Invicti for Security Engineers
Secure your web applications with the only AppSec platform that truly scales
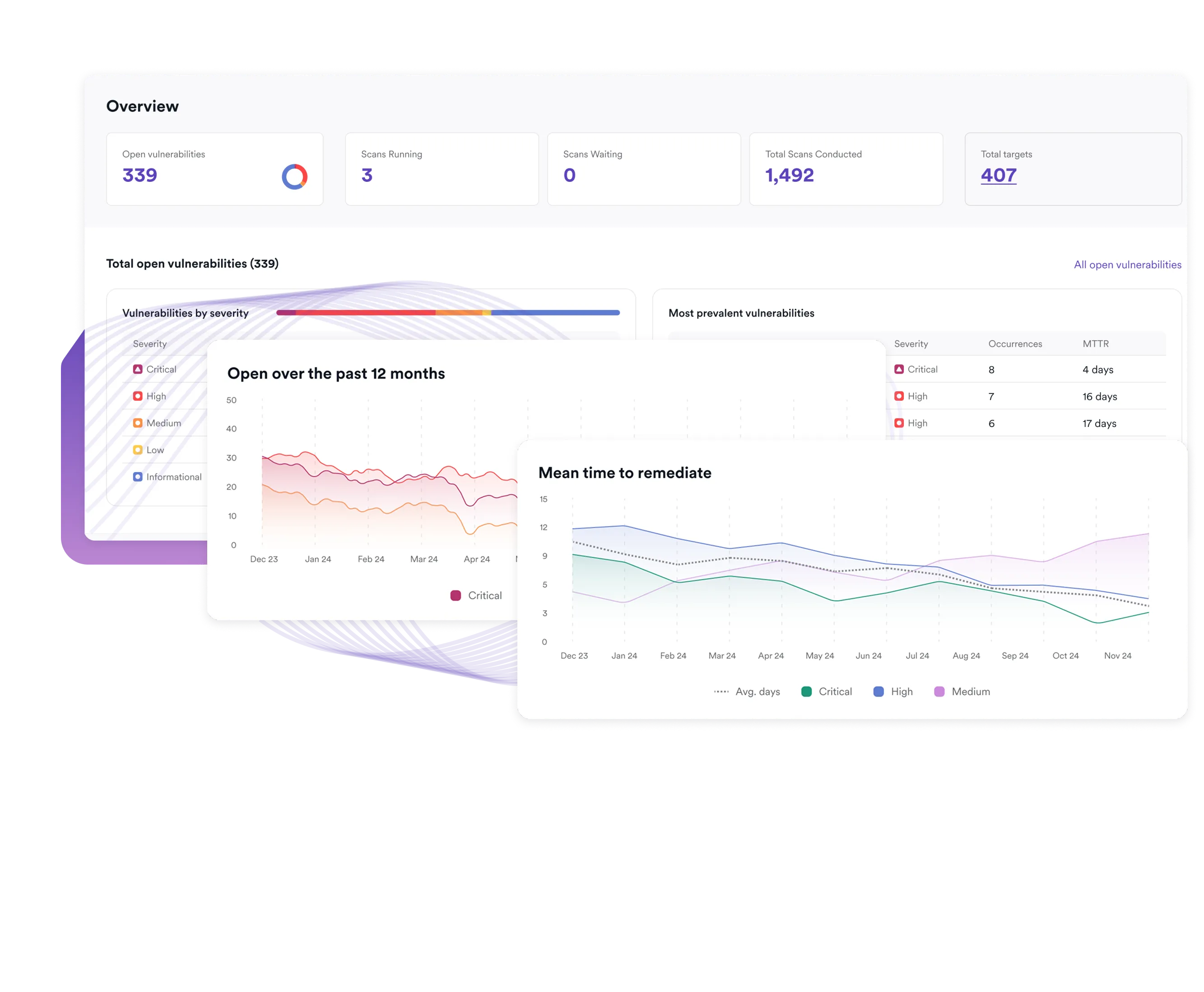

3600+ Top Organizations Trust Invicti






More Time for Hacking
Why spend hours finding and confirming ordinary bugs? Invicti not only scans everything for you but it also generates proof of exploit for every vulnerability that it finds, so you don’t have to. With the mundane out of the way, you can spend your time digging deep into more interesting subjects, for example researching new attack vectors.

No More Ghost Hunting
One of the most annoying tasks for a security engineer is trying to confirm an inexistent bug that is reported by an automated scanner. It takes a lot of time and causes a lot of frustration because it is much harder to prove that there is no bug than to find one. Invicti’s engine reports only vulnerabilities that it can prove, so you don’t need to worry about false positives.

Working with Other Tools
Invicti’s extensive import, export, and integration capabilities let you use it with many other solutions of your choice. For example, you can work together with your favorite manual tools to be able to follow up on results acquired from your own research or to dig deeper into issues that Invicti finds. If you prefer, you can also automate and integrate it to work completely in the background.
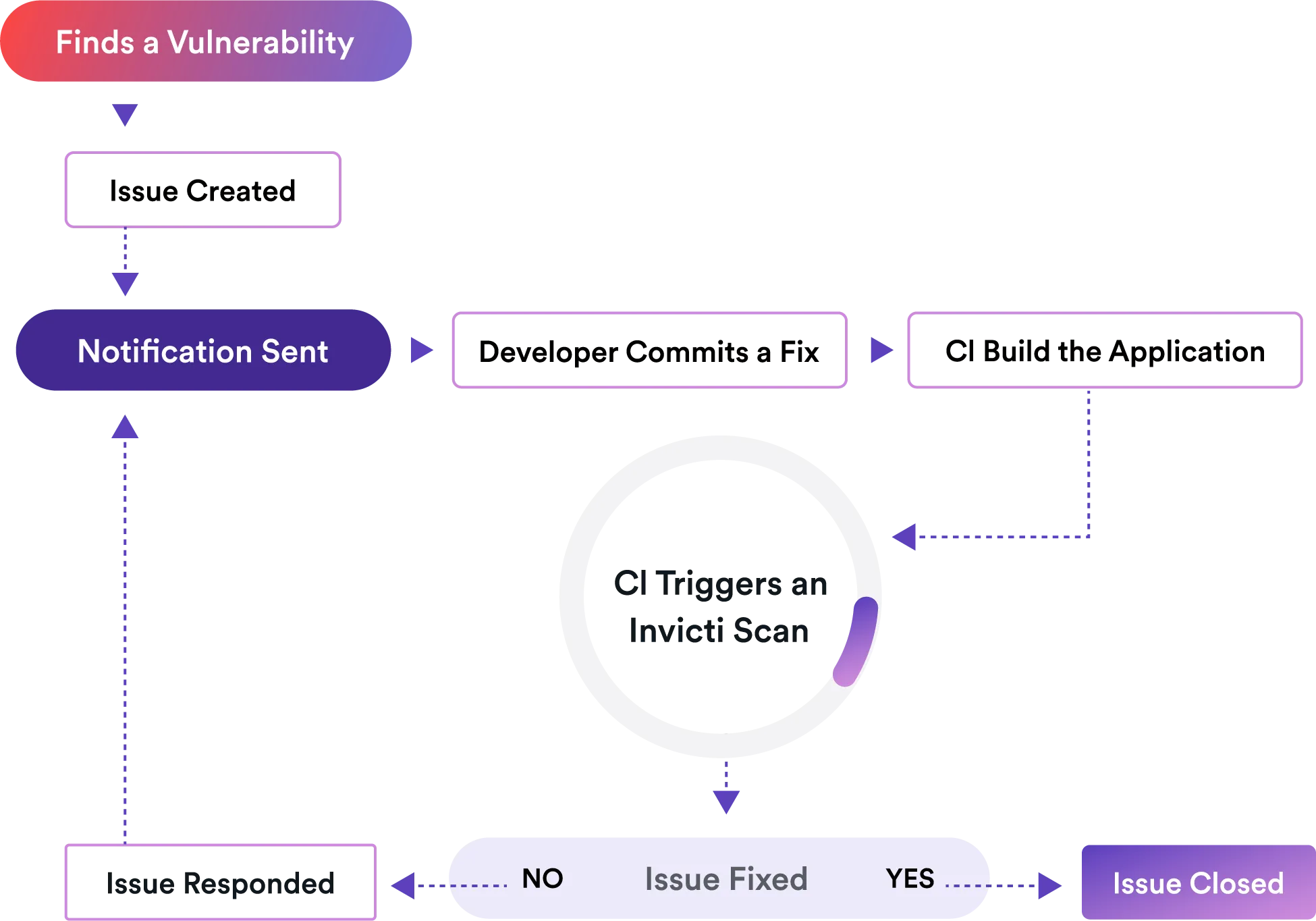
The AppSec platform that truly scales






