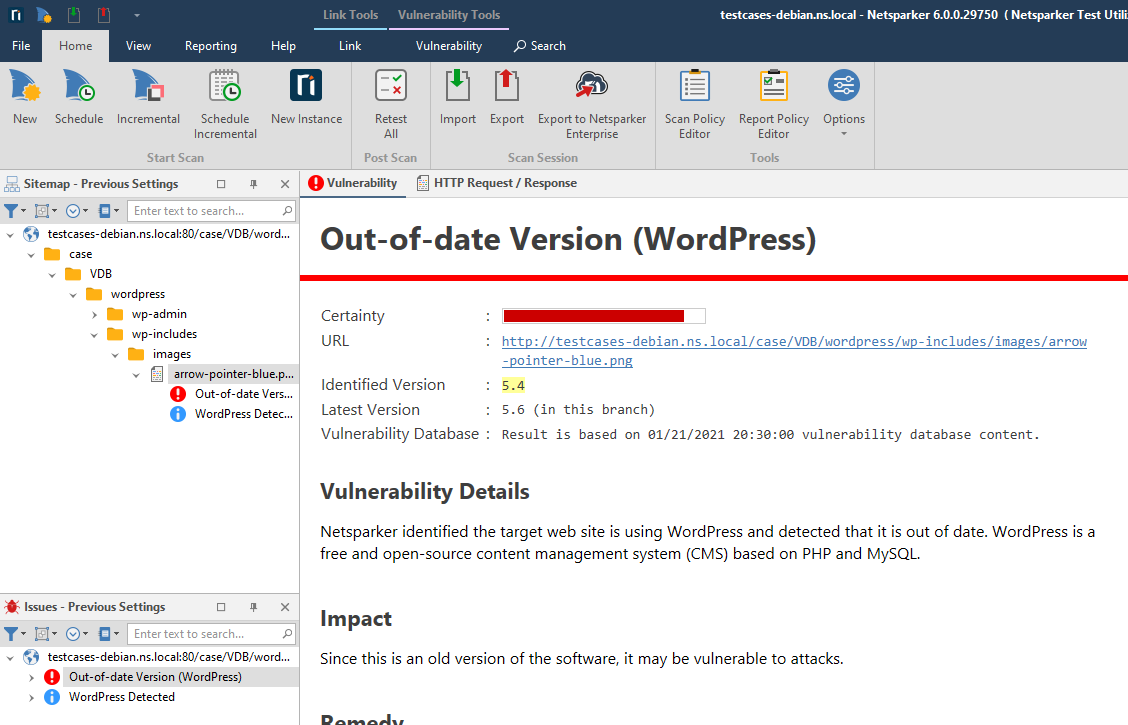
Fingerprinting libraries
Many applications, third party libraries and frameworks have filenames, copyright notices and other characteristics that are unique – like a fingerprint. It's therefore possible to 'fingerprint' libraries and find out exactly which ones are in use in an application, by looking at these unique characteristics.
The Importance of Keeping All JavaScript Libraries Up to Date
Like any other software component, JavaScript libraries can have their own security issues. Unless the JavaScript libraries you use in your web applications are kept up-to-date, your web application could be vulnerable to known attacks.
Invicti’s JavaScript Libraries Fingerprinting Engine
Both the Invicti Enterprise and Invicti Standard editions include a JavaScript Libraries engine. It identifies the JavaScript libraries used in a target web application, and their version. If an outdated JavaScript library is identified, Invicti creates an Issue and reports the vulnerabilities associated with that version of the library.
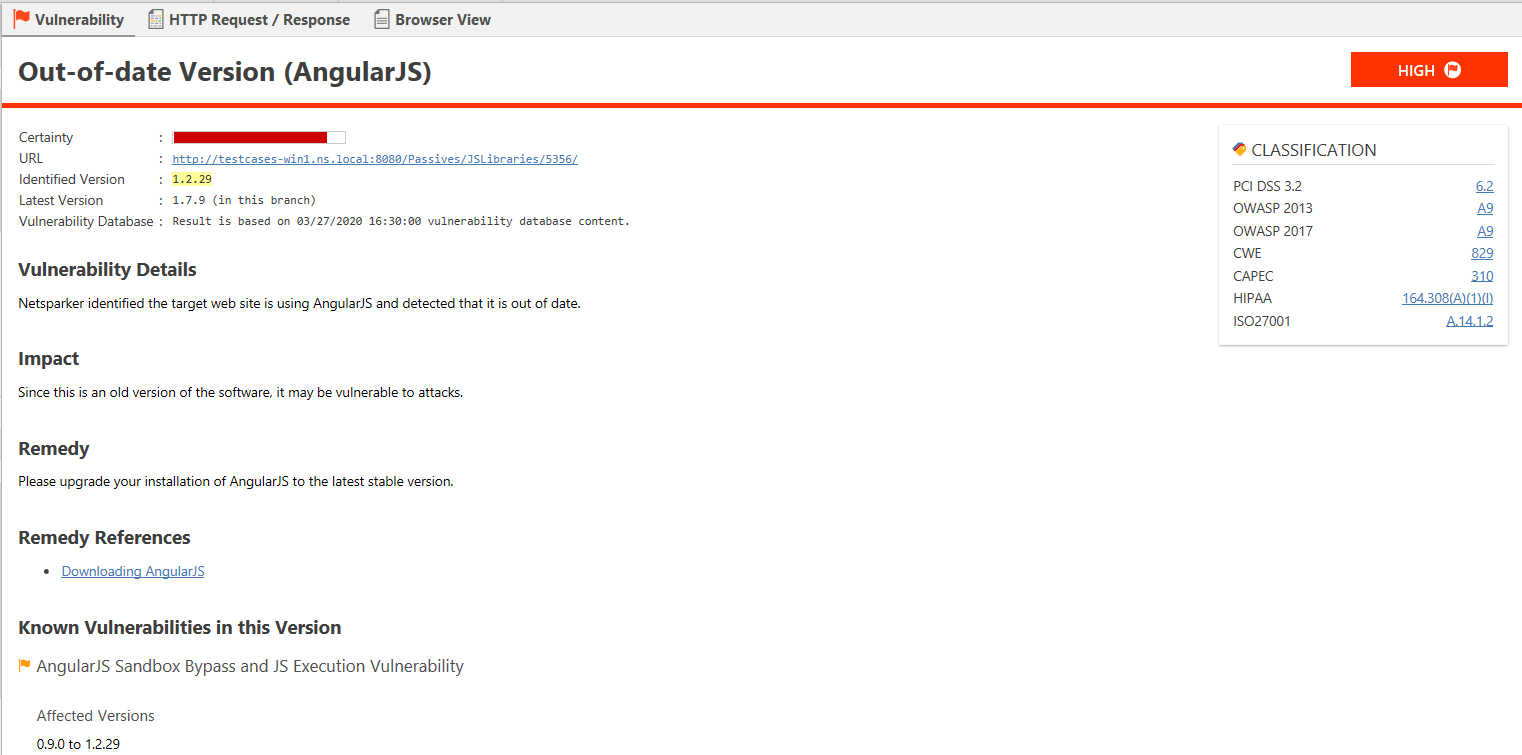
Which JavaScript Libraries Do Invicti Scanners Detect?
The scanning engine can fingerprint 20 of the most popular libraries, such as jQuery, React, Angular.js and Bootstrap.js..
How to View a Complete List of JavaScript Libraries in Invicti Enterprise
- From the main menu, click Policies, then New Scan Policy.
- Select the Security Checks tab.
- Scroll down the A-Z list and select JavaScript Libraries. The right hand pane displays a list of JavaScript Libraries.
How to View a Complete List of the JavaScript Libraries in Invicti Standard
- From the Home tab, click Scan Policy Editor.
- In the Security Check Groups pane, select JavaScript Libraries. The complete list of JavaScript Libraries is displayed in the Security Checks pane.
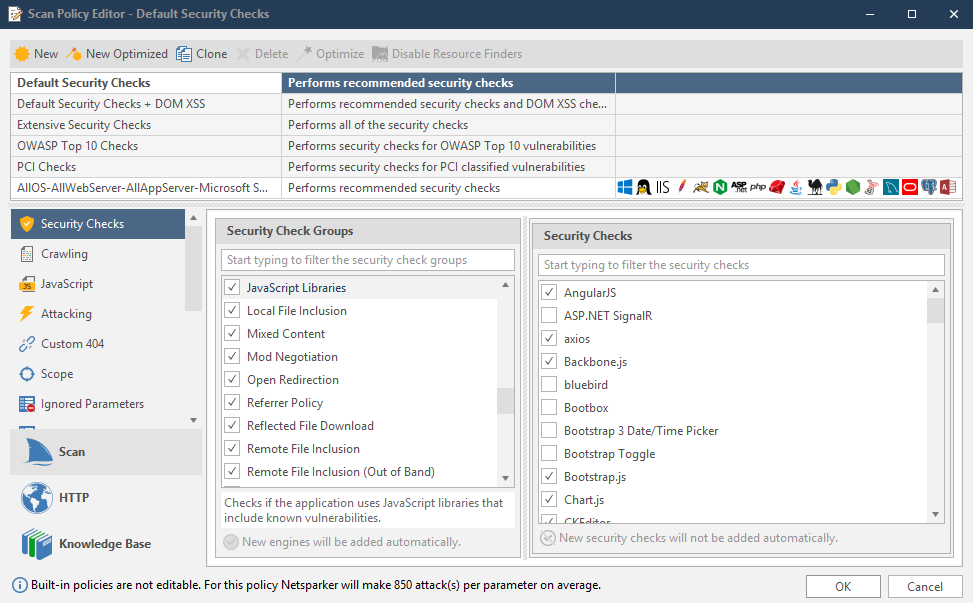
- In order to activate or deactivate fingerprinting JavaScript libraries, check or uncheck the JavaScript Libraries Security Check Group.
- Also, for New Scan Policies only (not Default ones), you can disable the JavaScript fingerprinting module, by unchecking JavaScript Libraries.
Fingerprinting Off-the-Shelf Web Applications
Custom built applications are very popular, especially in business-specific web applications, but off-the-shelf web applications, especially open source, are gaining in popularity. Please be aware that, like any custom application, open source applications can contain web vulnerabilities (see our Web Application Vulnerabilities Index).
Why Should You Keep Your Off-the-Shelf Web Applications Up to Date?
Malicious hackers are constantly and randomly scanning websites to check if they are vulnerable to a SQL Injection in an old version of WordPress or a Cross-site Scripting (XSS) vulnerability in an old version of Joomla! or phpBB.
If you are running an old version of software with a known vulnerability, it is only a matter of time until you get hacked.
Invicti Fingerprints Off-the-Shelf Web Applications
Since it is almost impossible to keep track of all the off-the-shelf web applications and components used in your web environment, we have several checks to help you automate this. Invicti will automatically fingerprint and identify any possible vulnerable JavaScript libraries and will also identify the versions of the most popular off-the-shelf web applications such as WordPress, Drupal, Joomla!, MediaWiki, phpBB, TWiki, and several others.