Subresource Integrity (SRI) for Validating Web Resources Hosted on Third Party Services (CDNs)
This article explains what is Subresource Integrity (SRI), how it works and how it helps web application developers ensure a more secure web environment especially when hosting resources on third party servers and services such as Content Delivery Networks (CDNs).
Your Information will be kept private.
Your Information will be kept private.
 On the 23rd of June 2016 the World Wide Web Consortium (W3C) announced the Subresource Integrity (SRI) as a W3C recommendation.
On the 23rd of June 2016 the World Wide Web Consortium (W3C) announced the Subresource Integrity (SRI) as a W3C recommendation.
On the same day we also announced some new web security checks for the Subresource Integrity in our automated web application security scanner.
What is Subresource Integrity?
Subresource Integrity (SRI) is a method that allows web application developers to ensure that resources hosted on third party services such as Content Delivery Networks (CDN) has been delivered without any unexpected modifications.
The W3C recommended the Subresource Integrity (SRI) as a best-practise whenever resources are loaded from a third-party source.
How Does the Subresource Integrity (SRI) Work?
SRI does this by using hash comparisons; it compares the hash value of the resources hosted on the web server and those hosted on the third party server or service.
Why Use the Subresource Integrity (SRI) ?
To improve the performance of their websites many organizations hosts different resources on different servers. For example resources such as scripts, CSS stylesheets and images are typically hosted on a content delivery network (CDN).
However by doing so you put explicit trust in your CDN or third party service. This means that should the CDN service get hacked, or the DNS is hijacked then your web application is hacked as well. At this stage the attacker can modify the content of a script file that is hosted on your CDN which will lead to a cross-site scripting vulnerability on your website.
Therefore by implementing SRI you ensure that the web application is referring to a file that is actually legitimate, and should the file change your browser will not load it and the attack will fail.
You can check if your browser supports the Subresource Integrity from the Can I Use website.
Why Isn’t HTTPS Enough?
HTTPS is used to ensure that the connection between the user’s browser and the web server is encrypted. Therefore in case the content on the third party server or service is tampered with malicious code, it will still be delivered to the user, irrelevant if the connection is encrypted or not.
Netsparker Subresource Integrity (SRI) Security Checks
When you scan your websites with the Netsparker web vulnerability scanner it will check if SubResource Integrity (SRI) is implemented.
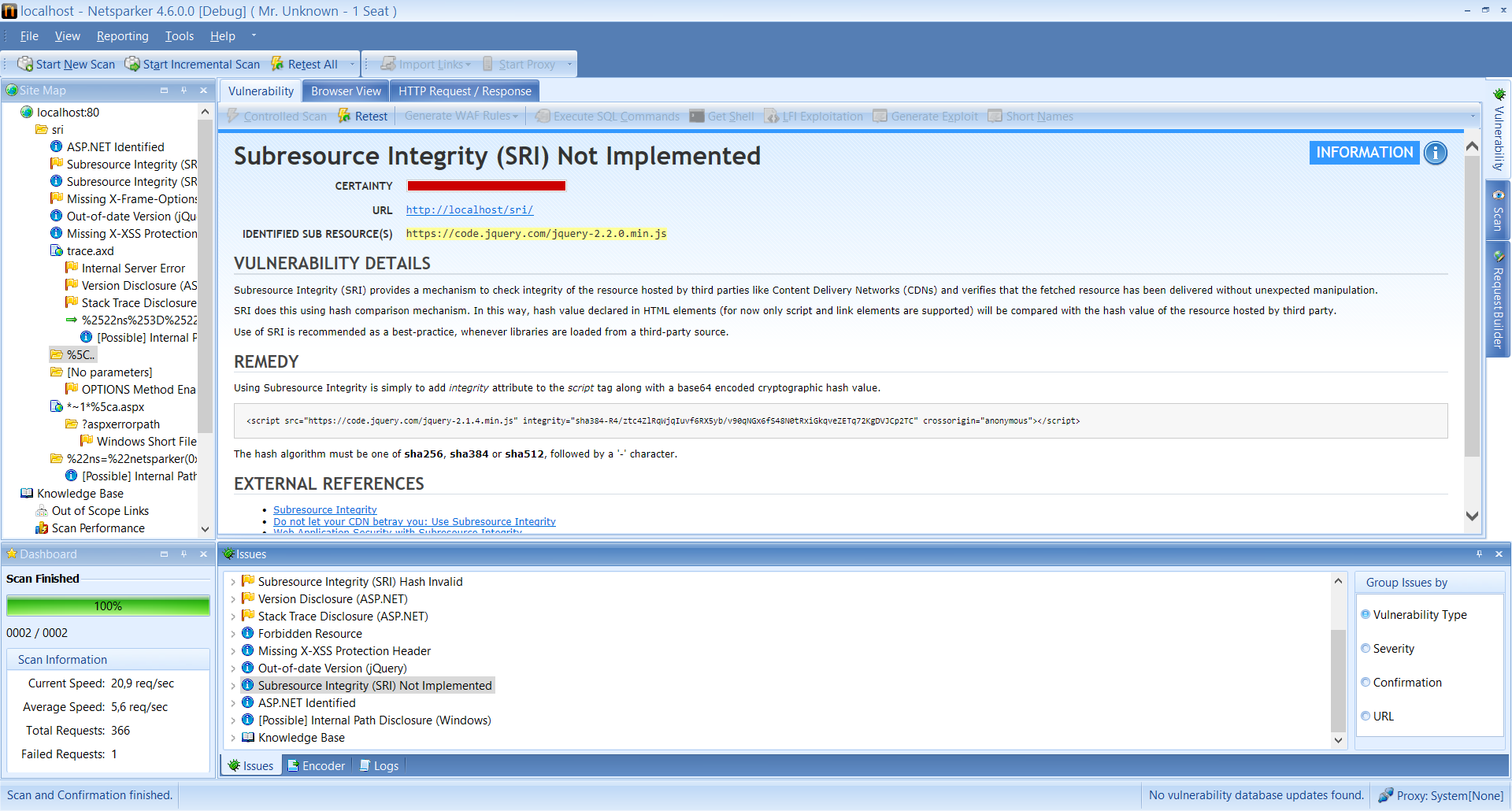
And if SRI is implemented, the security scanner will also check for invalid hashes. Therefore should Netsparker report a mismatch in the hashes, as in the below screenshot, it means that an external resource has been compromised.
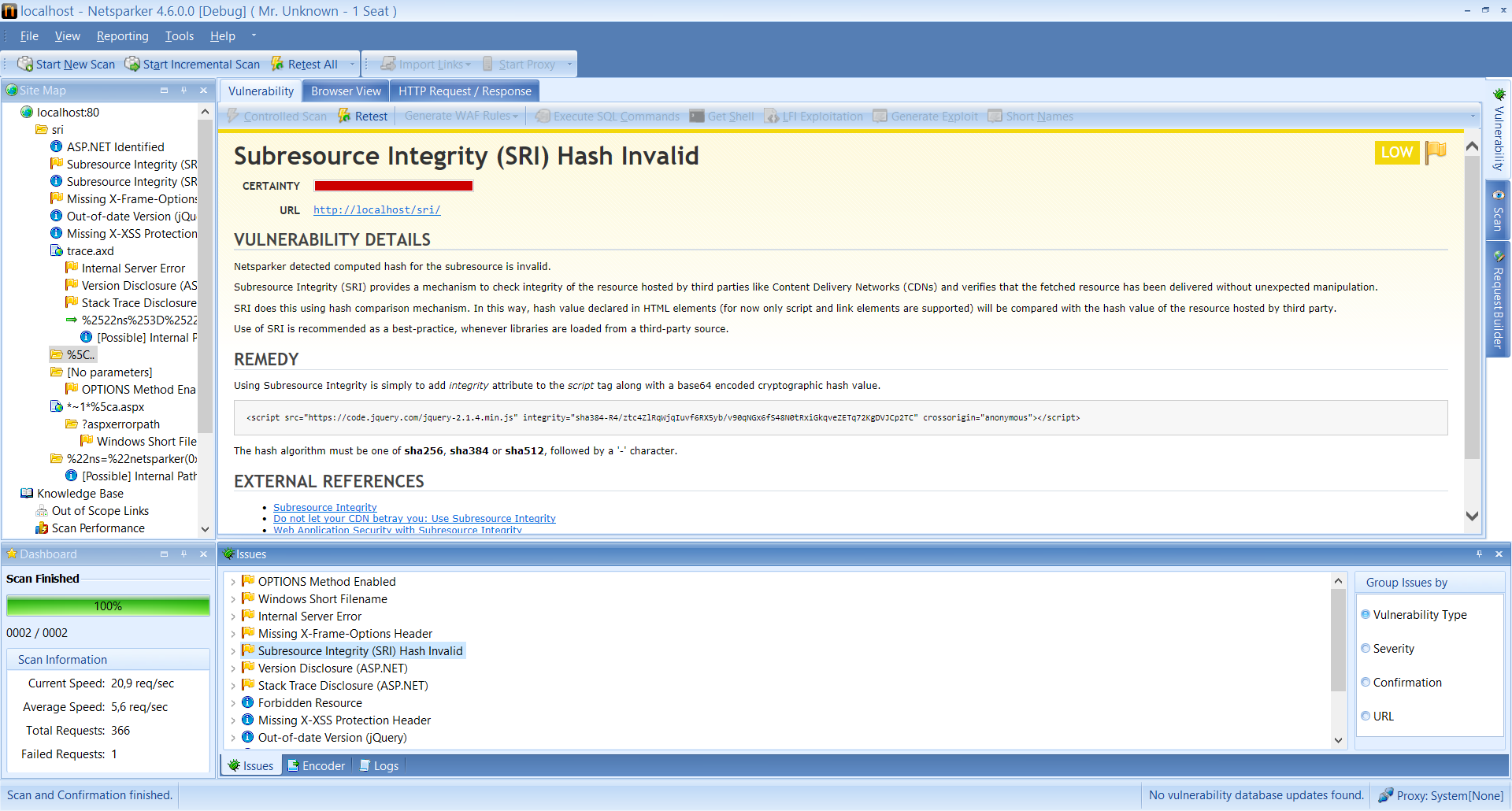
Example: implementing Subresource Integrity (SRI)
The format of the integrity HTML attribute is:
integrity="[hash algorithm]-[base64 encoded cryptographic hash value]
The hash algorithms that can be used are; sha256, sha384 or sha512. Therefore to enable the Subresource integrity checks simply add the integrity HTML attribute to the script tag as shown in the below example:
<script src="https://code.jquery.com/jquery-2.1.4.min.js" integrity="sha384-R4/ztc4ZlRqWjqIuvf6RX5yb/v90qNGx6fS48N0tRxiGkqveZETq72KgDVJCp2TC" crossorigin="anonymous"></script>
For more detailed information on SRI refer to the W3C SRI documentation.






