How you can disable directory listing on your web server—and why you should
This article explains what directory listing is, why it can be dangerous, and how to disable it on a variety of web servers, including Apache, Nginx, and Microsoft Internet Information Services (IIS).

Misconfigured or default configuration on web servers may lead to a number of issues that could aid malicious hackers in their attacks. One common web server issue is directory listing. Many leave it enabled by mistake, thus creating an information disclosure issue (leakage of sensitive information) because they are allowing everyone to see a list of files in a directory or even all the files and directories on a website.
This article explains what directory listing is and how to:
- Disable directory listing on Tomcat server
- Disable directory listing on Nginx web server
- Disable directory listing on LiteSpeed server
- Disable directory listing on Lighttpd server
- Disable directory listing on Microsoft IIS server
- Disable directory listing on Apache server
What is directory listing?
Directory listing is a web server feature that, when enabled, lists the content of a directory that has no index file (e.g. index.php or index.html). Therefore, if a request is made to a directory on which directory listing is enabled and there is no index file such as index.php or index.asp, the web server will return a directory listing, even if that directory contains files from a web application. This creates an information leakage issue and attackers can use such information to craft other attacks, including exploiting vulnerabilities such as cross-site scripting (XSS).
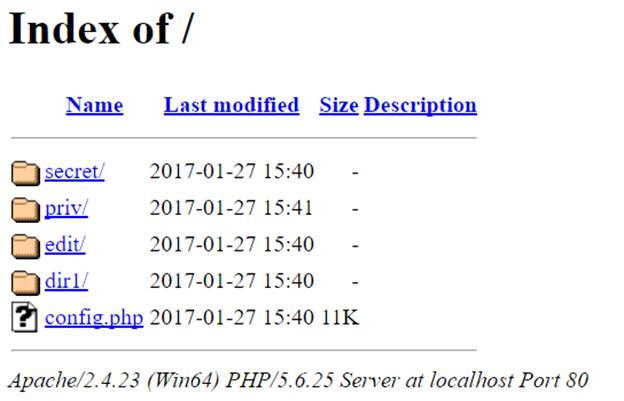
As you can see from the picture above, the directory listing feature generates an output similar to the dir or ls command that is run on an operating system. Directory listing issues are the type of issues that an SSL certificate won’t protect you from. The good news is that they can be easily identified with an automated web vulnerability scanner.
What information is leaked via directory listing and what is the risk?
Let’s assume you have a backup copy of the file config.php, containing the credentials for a database connection. You keep the copy in the secret folder, for which directory listing hasn‘t been disabled.
If an attacker finds the secret folder by crawling or fuzzing, they only need to access it directly by navigating to http://www.example.com/secret/ to see and download the file with your database connection details. Now the attacker has the connection details to your web application’s database and can exfiltrate data, craft other attacks, and potentially even damage the database or application.
How to disable directory listing
As a security best practice, it is recommended to disable directory browsing and listing. A quick-and-dirty way to disable directory listing is to create an empty index file (index.php, index.html, or any other extension your web server is configured to parse) in the relevant directory. In most cases, though, this is not the best solution because such files can be overlooked later, like when migrating a website or application from development to production or when new directories are added.
It’s therefore worth implementing a permanent and secure solution by disabling directory listing at web server level, as explained below.
Disabling directory listing for selected web servers
Disabling directory listing on Tomcat
Starting from Tomcat 5.0, directory listing is disabled by default. However, it is still possible to disable directory listing if it was enabled because of a regression or configuration changes. You can configure directory listing on two different levels: either for all your web projects or only for a specific website.
Disabling directory listing for all Tomcat web projects
To disable directory listing on the Tomcat web server, open the conf/web.xml file in the directory where Tomcat is installed. In our test on Windows 10, the default installation directory was C:\Program Files (x86)\Apache Software Foundation\Tomcat 9.0
<servlet> <servlet-name>default</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup></servlet>
Find the listing part of the <param-name> value in the <init-param> tag and check the <param-value> content. If this field is true and you want to disable directory listing, change this field to false. You can directly copy and modify the code above if needed.
Disabling directory listing for a specific Tomcat web project
The above method configured a general setting that applies to all the web projects running on the server, but you can also disable directory listing only for a specific website. Open the web.xml file for the relevant web project and add the following code:
<servlet> <servlet-name>DefaultServletOverride</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup></servlet><servlet-mapping> <servlet-name>DefaultServletOverride</servlet-name> <url-pattern>/</url-pattern></servlet-mapping><servlet> <servlet-name>DefaultServletOverride</servlet-name> <servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class> <init-param> <param-name>debug</param-name> <param-value>0</param-value> </init-param> <init-param> <param-name>listings</param-name> <param-value>false</param-value> </init-param> <load-on-startup>1</load-on-startup></servlet><servlet-mapping> <servlet-name>DefaultServletOverride</servlet-name> <url-pattern>/</url-pattern></servlet-mapping>
The default servlet setting was overridden with the above change, so the website where you made this change will run independently of the global setting configured using the first method.
Disabling directory listing on Nginx
The directory listing feature on Nginx is controlled by the module ngx_http_index_module. Directory listing is disabled by default in the Nginx configuration file, but you can still disable it manually if it was enabled because of a regression or configuration changes. The Nginx parameter autoindex is used together with the location segment to enable or disable the directory listing feature.
The default configuration file of a Nginx server is called nginx.conf and can be found under /usr/local/nginx/conf, /etc/nginx, or /usr/local/etc/nginx. If the default value has been changed, you will see a setting similar to the following:
server { listen 80; server_name domain.com www.domain.com; access_log /var/...........................; root /path/to/root; location / { index index.php index.html index.htm; } location /somedir { autoindex on; }}
In this section, the crucial parameter is autoindex on;. In the above example, directory listing is configured only for the somedir directory. If no directory is specified (i.e. you have location / {autoindex on;}), the rule will be applied to all folders. To disable directory listing, we need to change the value to autoindex off. Don’t forget to restart the server to allow changes to take effect:
service nginx restart
Disabling directory listing on LiteSpeed
As with the earlier web servers, the LiteSpeed web server also lets you disable directory listing at both web server and website level. To disable directory listing at the server level, you can manually update the httpd_config.xml file as shown below, but you can also do the same using LiteSpeed server control panel:
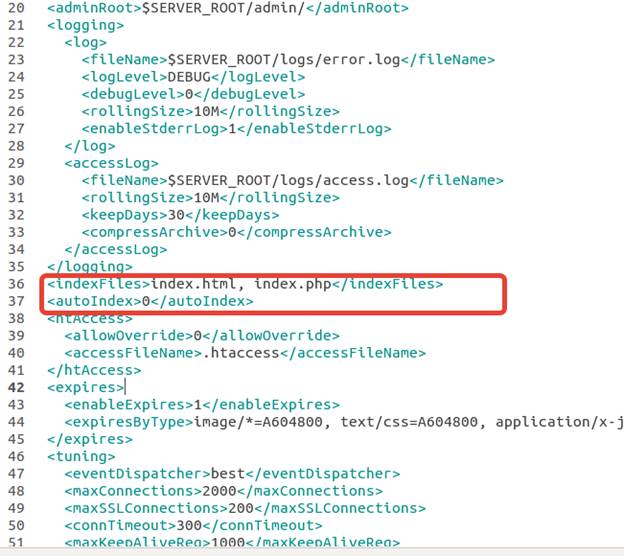
As you can see from the code example in the screenshot above, if you want to disable directory listing at the server level, add the following line to the httpd_config.xml file:
<autoIndex>0</autoIndex>
To enable or disable the directory listing at website level, you need to follow the /VIRTUAL_HOST_ADI/conf/vhconf.xml path and make a similar change in the vhconf.xml file at that location.
Disabling directory listing on Lighttpd
Directory listing is disabled by default on a Lighttpd web server, but you can disable it manually in the dirlisting.conf if it was enabled because of a regression or configuration changes. The configuration file for the mod_dirlisting module that generates directory listings is /etc/lighttpd/conf.d/dirlisting.conf and looks like this:
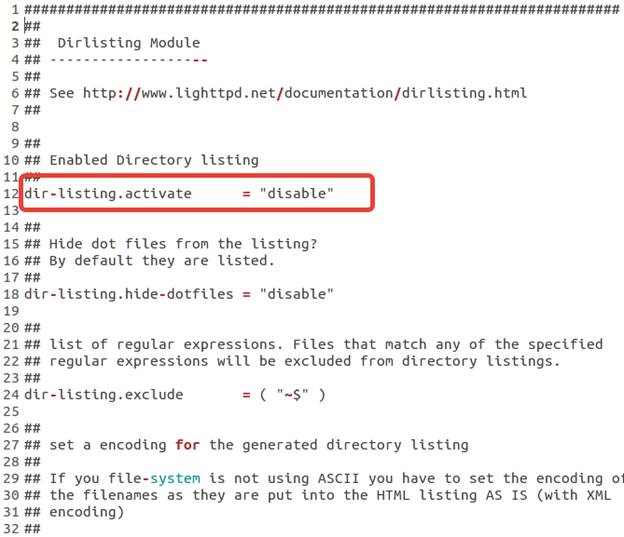
To disable directory listing on the server, ensure you have the following line in the config file:
dir-listing.activate = "disable"
If you want to enable directory listing only for a particular directory, you need to make the following changes in the configuration file specifically for that directory (using /download as an example):
$HTTP["url"] =~ "^/download($|/)" { dir-listing.activate = "enable"}
Disabling directory listing on IIS
Directory listing on the IIS web server is disabled by default, but you can disable it manually from the configuration interface of IIS web server if it was enabled because of a regression or configuration changes.
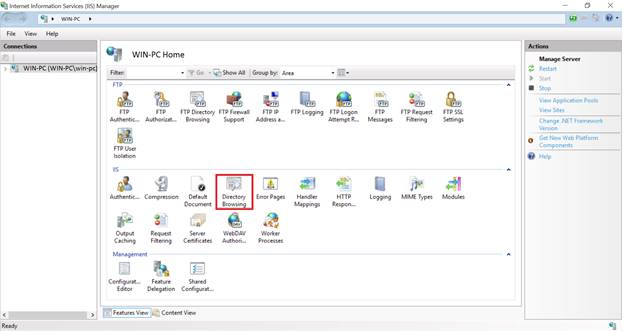
For IIS7 and above, you can disable directory listing from the Directory Browsing settings in the IIS manager console:
Alternatively, you can run the following command in the command line:
appcmd set config /section:directoryBrowse /enabled:false
Disabling directory listing on Apache
In order to disable directory listing on an Apache web server, you have to create a .htaccess file in the related application directory. You can add the following lines to the Apache configuration file httpd.conf or replace the existing lines with the following:
<Directory /{YOUR DIRECTORY}> Options FollowSymLinks</Directory>
As you can see from the example code above, you should also remove the Indexes (for directory indexing) and MultiViews statements for the directory listing feature to be disabled safely on an Apache web server.
Vulnerability Classification and Severity Table
ClassificationID / SeverityOWASP 2013A5CWE548CAPEC127WASC16OWASP-PCC6CVSS:3.0
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N/E:H/RL:O/RC:C
InvictiInformation


