Netsparker Standard 5.5 – November 2019 Update
This blog post announces the November 2019 update for Netsparker Standard 5.5. The release highlights are a new Scan Search feature, new Security Checks, and new Web Application Firewall integrations. Other features include improvements to the Progress Panel and Form Authentication OTP support.
Your Information will be kept private.
Your Information will be kept private.

We’re delighted to announce the release of Netsparker Standard 5.5. The highlights of this release are:
- Scan Search
- New Security Checks
- New Web Application Firewall software integrations
Other new features include Progress Panel improvements and Form Authentication OTP support.
Scan Search Feature
We’ve added a scan search feature that allows searching for anything in the scan. Users will be able to conduct a full-text search on a scan among all the requests, responses and vulnerabilities.
The Search dialog can be opened using the CTRL+K keyboard shortcut. Then, you can enter any search phrase, which searches through every link's request and response in the scan.
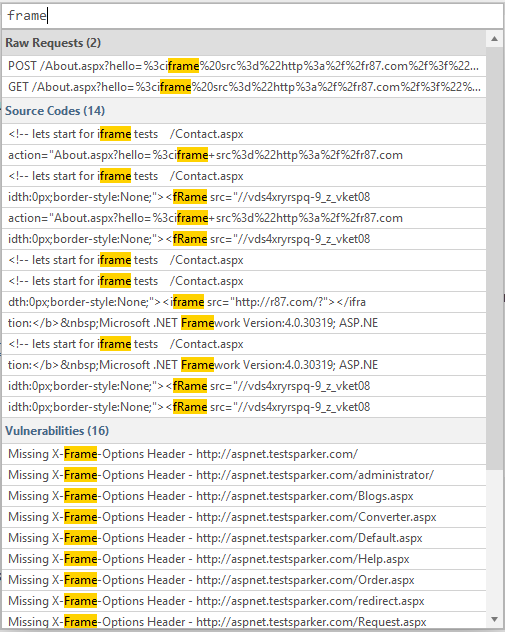
For further information, see Scan Search.
New Security Checks
We have added a new security check and BREACH Attack Detection.
BREACH Attack Detection
Even if you use an SSL/TLS protected connection, an attacker can still view the victim’s encrypted traffic and cause them to inadvertently send HTTP requests to the vulnerable web server (using invisible frames).
A BREACH attack is possible when web applications meet the following conditions:
- SSL/TLS-secured connection
- HTTP level compression (using gzip or Deflate)
- Reflected user-controlled input in the page
- Sensitive data that is attractive to attackers
This combination of factors can enable an attacker to 'eavesdrop' on the connection. By measuring the packet length, they can infer some sensitive information.

For further information, see BREACH Attack.
New WAF Integrations
Web Application Firewalls (WAF) filter, monitor, and block HTTP traffic, helping protect web applications from attacks and breaches. Netsparker aims to integrate with existing WAFs to provide better protection against these risks.
WAF integration has been improved to create WAF rules via REST APIs. This means that when a vulnerability is found, Netsparker can create a WAF rule at the same time to block vulnerable requests. We have added three new WAFs in this latest update.
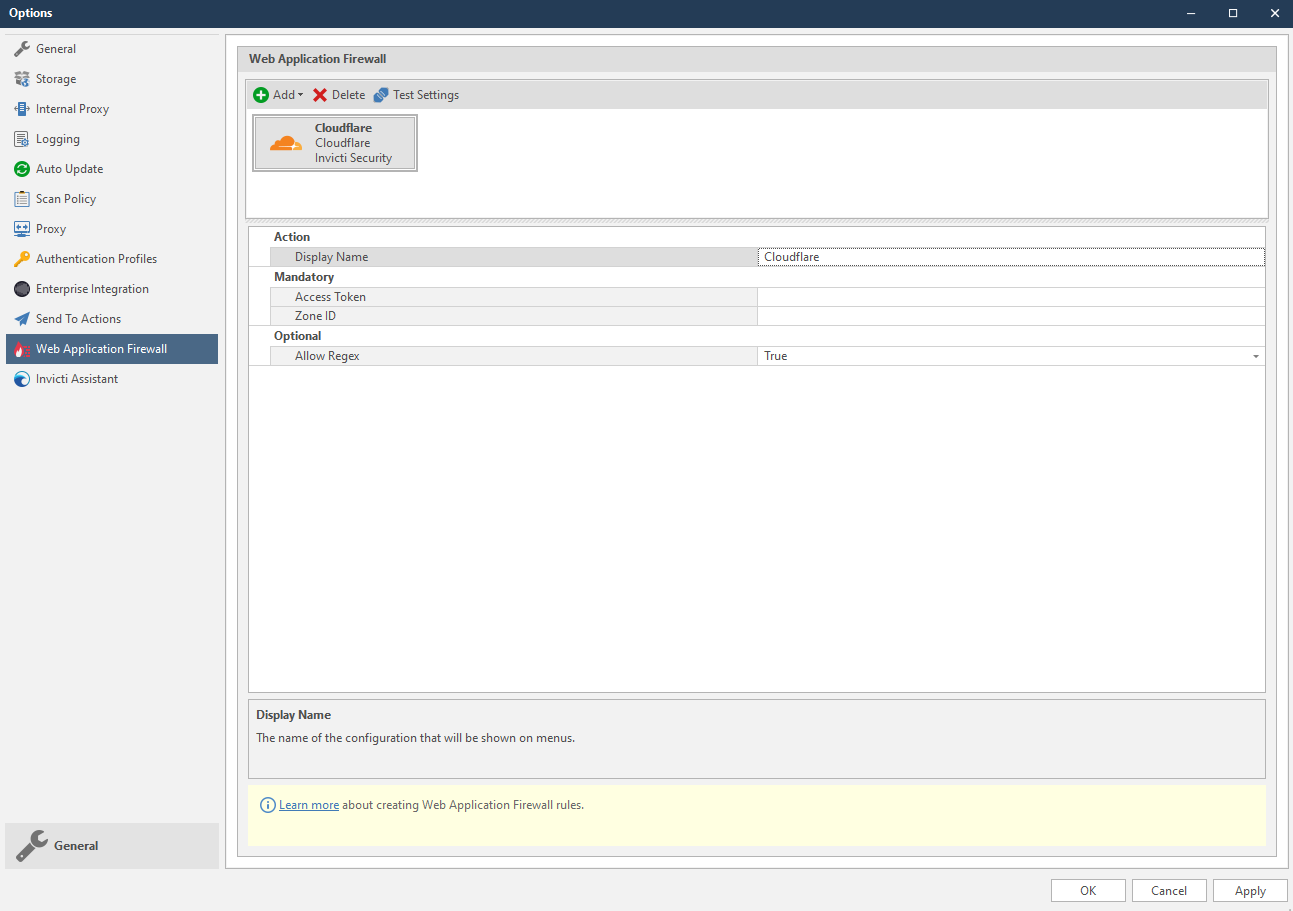
You are now able to generate WAF rules for Amazon Web Services, Cloudflare and Imperva SecureSphere WAF software. Fixing vulnerabilities using WAF software is a temporary solution. It will not solve the root cause of the issue, but it will enable you to prevent external attacks until you fix the root cause.
Progress Panel Improvements
We have made some improvements to the Progress panel, in order to better estimate the remaining scan time.
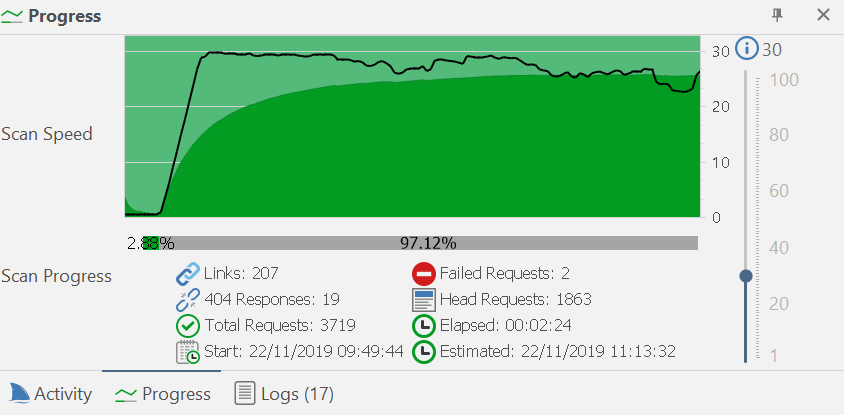
- The Progress bar estimation calculation is no longer based on the number of remaining HTTP requests to be made, but on engine runtimes, the actual time these requests and analysis of their responses would take, including CPU-intensive DOM simulation operations.
- The Scan Performance section in the Knowledge Base report has also been updated to reflect engine runtimes instead of request count.
- The Progress Panel’s Requests per second setting has been improved, so that its value can be changed by clicking anywhere along the slider.
For further information, see Progress.
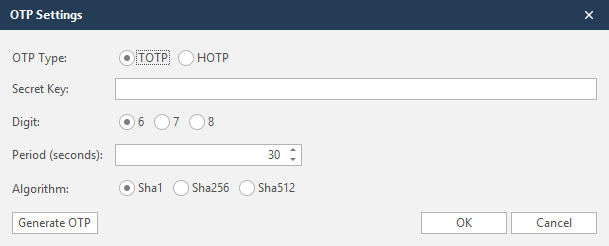
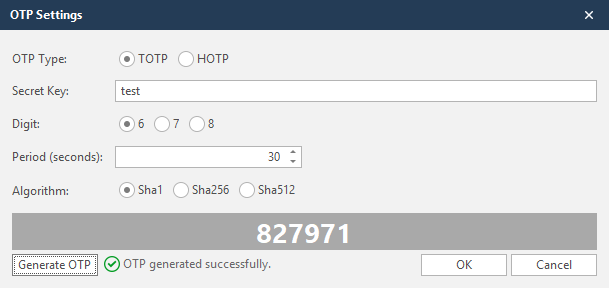
Form Authentication OTP Support
If the target website has a One-Time-Password requirement (two-factor authentication), you will be able to configure Netsparker to auto-fill the required password. Both time-based OTP and HMAC-based OTP are supported.
You can access this from the Form tab in the Start a New Website or Web Service Scan dialog.
Further Information
For a complete list of what is new, improved and fixed in this update, refer to the Netsparker Standard changelog.






