
Automate and scale AppSec with the world’s best web vulnerability scanner
Take control of your web security posture and build more secure applications faster with Invicti’s application security testing and vulnerability management solution—focused on automation, integration, and scalability.

The software is an important part of my security strategy which is in progress toward other services at OECD. And I find it better than external expertise. I had, of course, the opportunity to compare expertise reports with Invicti ones. Invicti was better, finding more breaches.
Senior Analyst, OECD
Cover your real-life app and API attack surface with the leading web vulnerability scanning tool
As you’re building and running complex web application environments on a rapid schedule, Invicti’s comprehensive DAST-based approach to AppSec helps you find and fix security vulnerabilities faster, more accurately, and across more technologies than with basic web application vulnerability scanners:
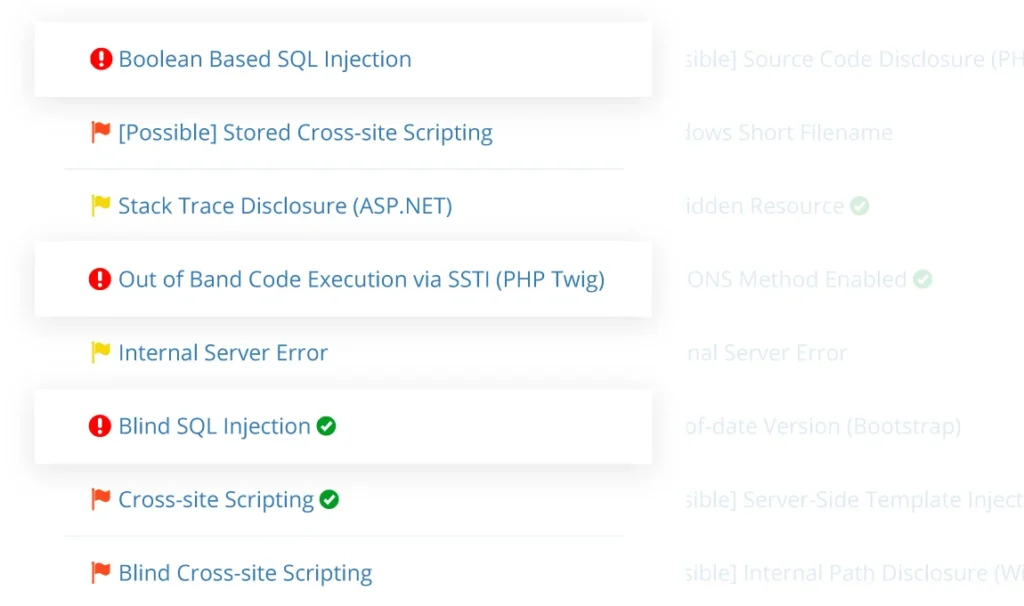
- New vulnerability detection to find security weaknesses, like SQL injection, cross-site scripting (XSS), or command injection, and misconfigurations such as missing web server security headers
- Full embedded browser engine to fully crawl and test every web page, including JavaScript-heavy single-page applications
- API security testing with automated authentication support and API endpoint discovery functionality
- Outdated tech stack detection and dynamic SCA based on fingerprinting against CVEs in an internal vulnerability database
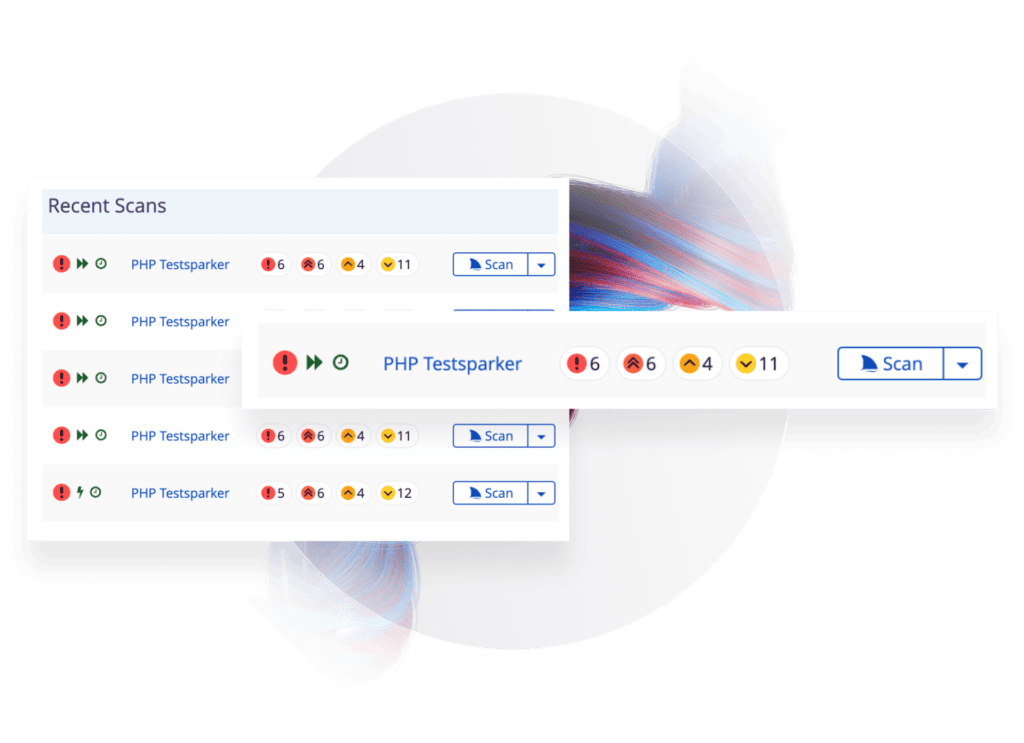

Integrate a zero-noise web application vulnerability scanner into your SDLC
Web application security testing tools can only be effective in fast-moving DevOps workflows when they are tightly integrated into the entire SDLC, from first builds through production. The Invicti platform provides a vulnerability scanning solution that integrates deeply into development and operations to find more security vulnerabilities as early as possible:
- 50+ out-of-the-box integrations with industry-standard issue trackers such as Jira, CI/CD tools such as Jenkins, and collaboration platforms—plus a comprehensive internal API for custom integrations
- Trustworthy and comprehensive vulnerability reports with full technical information, proof of vulnerability, and remediation guidance delivered directly as actionable tickets
- Available in on-premises and cloud-based SaaS editions
Speed up vulnerability assessment and remediation with proof-based scanning
To sidestep the false positives that cause scalability problems for other web application scanners (especially open-source tools), Invicti uses proof-based scanning to safely and automatically exploit common types of high-severity and critical vulnerabilities, delivering a proof of exploitability to show the security issue is real:
- Routinely fix confirmed security vulnerabilities faster by sending tickets directly to your devs without manual verification by security professionals
- Use your DAST scanner for in-house automated penetration testing to maintain a strong security posture in between scheduled manual pentests
- Update your web application firewall rules in near real time based on reports of exploitable vulnerabilities
- Prioritize security scans already during the asset discovery phase with proprietary AI/ML Predictive Risk Scoring to minimize OWASP Top 10 security risks at each stage
Trusted by IT & Telecom Companies Like








“Invicti are not just another vendor from where we purchase any other software, they are like business partners.”
Jade Ohlhauser, CTO
RPM Software Uses Invicti to Ensure their Online Service Offering is Secure
As a cloud-based software developer and provider, RPM Software is responsible for the sensitive data their customers store on their solutions, hence they cannot afford to take web application security lightly…
Featured IT & Telecom Content
Web Security
Does having a PCI compliant website and business means they are bulletproof, or better, hacker proof? This first part of this PCI compliance article looks into…
PCI Vulnerability Scan
Run automated PCI DSS vulnerability scans with Invicti to automatically identify security vulnerabilities in your web applications, and fix them to…
Web Security
As we have seen in part 1 of PCI Complaince, the Good, the Bad and the Insecure, PCI compliance is a good idea in abstract, however it should be…
Web Security
When it comes to compliance, especially as it relates to web application security, the Payment Card Industry Data Security Standard (PCI DSS) is usually the main…
IT Security Software Tools
Businesses are focusing on web security to ensure the web & cloud based services they use are secure. Web application security is not easy…
Server Security Software
An accurate and automated web server security software is vital to the security of your web applications, because the web server itself also needs to be secured…
