Streamline authenticated scanning with Invicti’s verifier agents
Authenticated scanning remains challenging for some automated vulnerability scanners. Doing it across multiple environments, deployments, and locations is even more difficult. To streamline the process of scanning password-protected web pages, Invicti has added the ability to deploy local authentication verifier agents.
The importance and challenges of authenticated scanning
Less advanced dynamic application security testing (DAST) tools will often skip password-protected web pages during scanning due to problems with automated authentication. With more and more application functionality only being accessible to authorized users, authenticated scanning is crucial for test coverage, even as authentication technologies get more complex. Protected assets are also likely to be the most attractive targets for attackers and the gatekeepers of valuable data, so leaving them untested puts organizations at serious risk.
Getting authenticated scanning right is tricky enough, but running it consistently across the variety of environments used in application development is even more difficult. Some of them might be internal and not directly accessible from the Internet or even reside in a separate physical network or geographical location. And yet they all require authenticated scanning to ensure security by identifying vulnerabilities and other issues, such as outdated software versions and misconfigurations.
Authentication verifier agents in Invicti
To help secure all parts of your web applications, Invicti has introduced the authentication verifier agent feature to streamline authenticated scanning when internal scanning agents are used. This approach makes it possible to scan a wide variety of application environments with full authentication support. Combined with flexible deployment options for scanning agents, this helps you align security testing with the development structure while taking advantage of Invicti’s centralized scan and vulnerability management.
Before getting into the details of using an authentication verifier agent in your local environment, a word about the operational basics. You can install authentication verifier agents for cloud-based Invicti deployments, with authentication verifier agents available for Windows and Linux (currently Red Hat and Debian).
Setting up an authentication verifier
Deploying an authentication verifier agent is straightforward. After downloading the required file for your environment, you need to unzip it and configure the appsetting.json file. For the authentication verifier agent to work, you need to provide your Invicti API token and then enter a unique agent name so you can select this particular agent when verifying a login form. You can also configure the agent as an operating system service for Windows and Linux so it can run in the background and receive commands. For more information, see Setting the Agent as a Windows Service or Setting the Agent as a Linux Service.
After installing an internal authentication verifier, you can run an authenticated scan in your environment. When launching a new scan, select the Form Authentication checkbox in the New Scan window and enter the login form URL and credentials. To verify login and logout, Invicti will use the authentication verifier agent in your environment to make sure it can authenticate. Once Invicti completes the login and logout process successfully, you can close the simulation window.
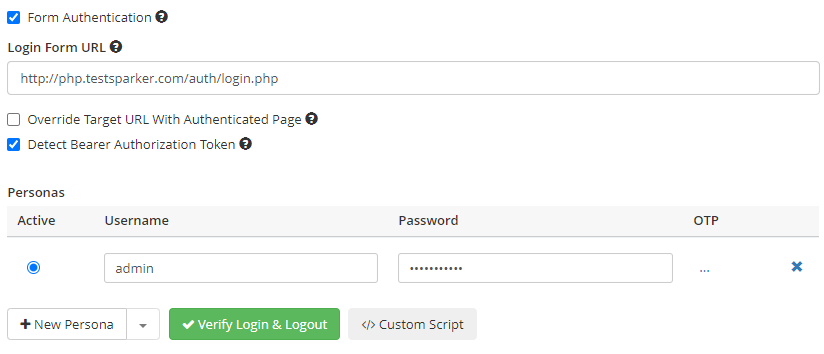
Note that the authentication verifier agent is an optional component. You can download and install the authentication verifier agent if you need to scan websites with form-based, basic, or OAuth2 authentication. When Invicti authenticates itself against the web application, you can use the same verifier agent for other login forms in your environment.
Using multiple verifier agents
Sometimes, you may want to run concurrent scans or use several different authentication verifier agents for convenience. To cover these cases, the authentication verifier agent supports multiple authentication processes. Similar to the scanning agent, you can install as many verifier agents as you need when you need to authenticate many login forms.
To install an additional authentication verifier agent, simply duplicate the existing agent file under a different filename and enter a unique agent name in the appsetting.json file. Using multiple verifier agents rather than only the central verifier can also be a way to speed up authentication and testing. If you’ve created multiple verifier agents, you can then select the one you want to use. When creating a new scan, select Form Authentication. Invicti will detect multiple verifier agents and prompt you to select one to use for authentication.
Working with scanning and verifier agents
As well as having multiple verifier agents in your environment, you can also have a mix of scanning and verifier agents to choose from for testing your web applications. You can download both types of agents from the Configure Agent window and deploy them in your environment following our instructions for installing internal agents. Once deployed, the agents will be accessible from the Invicti user interface. The ability to use both types of agents further increases Invicti’s deployment flexibility, allowing you to run authenticated scans that match your specific requirements while maintaining centralized scan and vulnerability management.
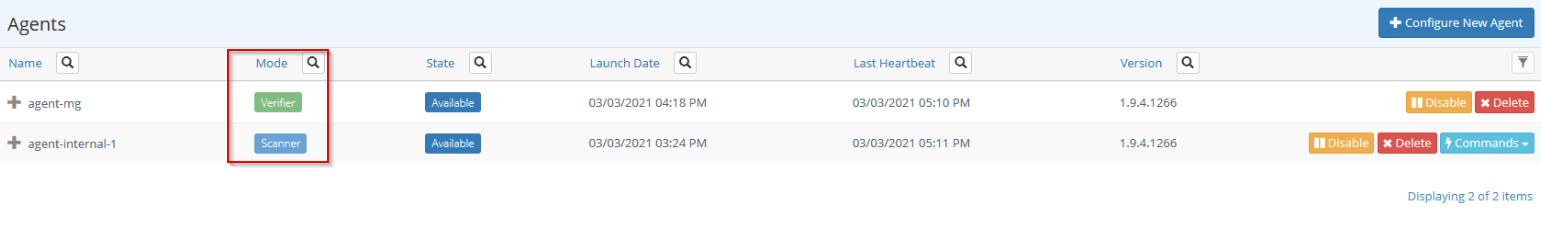
Authenticated scanning to suit your needs with verifier agents
Maximizing scan coverage and accuracy is crucial to ensure that your DAST solution provides real security benefits for web applications. If a scanner skips password-protected sections or pages, you simply don’t know your full application security status. As an industry leader, Invicti uses advanced crawling and authentication techniques to maximize vulnerability testing coverage across all types of modern websites and applications.
Authentication verifier agents make it easier to run authenticated scanning across multiple environments, deployments, and locations. Combined with the accuracy of Proof-Based Scanning, authenticated application security testing gives you a true picture of all the issues you need to remedy to protect your websites and applications from attackers.
For more information and FAQs related to authentication verifier agents in Invicti, see our support page for internal agents.


