How Invicti Reports Inform Vulnerability Management
Invicti provides reports that give users information on the nature, severity, frequency, and other attributes of detected vulnerabilities. This blog post explains the purpose and layout of the main reports and report types available in Invicti: detailed scan reports, executive summary reports, comparison reports, and compliance reports.
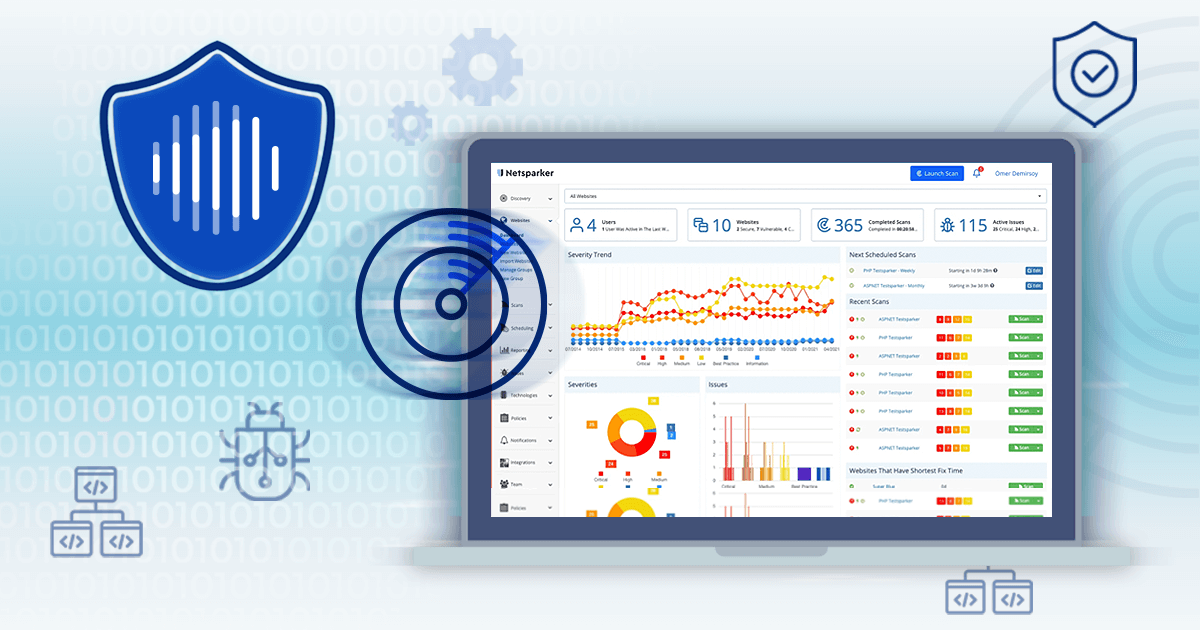
How Does Invicti Reporting Work?
Invicti works by scanning your target web applications to detect which vulnerabilities could be exploited and how. Following scans, you can view and download many types of reports. There are detailed reports that provide developers with essential information to enable them to prioritize, understand and fix issues; summary reports that are useful for managers and team leaders to monitor progress; comparison reports that help track progress over time; and compliance reports that give compliance officers information on where the gaps are. These reports are referred to as Report Templates.Security professionals work in a collaborative environment which brings challenges among developers to find the right balance between producing software and addressing detected vulnerabilities urgently. Invicti’s comprehensive and actionable reports help developers to tackle the most urgent detected issues first and hone their skills to produce software that is secure by design.

Reports list the severity level of each detected vulnerability along with its impact if exploited. They use Invicti’s unique Proof-Based Scanning technology to demonstrate how it was possible to exploit the vulnerability in a safe and read-only manner. Remediation information is supplied, including direct actions to take.

And, finally, reports list additional supporting information such as best practice, references, classifications and CVSS scores. This combination of technical information enables developers to determine the urgency for each vulnerability and get started on fixing it straight away.

In addition to these essential features, you can customize the reports you want to generate. The Invicti Standard edition also enables you to create Custom Reports and generate Custom Report Policies based on existing templates to suit your business needs. You can also replace the Invicti logo with your own.Now, let’s delve into some of the most commonly used report templates available in Invicti: Detailed Scan Reports, Executive Summary Reports, Comparison Reports, and Compliance Reports.
Detailed Scan Reports: Comprehensive and Easy to Understand
Invicti’s comprehensive technical reports are designed for those dealing with fixing vulnerabilities. Technical staff can employ them to easily grasp how Invicti has proved that the vulnerability can be exploited.To illustrate, technical reports such as the Detailed Scan Report provide a comprehensive security overview of the target web application. Written in a clear and accessible format, this report includes a summary that presents straightforward numerical and graphical information.

This report also includes a Vulnerability Summary, as illustrated, listing basic information about each detected vulnerable URL, categorized by severity.
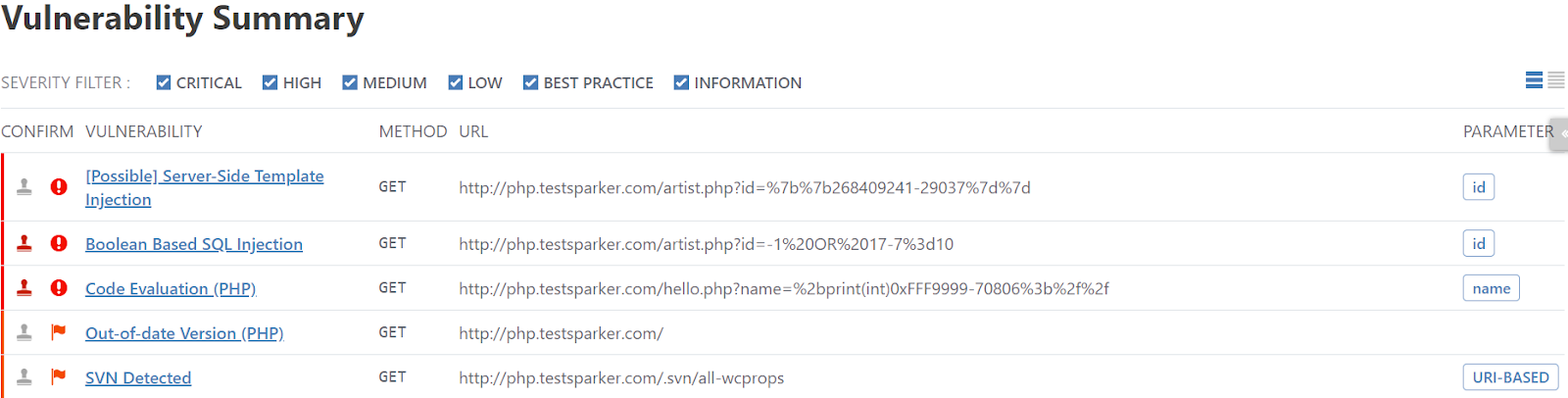
The bulk of the report are individual sections for the vulnerability names and technical details. Each section describes the impact of a vulnerability and explains the Proof of Exploit. This is in addition to the details outlined in the How Does Invicti Reporting Work? section above. Here is one example:

A technical report is comprehensive and rich in detail, allowing developers to attend to vulnerabilities immediately.
Executive Summary Reports: Concise Overviews for Management
An Executive Summary Report is produced following every web application security scan. It contains numerical and graphical information that presents an overall summary of the target web application’s security status. The format of this report allows less technical users to quickly see how many issues were detected and which need urgent attention. They can also see the business impact of the scan, and therefore prioritize and manage the required remediation work.

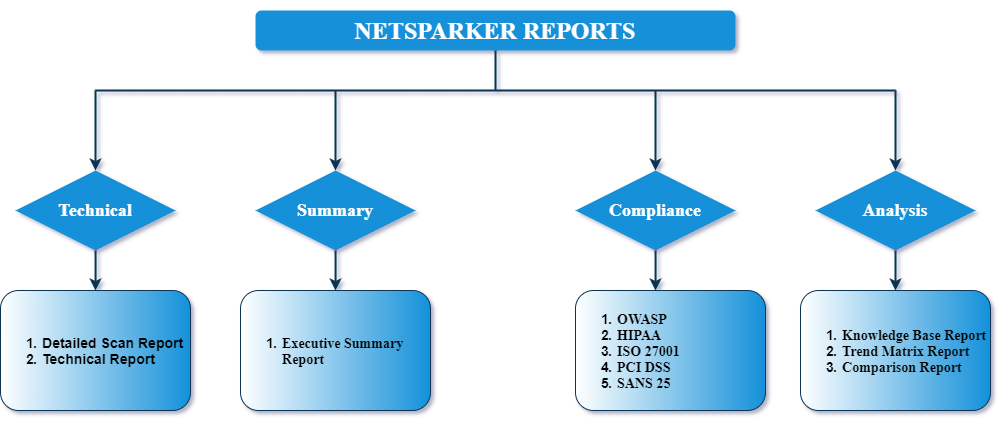
Compliance Reports Classify Vulnerabilities with Precision
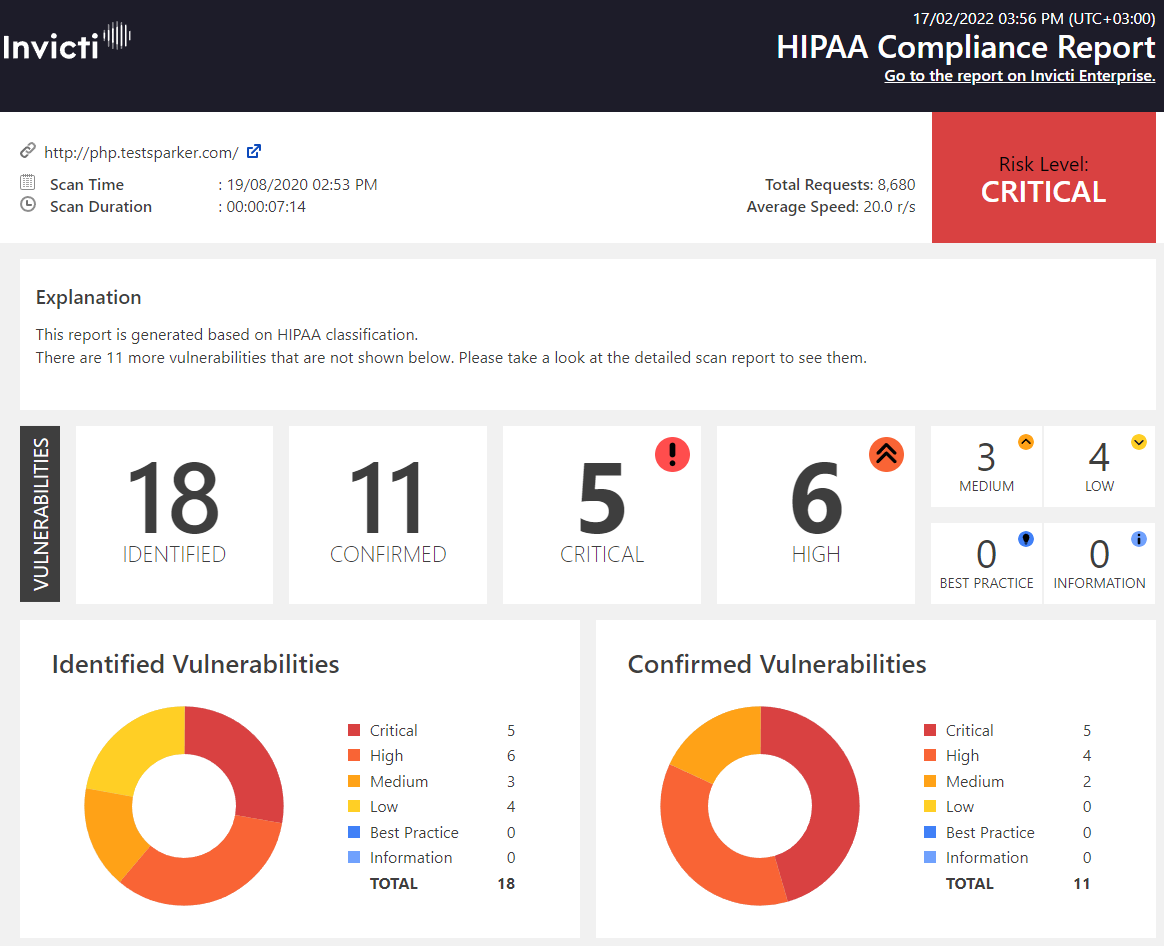
Invicti reports list vulnerabilities based on Vulnerability Severity Levels. If Invicti labels a vulnerability as critical, it lists it at the top. However, if you want to restrict the report to view only vulnerabilities that are based on specific classifications or compliance requirements, such as HIPAA, ISO 27001, OWASP, PCI DSS, and SANS, there is a series of reports among the Report Templates that enable you to do so.If your organisation processes identifiable health information, you are expected to abide by the US Health Insurance Portability and Accountability Act (HIPAA) standards.Here is an example of a HIPAA Compliance Report.
Likewise, you can generate the ISO 27001 Report to view issues that infringe this standard. In addition to breaking down vulnerabilities from a compliance viewpoint, these reports include all the relevant technical details you might expect to find in the Detailed Scan Report.The OWASP Top Ten 2017 Report is another example of a classification-style report. The OWASP Foundation has published and updated its vulnerability lists since 2003 to raise awareness for common vulnerabilities found in web applications. Similarly, if you want to see only the most dangerous software errors listed by SANS, you can generate the SANS Top 25 Report.Our final example in this category of reports is essential if your company processes credit or debit card payments. Such organisations are expected to comply with the Payment Card Industry Data Security Standard (PCI DSS) rules. Invicti can generate an unofficial PCI DSS Compliance Report based on a scan. If you need an official PCI DSS Report, you can generate it from Invicti Enterprise based on your scan results. By fixing vulnerabilities specified in these reports, you can work towards becoming PCI DSS compliant.Here is an example of a PCI DSS Compliance Report:
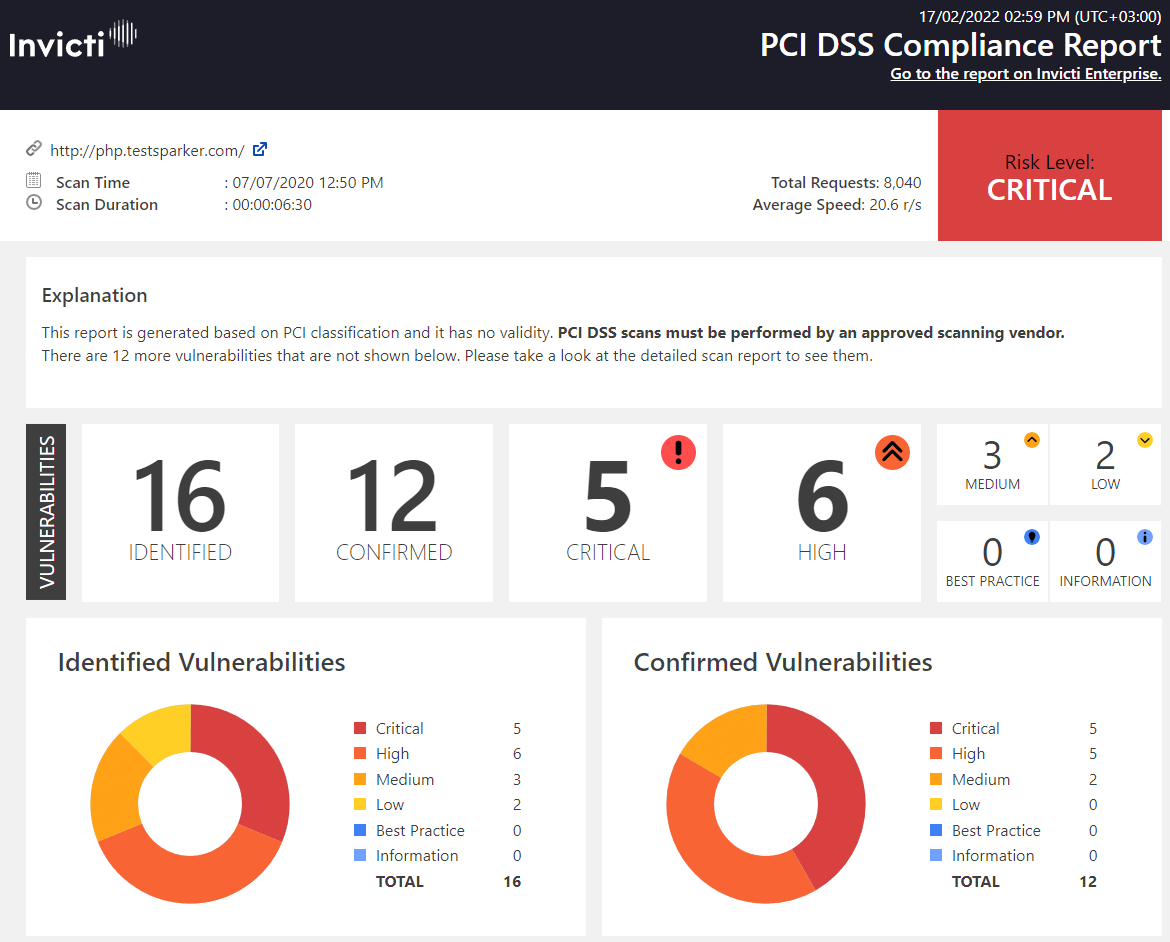
Knowledge Base Reports: Information About Additional Risk Factors
The Knowledge Base Report – unlike the Detailed Scan Report that developers rely on to list all vulnerabilities – lists additional information about the scan via a series of Knowledge Base Nodes. Reported issues include, for example, AJAX/XML HTTP Requests, CSS Files, External Scripts, Google Web Toolkit, Interesting Headers, and Web Pages With Inputs.
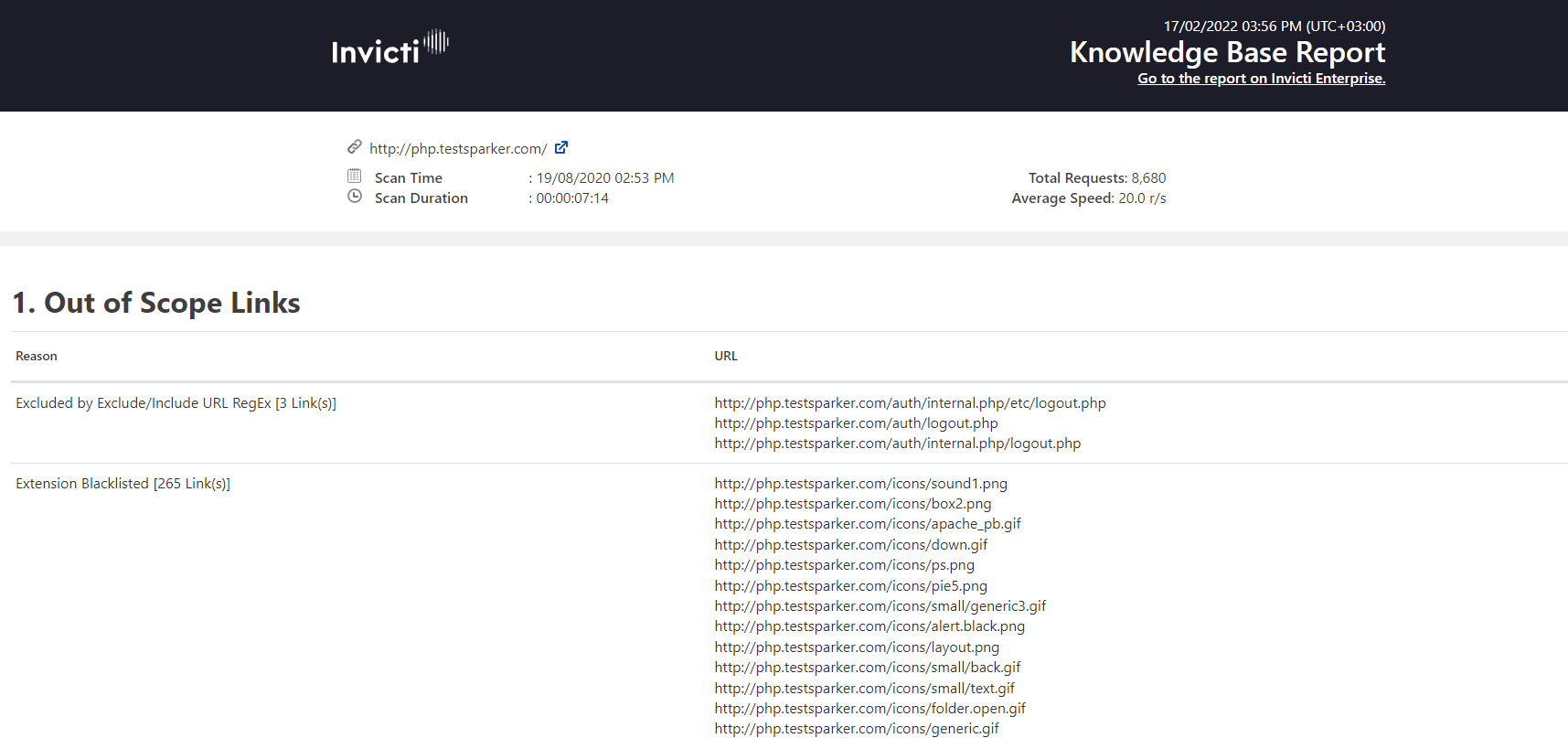
These issues are not classified as vulnerabilities, but they could still help malicious hackers to launch an attack.
Comparison Reports: Track Your Web Application’s Security Status
The Comparison Report, available in the Invicti Standard edition, can be used to monitor progress in fixing security vulnerabilities. If you run more than one scan on a target web application, you can subsequently use the Comparison Report feature in Invicti Standard to compare results and review progress. (In Invicti Enterprise, the Trend Matrix Report provides access to similar information.) In a quick, accessible format, you can see which vulnerabilities are fixed, new, revived, and not fixed. This report allows you to see the progress made in securing the web application over time.
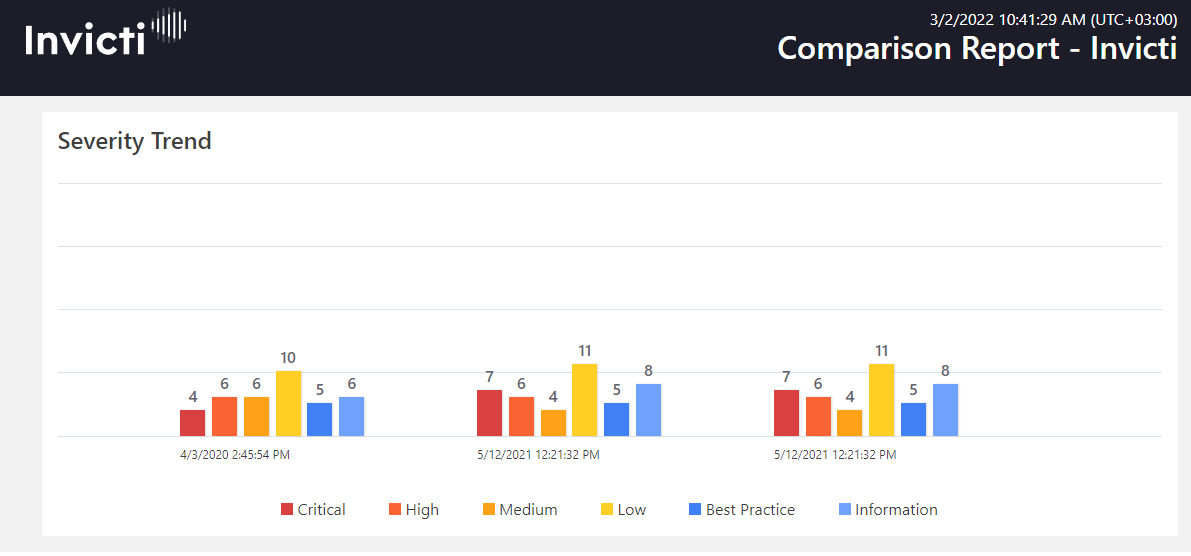
You can also run Statistical Reports in Invicti Enterprise for a website group or vulnerability across a specific date range. Like the Comparison Report, you can see how well your web application’s security status has progressed over time and how vulnerabilities have changed.Finally, you can combine the Comparison Report with the Executive Summary Report to illustrate the progress your team has made. Similarly, if you are a team supervisor and want to assess the team’s work or present its achievement to senior managers, these reports supply essential evidence.
Explore Invicti Reports Today
Invicti products are designed to arm you with powerful and comprehensive reports so that you and your team can quickly tackle issues and eliminate vulnerabilities. You can explore even further by running reports based on leading vulnerability lists such as OWASP, acting on non-vulnerability information, and check how your web application matches up to multiple compliance metrics. Invicti also provides the tools to allow managers and team leaders to monitor the team’s progress in fixing problems.Invicti opens up the security status of your web applications to give you insights into all relevant risk areas, including things you may never have considered – from unnecessary but minor risks to potentially disastrous vulnerabilities. This ensures that you are fully informed before implementing the final fixes and you can measurably improve the security posture of your web applications over time.For further information, see Overview of Reports and Report Templates.


